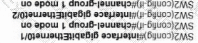An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 10.30.0.1?
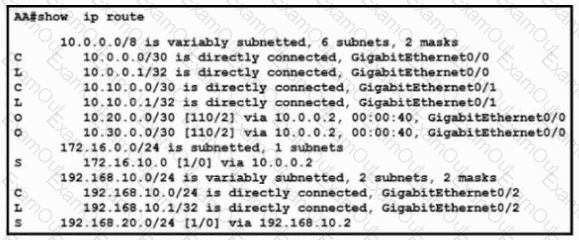
Refer to the exhibit. The route for 10.220.100.96/27 has been very unstable. The same route has four backups to routers A, B, C, and D via the respective methods. The routing protocol defaults for router Y have not been changed. When the current route for 10.220.100.96/27 becomes unavailable, which router will router Y use to route traffic to 10.220.100.96/27?
Why are API keys used to enforce rate limiting?
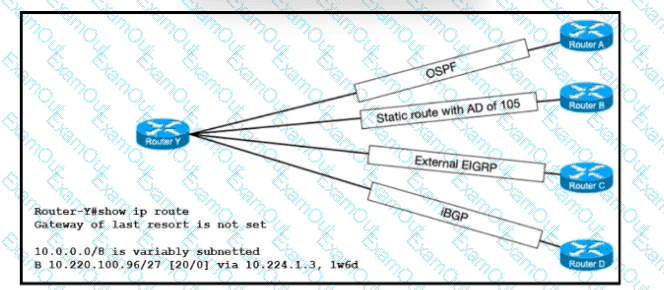
Refer to the exhibit. An administrator is configuring a new WLAN for a wireless network that has these requirements:
Dual-band clients that connect to the WLAN must be directed to the 5-GHz spectrum.
Wireless clients on this WLAN must be able to apply VLAN settings from RADIUS attributes.
Which two actions meet these requirements? (Choose two.)
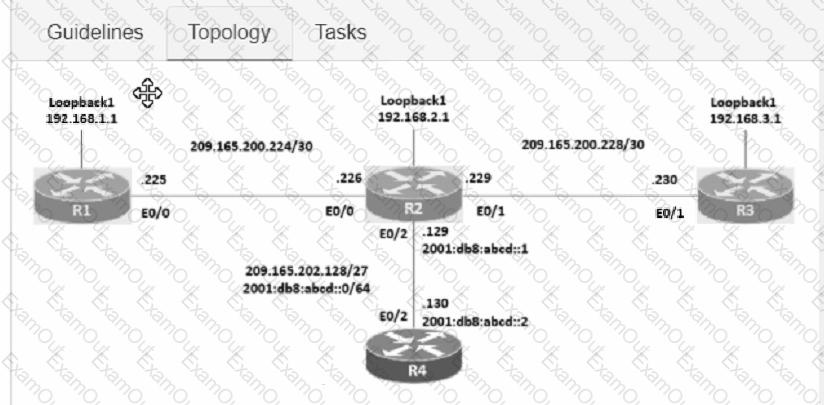
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
Which key function is provided by the data plane?
Where are the real-time control functions processed in a split MAC architecture?
