Exhibit.
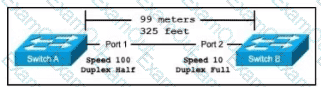
The switches are connected via a Cat5 Ethernet cable that was successfully tested. The Interfaces are configured as access ports and are both in a 'down" status. What is the cause of this issue?
Which two statements distinguish authentication from accounting? (Choose two.)
Refer to the exhibit.
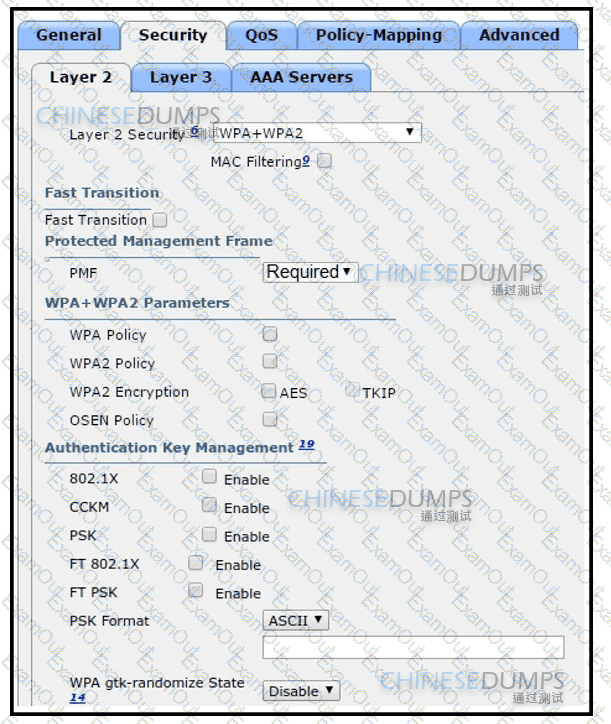
The network engineer is configuring a new WLAN and is told to use a setup password for authentication instead of the RADIUS servers. Which additional set of tasks must the engineer perform to complete the configuration?
Which AP mode serves as the primary hub in a point-to-multipoint network topology.
Refer to the exhibit.
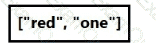
Which type of JSON data is represented?
Which CRUD operation corresponds to me HTTP GET method?
What are two reasons a switch experiences frame flooding? (Choose two.)
What is the purpose of configuring different levels of syslog for different devices on the network?
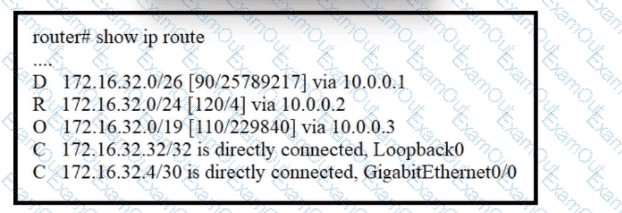
Refer to the exhibit. A packet sourced from 172.16.32.254 is destined for 172.16.32.8. What is the subnet mask of the preferred destination route?
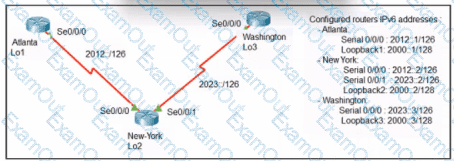
Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the Lo2 interface on the New York router?
Refer to the exhibit.
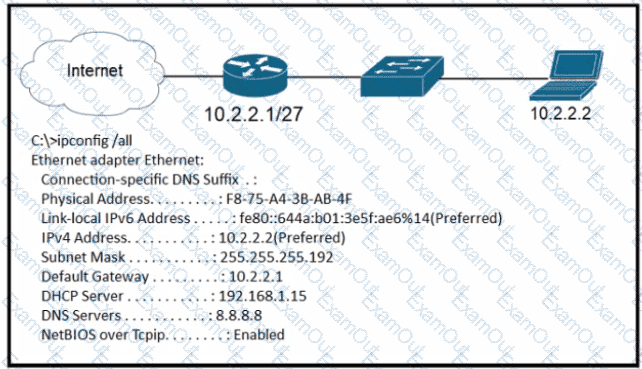
