Refer to the exhibit.
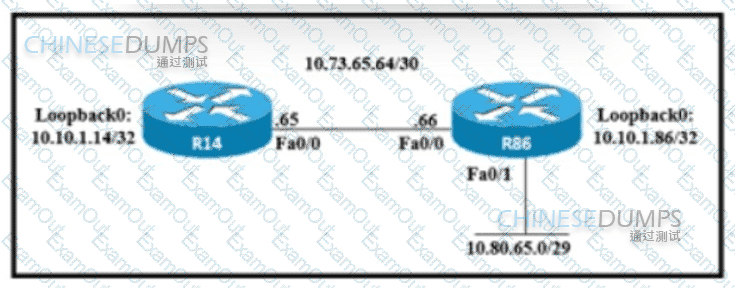
An engineer must configure a floating static route on an external EIGRP network. The destination subnet is the /29 on the LAN Interface of R86. Which command must be executed on R14?
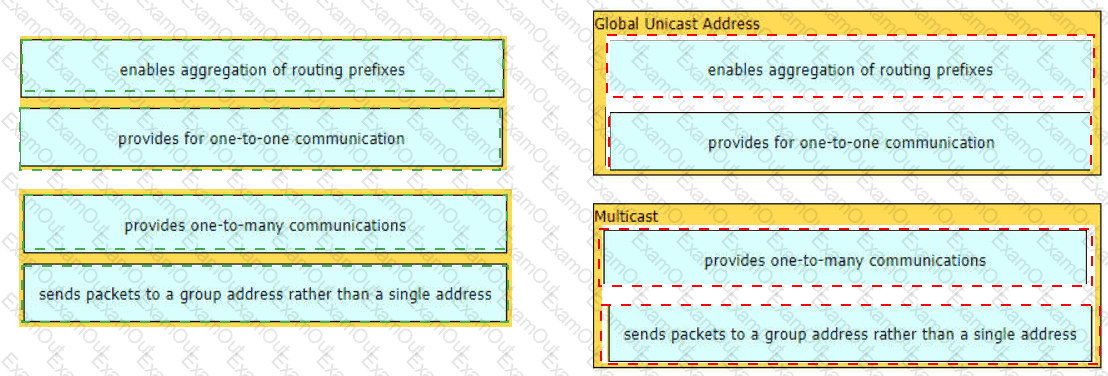
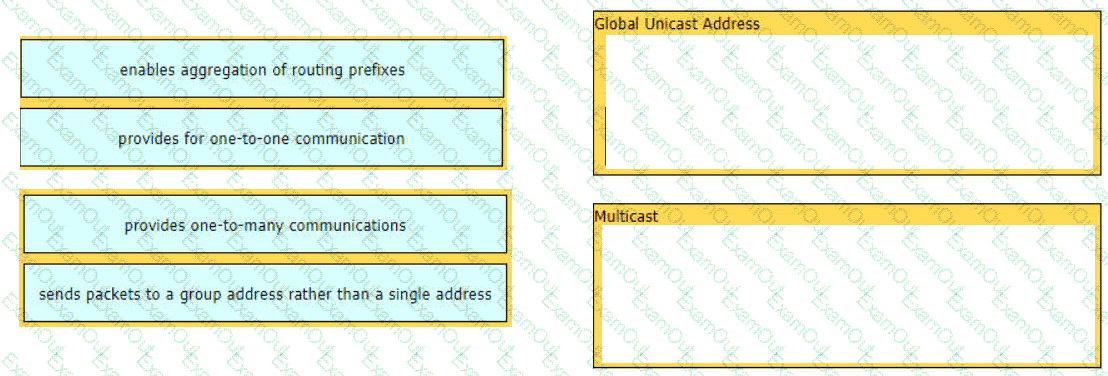
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Refer to the exhibit.
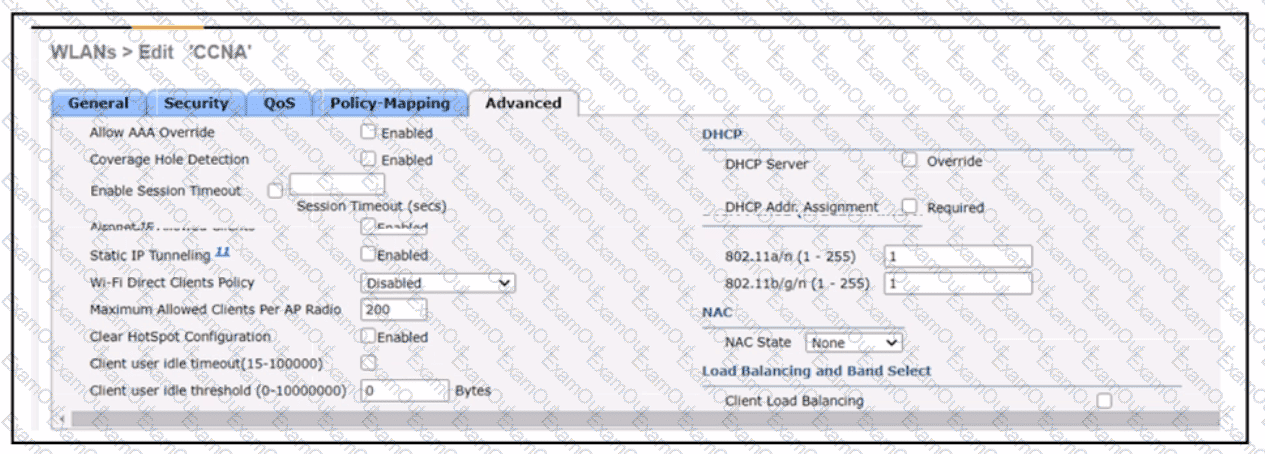
A network engineer configures the CCNA WLAN so that clients must authenticate hourly and to limit the number of simultaneous connections to the WLAN to Which two actions complete this configuration? (Choose two.)
