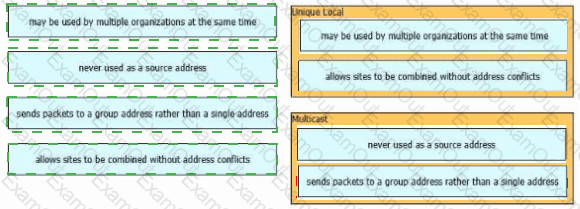
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
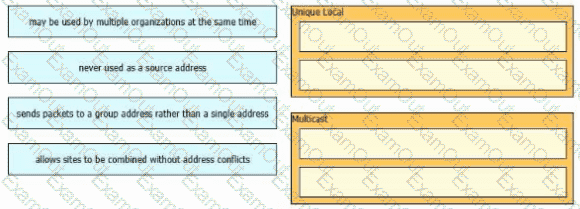
What is represented by the word "switch" within this JSON schema?
Which interface condition is occurring in this output?

Which interface is used to send traffic to the destination network?
10.90.207.87/26 [110/1912] via F0/7
10.90.207.87/26 [110/28968] via F0/6
10.90.207.87/26 [120/14] via F0/4
10.90.207.87/26 [120/11] via F0/5
How does MAC learning function?
Which statement describes virtualization on containers?
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
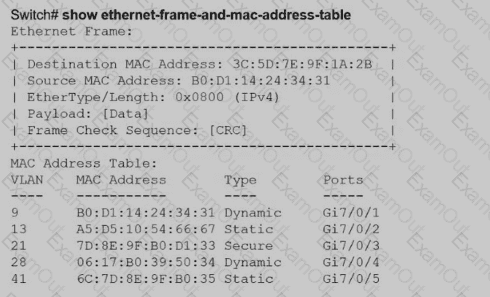
How does the switch handle the frame?
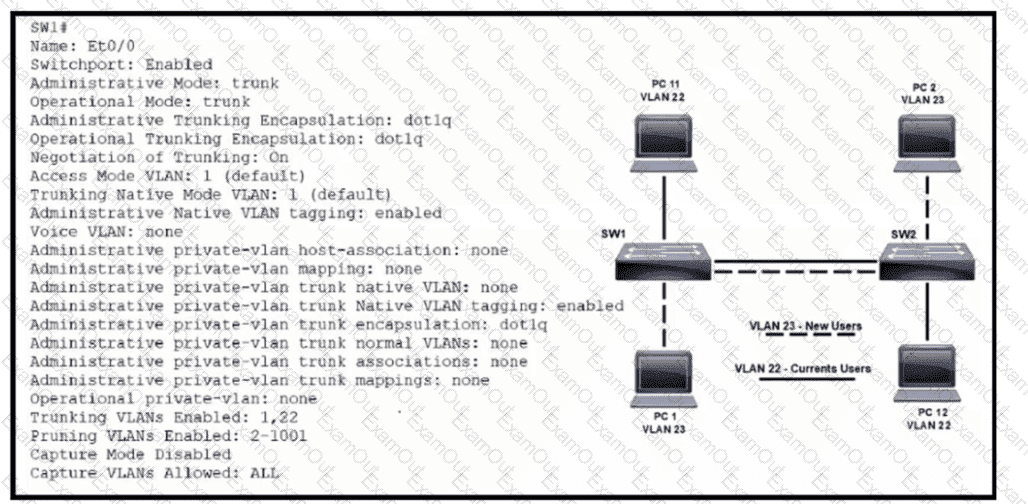
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
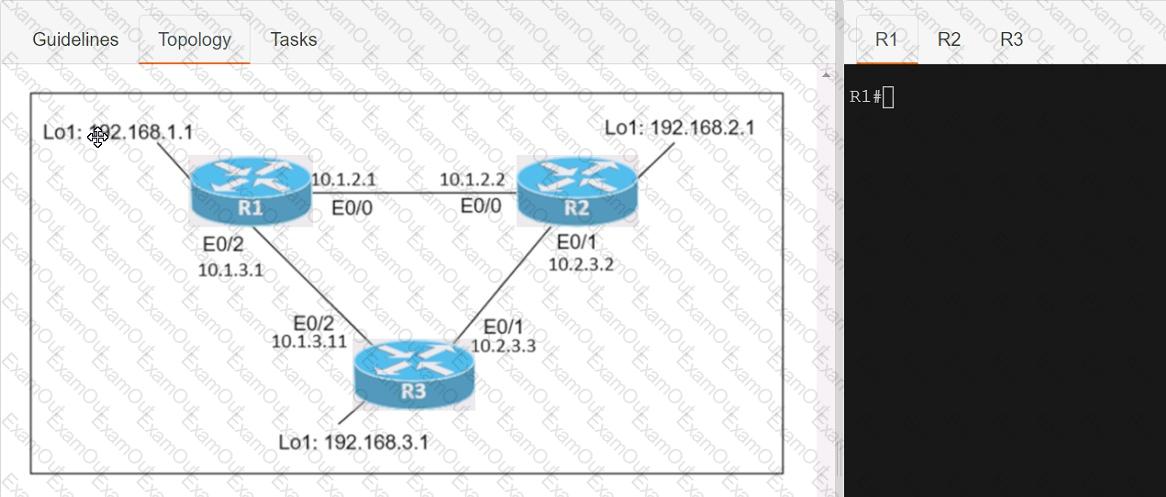
Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
How does automation leverage data models to reduce the operational complexity of a managed network?
