A)
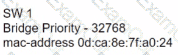
B)
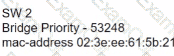
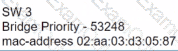
C)

D)
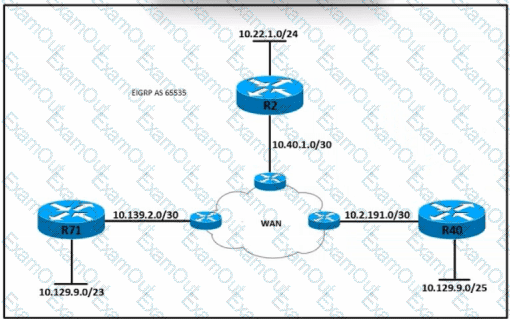
Refer to the exhibit. All routers in the network are configured conrectly, and the expected routes are being exchanged among the routers. Which set of routes are leamed from neighbors and installed on router 2?
What are two facts that differentiate optical fiber cabling from copper cabling? (Choose two.)
Which Cisco proprietary protocol ensures traffic recovers immediately, transparently, and automatically when edge devices or access circuits fail?
Which functionality is provided by the console connection on a Cisco WLC?
Which two protocols are used by an administrator for authentication and configuration on access points?
Refer to the exhibit.
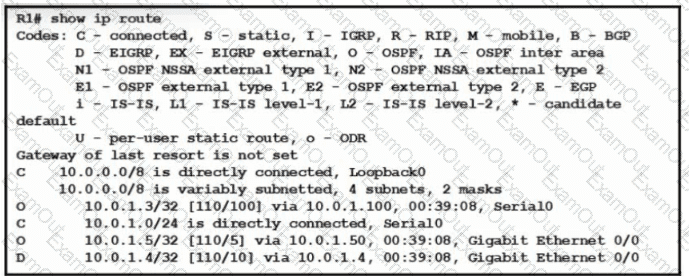
What does route 10.0.1.3/32 represent in the routing table?
What is a function of Cisco Advanced Malware Protection for a Next-Generation IPS?
A client experiences slow throughput from a server that is directly connected to the core switch in a data center. A network engineer finds minimal latency on connections to the server, but data transfers are unreliable, and the output of the show Interfaces counters errors command shows a high FCS-Err count on the interface that is connected to the server. What is the cause of the throughput issue?
Which protocol does Ansible use to push modules to nodes in a network?
Which interface is used for out-of-band management on a WLC?
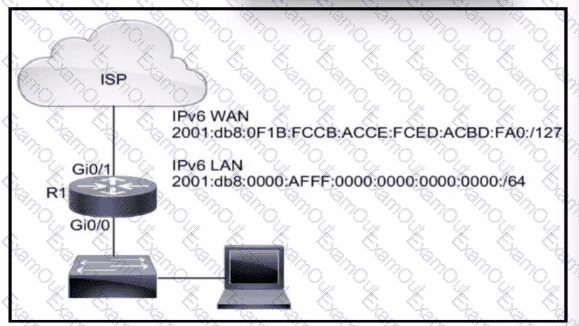
Refer to the exhibit. IPv6 must be implemented on R1 to the ISP The uplink between R1 and the ISP must be configured with a manual assignment, and the LAN interface must be self-provisioned Both connections must use the applicable IPv6 networks Which two configurations must be applied to R1? (Choose two.)
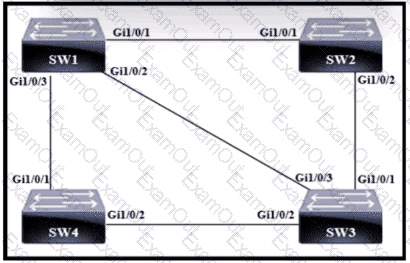
Refer to the exhibit.
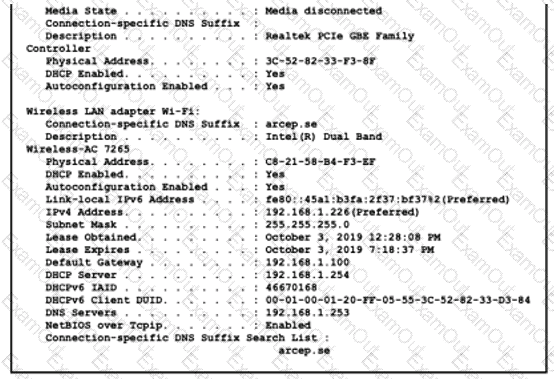
The given Windows PC is requesting the IP address of the host at www.cisco.com. To which IP address is the request sent?
Which type of port is used to connect lo the wired network when an autonomous AP maps two VLANs to its WLANs?
Refer to the exhibit.
