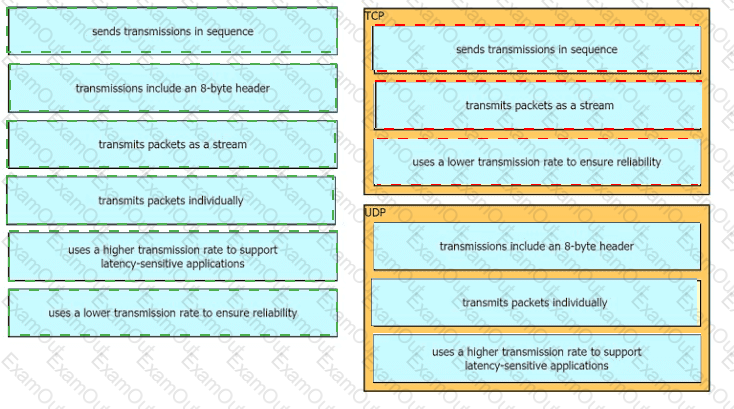
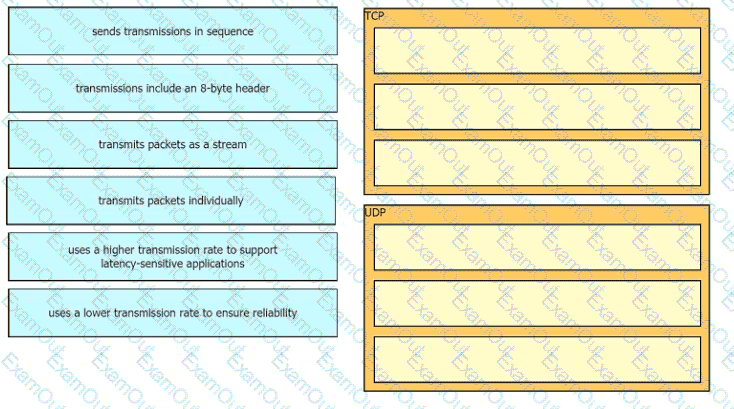
Drag the descriptions of IP protocol transmissions from the left onto the IP traffic types on the right.
Refer to the exhibit.
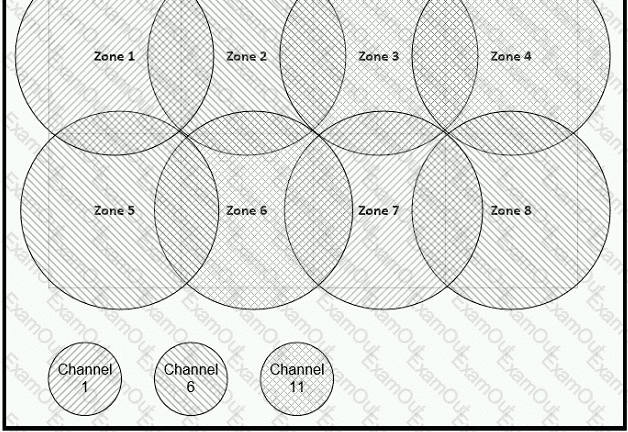
Between which zones do wireless users expect to experience intermittent connectivity?
How does the dynamically-learned MAC address feature function?
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
Refer to the exhibit.
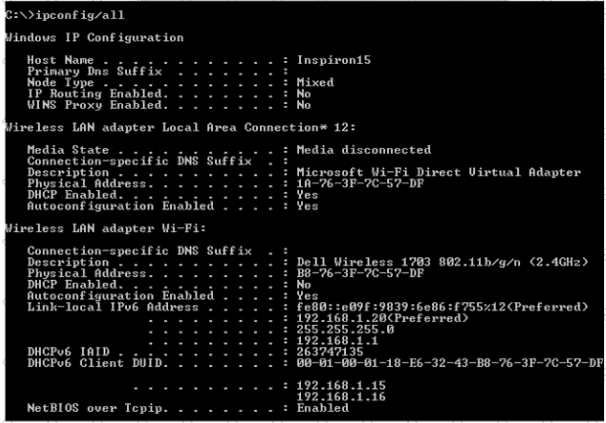
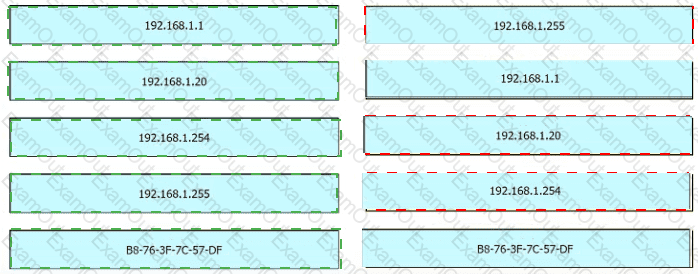
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.
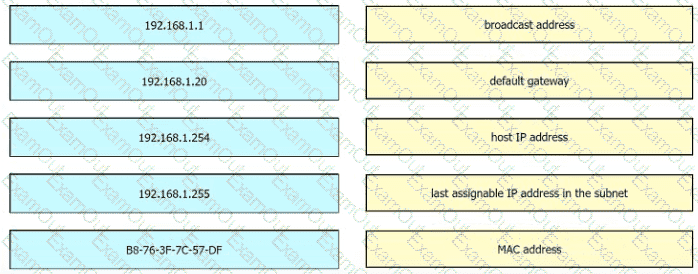
Refer to the exhibit.