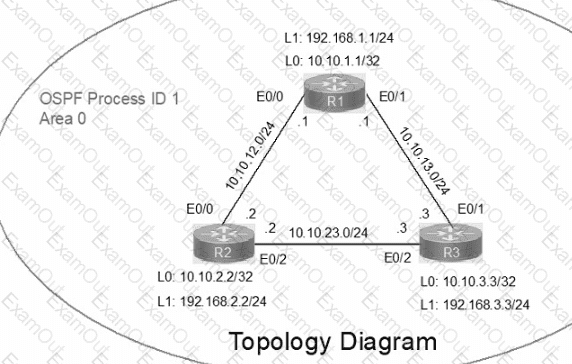
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
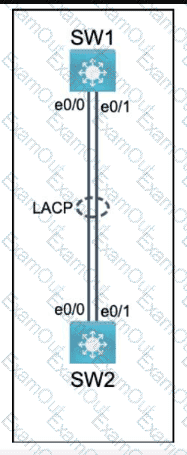
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
What is a function of a northbound API in an SDN environment?
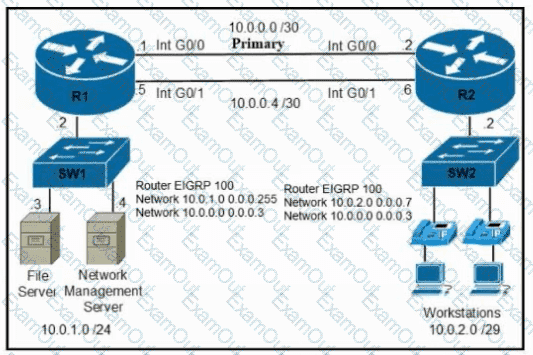
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
What is the maximum length of characters used in an SSID?
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
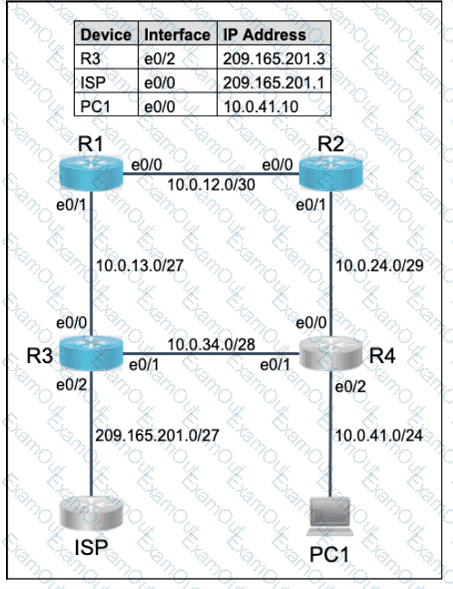
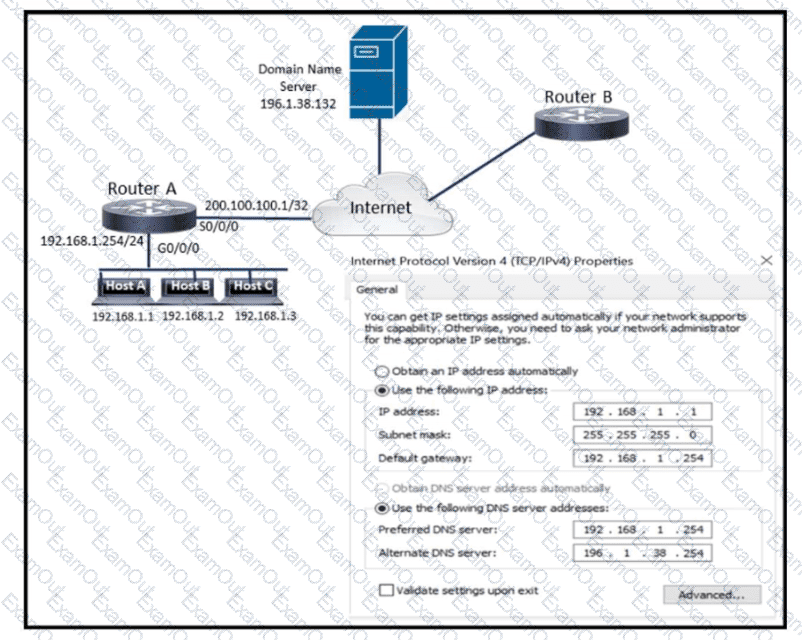
Refer to the exhibit. What is preventing host A from reaching the internet?
Which technology allows for logical Layer 3 separation on physical network equipment?
How does automation affect network management processes?