A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
Which type of organization should use a collapsed-core architecture?
What are two reasons for an engineer to configure a floating state route? (Choose two)
Where does wireless authentication happen?
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
Which WPA3 enhancement protects against hackers viewing traffic on the Wi-Fi network?
Refer to the exhibit.
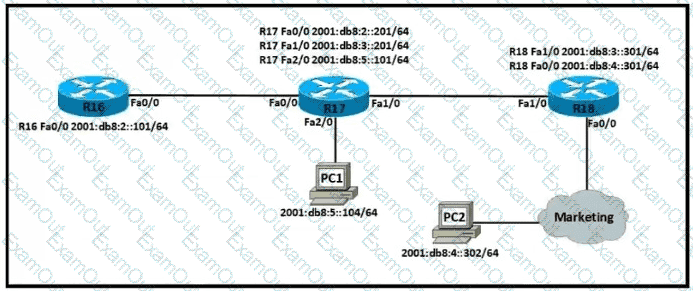
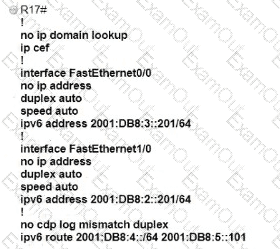
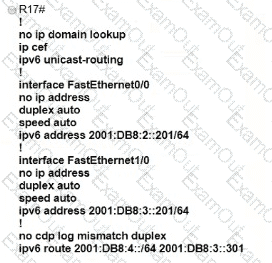
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A)
B)
C)

D)
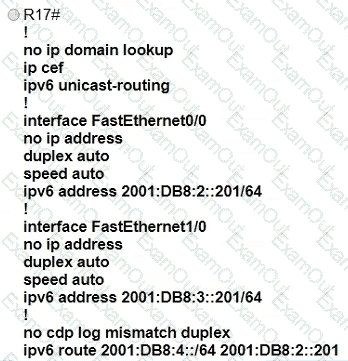
Refer the exhibit.
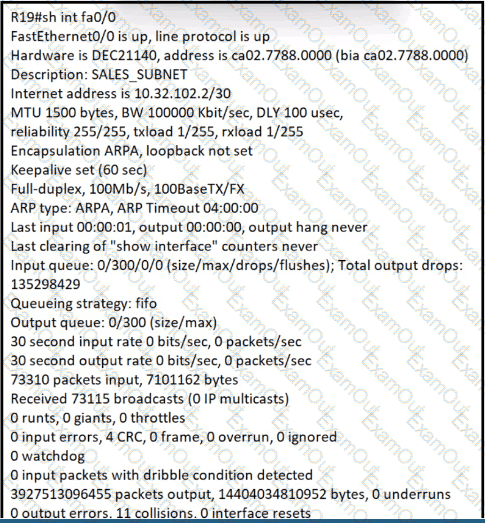
What is the cause of poor performance on router R19?
What is the put method within HTTP?
Which group of channels in the 802.11b/g/n/ax 2.4 GHz frequency bands are non-overlapping channels?
Refer to the exhibit.
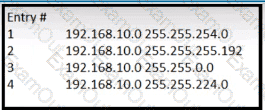
Which entry is the longest prefix match for host IP address 192.168.10.5?
