Why would a network administrator choose to implement RFC 1918 address space?
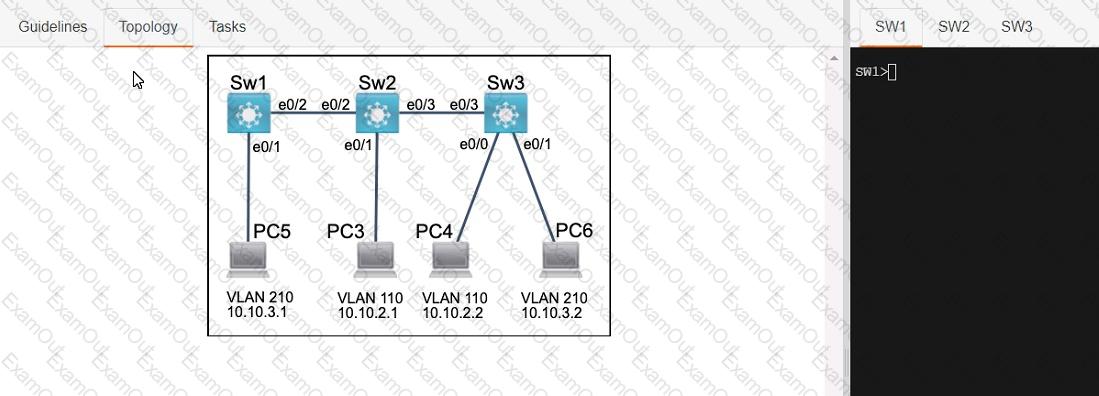
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
What differentiates the TCP and UDP protocols?
How is Al used to identify issues within network traffic?
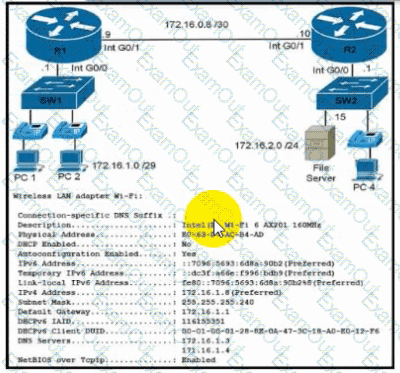
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?
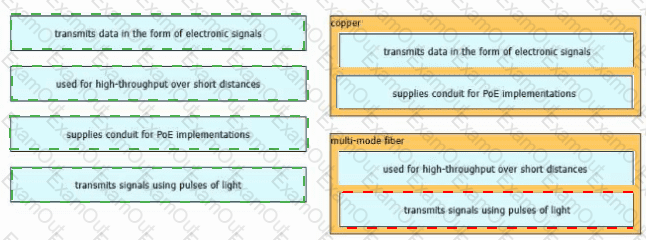
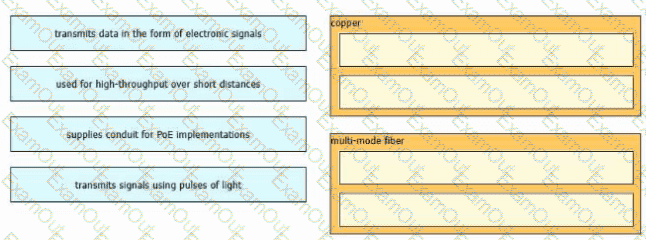
Drag and drop the characteristic from the left onto the cable type on the right.
What is a characteristic of a Layer 2 switch?
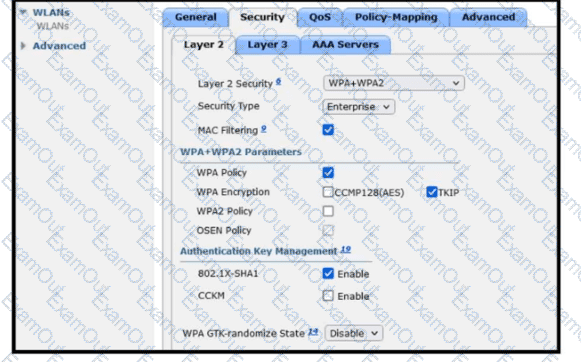
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
An engineer must update the configuration on two PCs in two different subnets to communicate locally with each other. One PC is configured with IP address 192.168.25.128/25 and the other with 192.168.25.100/25. Which network mask must the engineer configure on both PCs to enable the communication?