A newly configured PC fails to connect to the internet using TCP port 80 to www cisco com Which setting must be modified for the connection to work?
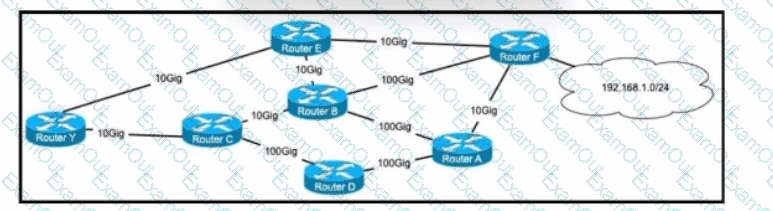
Refer to the exhibit. With a reference bandwidth of 100 Gb on all routers, which path does router Y use to get to network 192.168.1.0/24?
Refer to the exhibit.
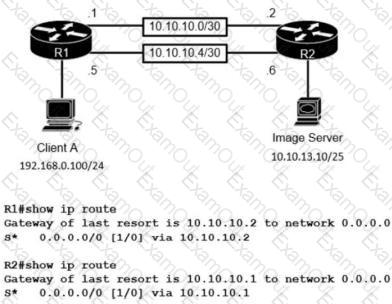
The image server and client A are running an application that transfers an extremely high volume of data between the two. An engineer is configuring a dedicated circuit between R1 and R2. Which set of commands must the engineer apply to the routers so that only traffic between the image server and client A is forces to use the new circuit?
An engineer must configure a core router with a floating static default route to the backup router at 10.200.0.2. Which command meets the requirements?
Which device separates networks by security domains?
Refer to the exhibit.
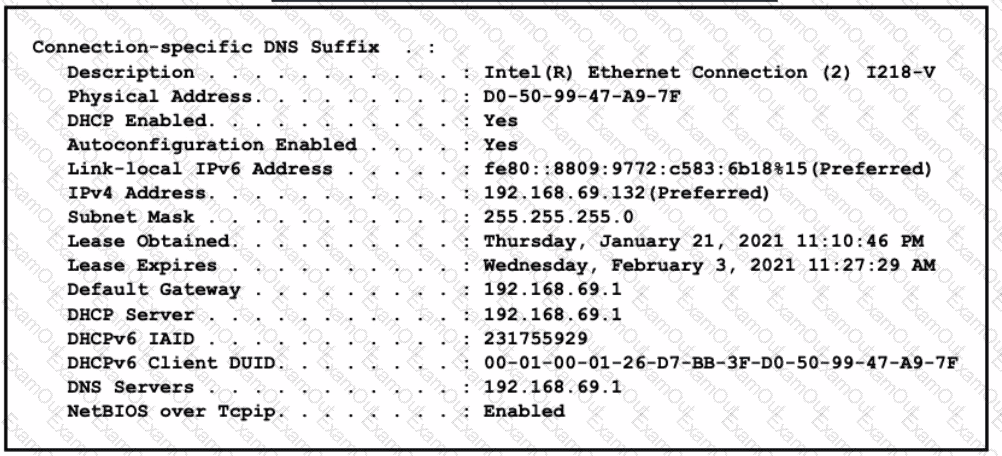
What does the host do when using the IPv4 Preferred function?
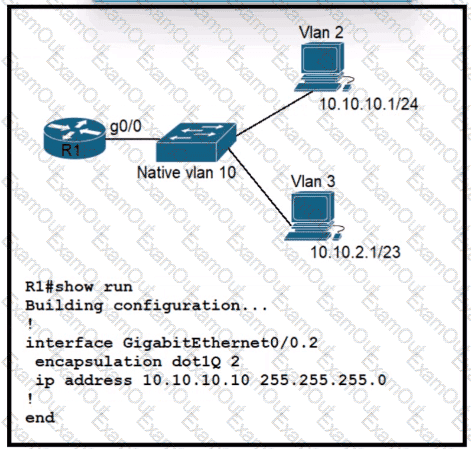
A)

B)

C)

D)


Refer to the exhibit. Which type of JSON data is shown?
What is the role of nonoverlapping channels in a wireless environment?
Refer to the exhibit.

A network engineer must configure NETCONF. After creating the configuration, the engineer gets output from the command show line but not from show running- config. Which command completes the configuration?