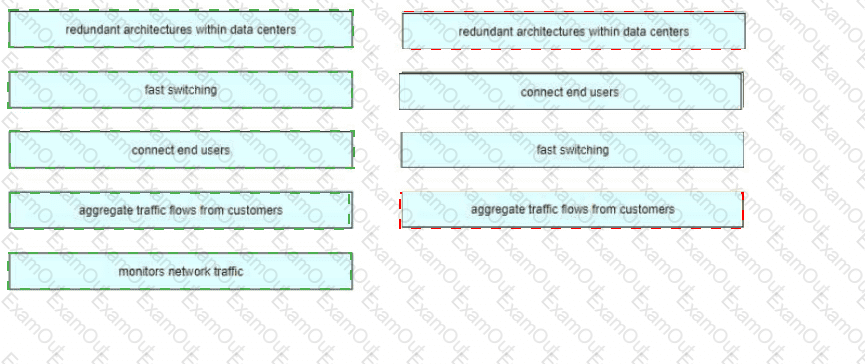
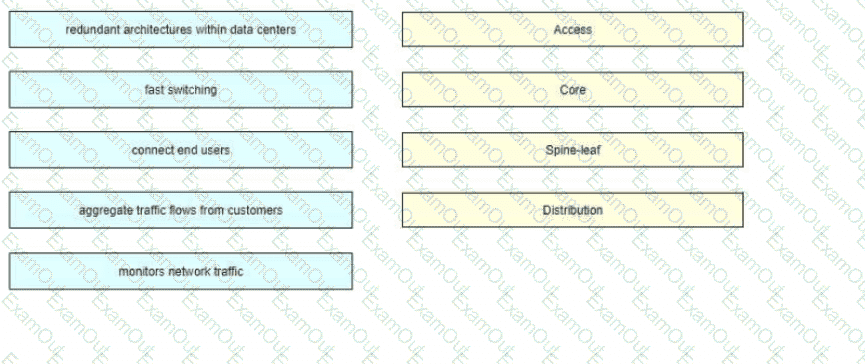
Drag and drop the common functions from the left onto the cofresponding network topology architecture layer on the right. Not all common functions are used.
Which protocol is implemented when an organization must verify network performance, troubleshoot issues, and use an agent to communicate between monitoring tools and end devices?
Refer to the exhibit.
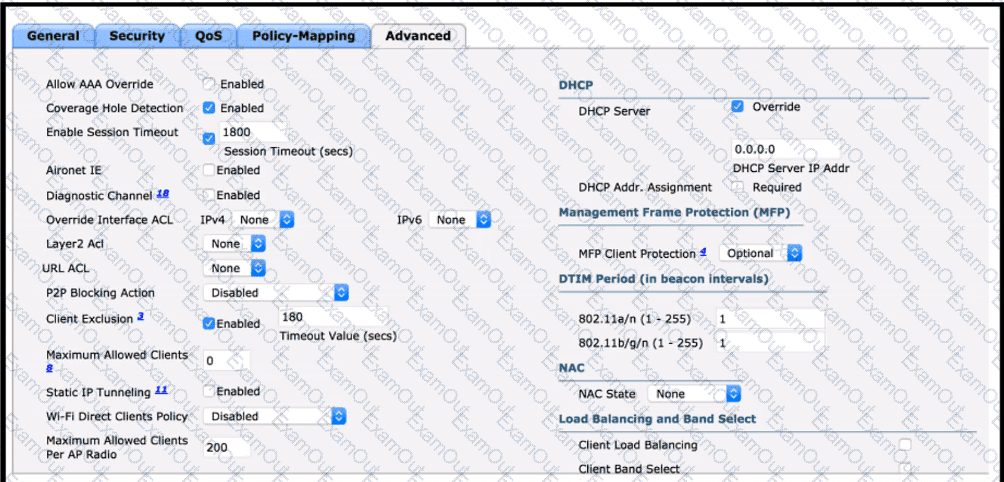
The P2P blocking action option is disabled on the WLC.
Why would VRRP be implemented when configuring a new subnet in a multivendor environment?
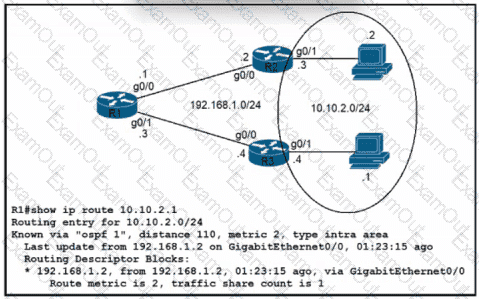
Refer to the exhibit. Traffic from R1 to the 10.10.2.0/24 subnet uses 192.168.1.2 as its next hop. A network engineer wants to update the R1 configuration so that traffic with destination 10.10.2.1 passes through router R3, and all other traffic to the 10.10.2.0/24 subnet passes through R2.