What is the purpose of the service-set identifier?
An engineer requires a switch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
Which interface is used to send traffic to the destination network?
O 10.76.170 161/26 |110/102] via FO/17
O 10.76.170 161/26[110/27e31] via FO/20
R 10.76.170.161/261120/15] via FO/8
R 10.76.170.161/26 [120/10] via FO/12
What is the function of generative AI in network operations?
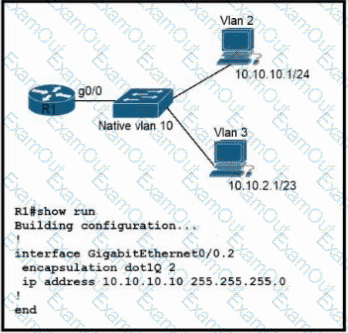
Refer to the exhibit. Configurations for the switch and PCs are complete.
Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
How does a network administrator securely manage an AP in lightweight mode?
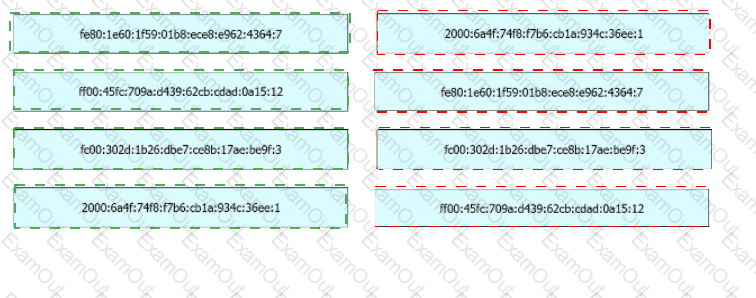
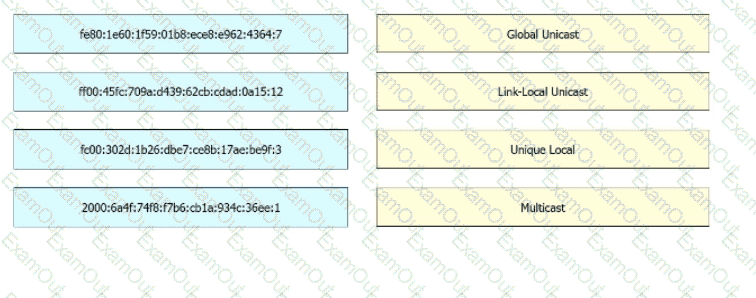
Drag and drop the IPv6 address from the left onto the type on the right.
Why would a network administrator implement the HSRP protocol?
Which interface on the WLC is used exclusively as a DHCP relay?
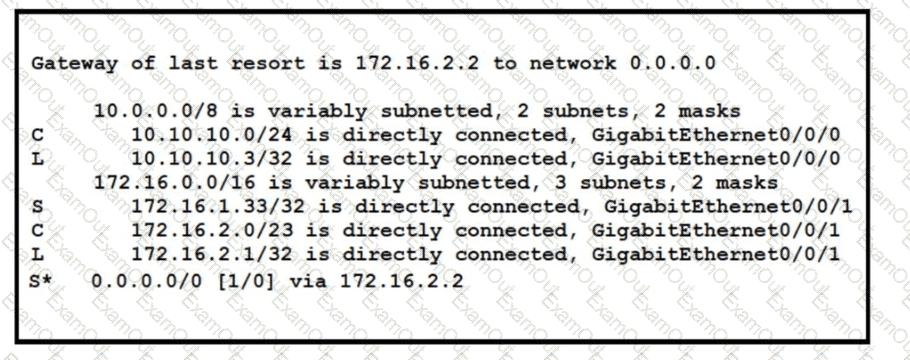
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?