Which route does R1 select for traffic that is destined to 192 168.16.2?
What makes Cisco DNA Center different from traditional network management applications and their management of networks?
Which function is performed by DHCP snooping?
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
How does WPA3 improve security?
Which communication interaction takes place when a southbound API Is used?
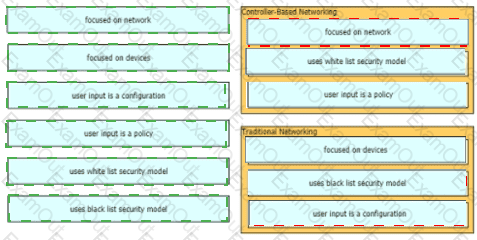
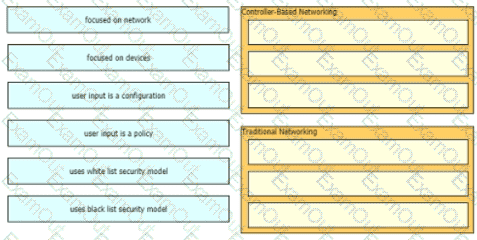
Drag and drop to the characteristics of networking from the left onto the correct networking types on the right.

Refer to the exhibit. After the configuration is applied, the two routers fail to establish an OSPF neighbor relationship. what is the reason for the problem?
What is the primary function of a Layer 3 device?
What are two characteristics of an SSID? (Choose Two)
Refer to the exhibit.
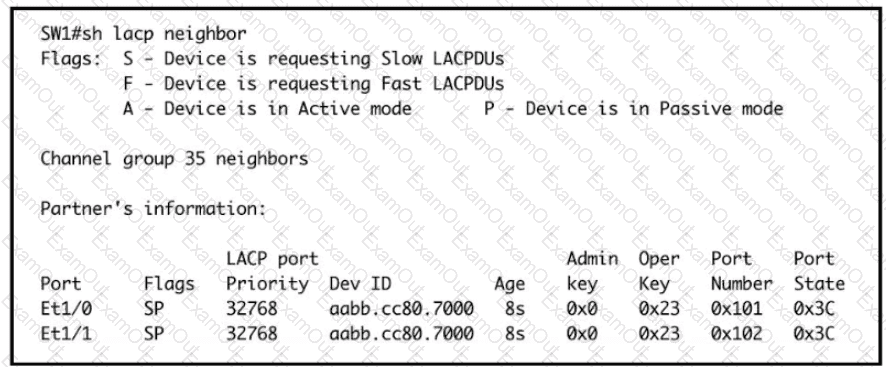
Based on the LACP neighbor status, in which mode is the SW1 port channel configured?
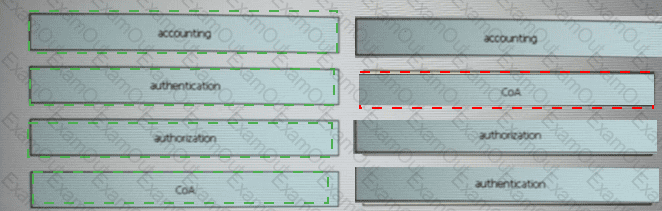
Drag and drop the AAA terms from the left onto the description on the right.

What does an SDN controller use as a communication protocol to relay forwarding changes to a southbound API?
Refer to the exhibit.
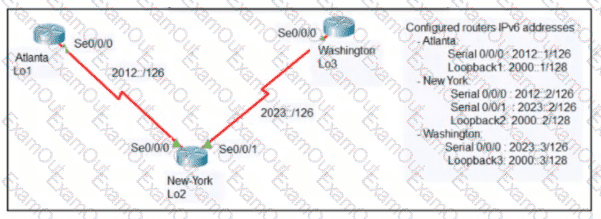
An engineer configured the New York router with state routes that point to the Atlanta and Washington sites. When command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
What is a function of TFTP in network operations?