Which command must be used?
The address block 192.168.32.0/24 must be subnetted into smaller networks. The engineer must meet these requirements:
Create 8 new subnets
Each subnet must accommodate 30 hosts
Interface VLAN 10 must use the last usable IP in the first new subnet.
A Layer 3 interface is used.
Which configuration must be applied to the interface?
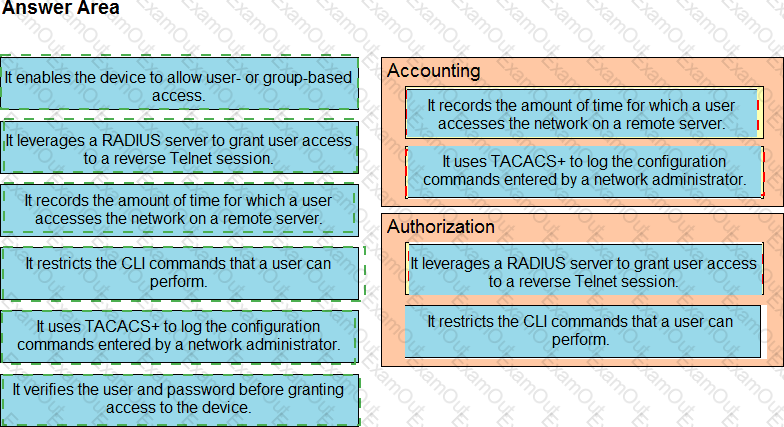
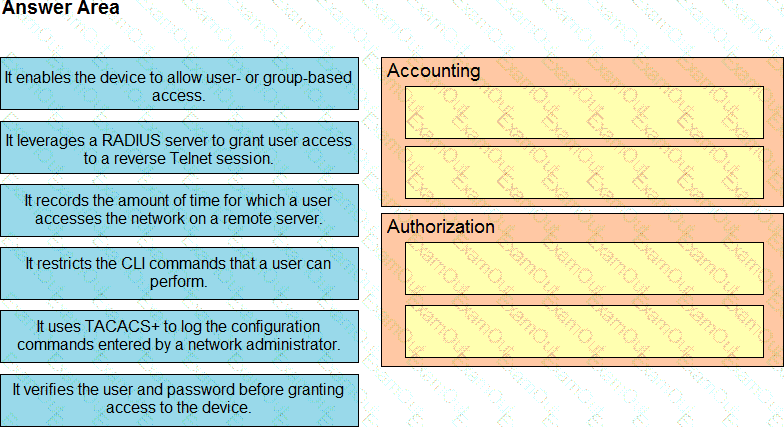
Drag and drop the AAA features from the left onto the corresponding AAA security services on the right. Not all options are used.
Which interface enables communication between a program on the controller and a program on the networking devices?
Refer to the exhibit.
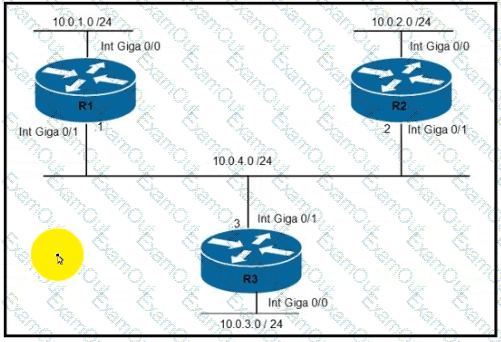
Router R1 must be configured to reach the 10.0.3.0/24 network from the 10.0.1.0/24 segment.
Which command must be used to configure the route?