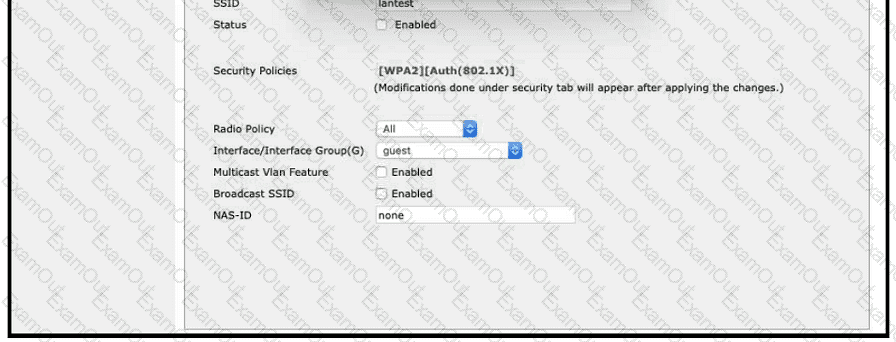
A Cisco engineer creates a new WLAN called lantest. Which two actions must be performed so that only high-speed 2.4-Ghz clients connect? (Choose two.)
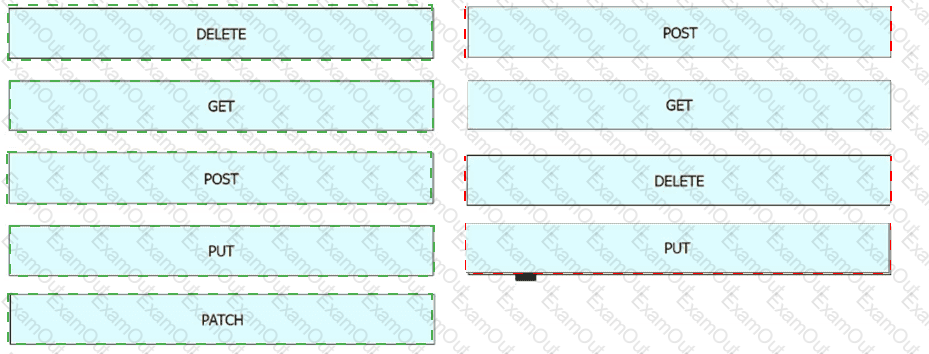
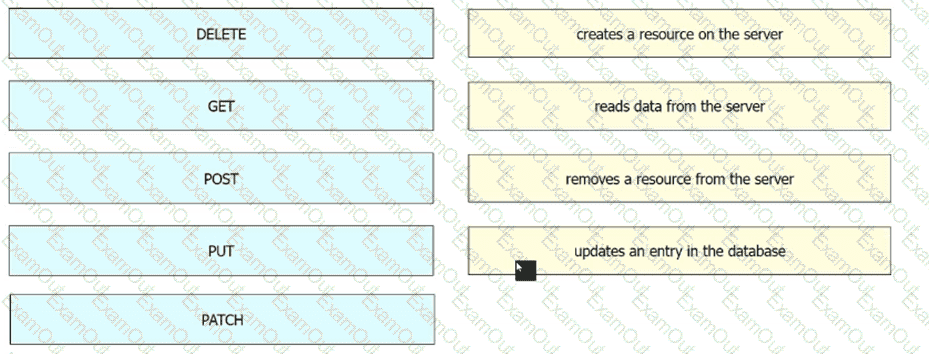
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.
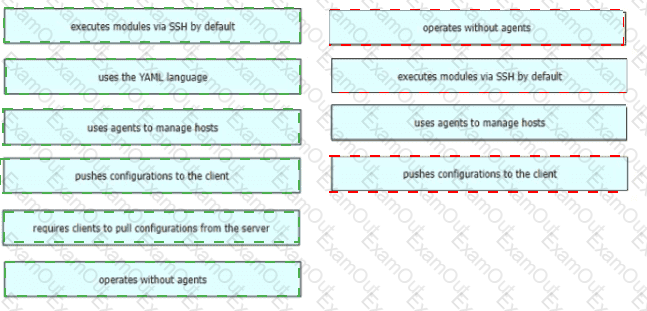
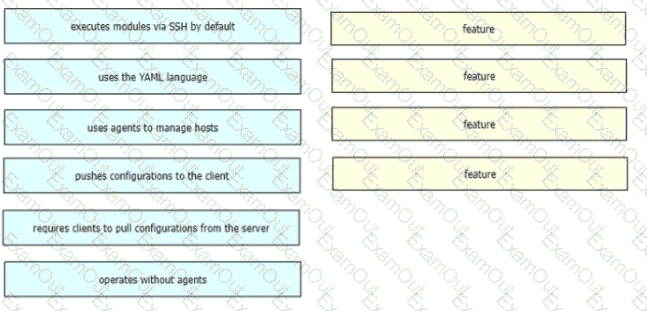
Drag and drop the Ansible features from the left to the right Not all features are used.
A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied, the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583B. Which command must be issued on the interface?
Which IPsec transport mode encrypts the IP header and the payload?
What are two characteristics of a controller-based network? (Choose two.)