What are two protocols within the IPsec suite? (Choose two)
What is a zero-day exploit?
What differentiates the Cisco OfficeExtend AP mode from FlexConnect AP mode?
Refer to the exhibit.
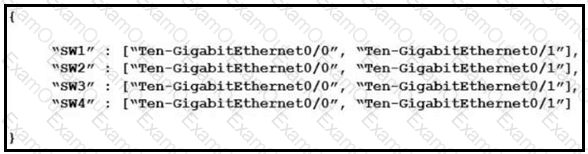
How many JSON objects are presented?
Refer to the exhibit.
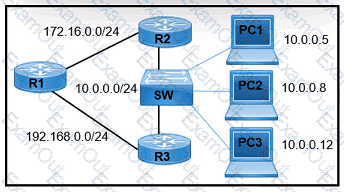
A network engineer must configure R1 so that it sends all packets destined to the 10.0.0.0/24 network to R3, and all packets destined to PCI to R2. Which configuration must the engineer implement?
A)
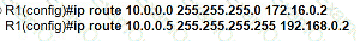
B)
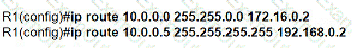
C)
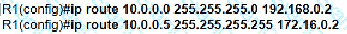
D)
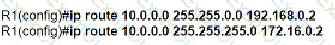
Which Windows command is used instead of the route print command to display the contents of the IP routing table?
Refer to the exhibit.
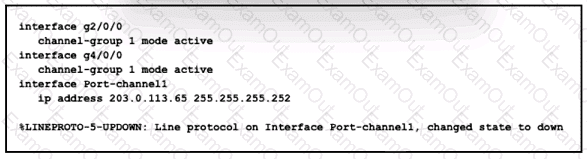
An engineer is configuring a Layer 3 port-channel interface with LACP. The configuration on the first device is complete, and it is verified that both interfaces have registered the neighbor device in the CDP table. Which task on the neighbor device enables the new port channel to come up without negotiating the channel?
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0.0.0.0.0:ffff:a36:4901, which prefix length must be used?
What is a characteristic of RSA?
Refer to the exhibit.
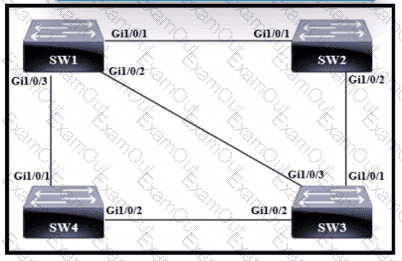
Which switch becomes the root bridge?
A)

B)
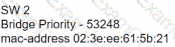
C)
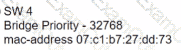
D)

What is a function of an endpoint?
A Cisco engineer notices thai two OSPF neighbors are connected using a crossover Ethernet cable. The neighbors are taking too long to become fully adjacent. Which command must be issued under the interface configuration on each router to reduce the time required for the adjacency to reach the FULL state?
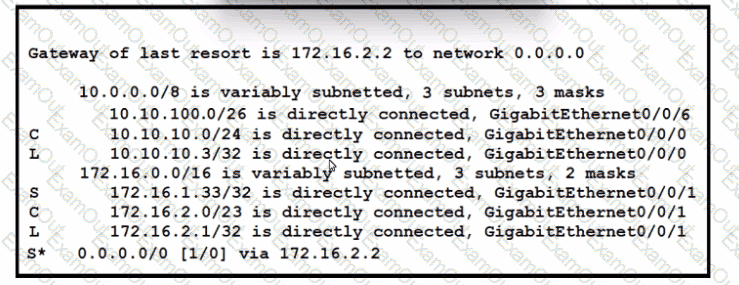
Refer to the exhibit. A packet sourced from 10.10.10.32 is destined for the Internet. What is the administrative distance for the destination route?
Which feature, when used on a WLC, allows it to bundle its distribution system ports into one 802.3ad group?
How does MAC learning function?
Which role do predictive Al models play in network load balancing?
What are two benefits of private IPv4 addressing? (Choose two.)