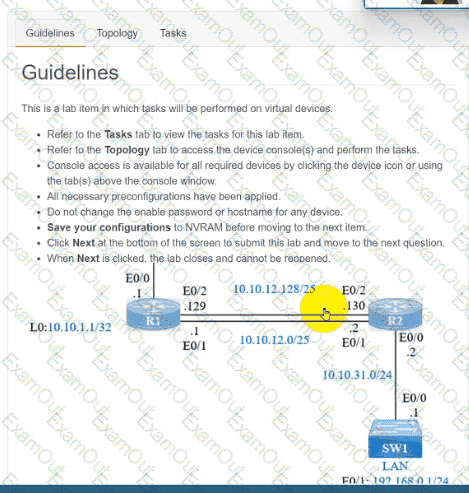
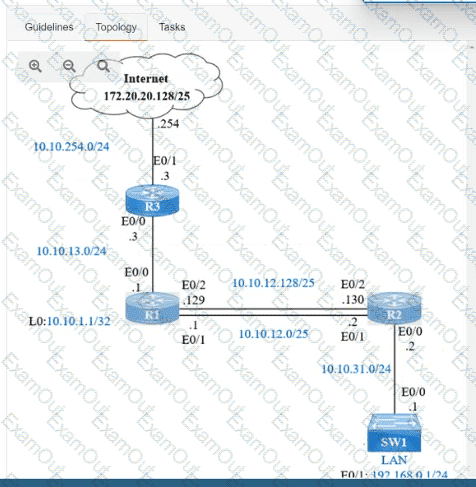
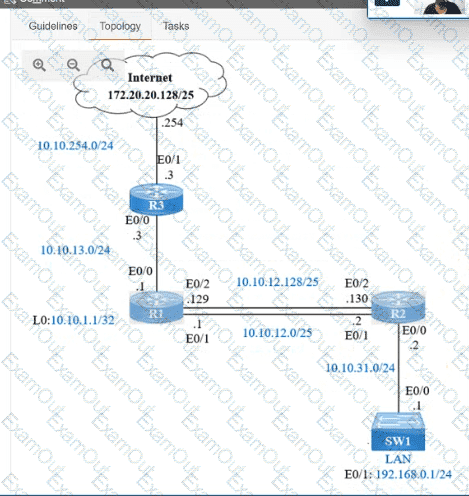
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
What is the total number of users permitted to simultaneously browse the controller management pages when using the AireOS GUI?
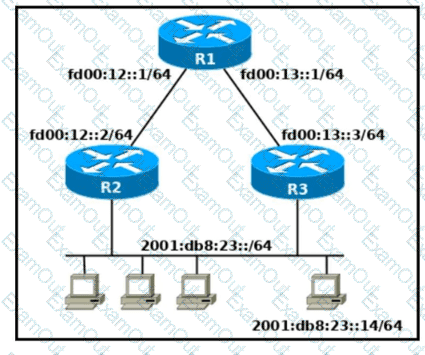
Refer to the exhibit. Which two commands, when configured on router R1. fulfill these requirements? (Choose two.) ' Packets toward the entire network 2001:db8:23: :/64 must be forwarded through router R2. ' Packets toward host 2001: db8:23::14 preferably must be forwarded through R3.
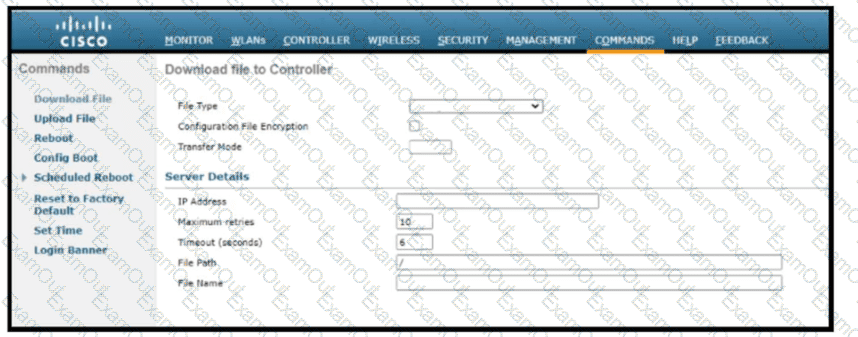
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
Refer to the exhibit.

What is occurring on this switch?
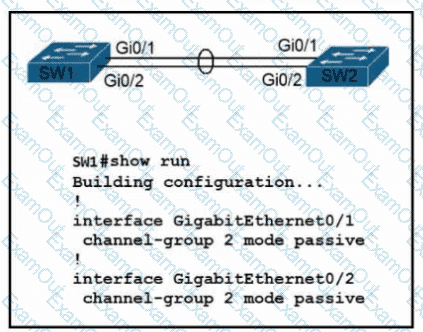
Refer to the exhibit. Which configuration enables SW2 to establish an LACP EtherChannel?
What is a similarity between global and unique local IPv6 addresses?
Which header must be included in a REST request from an application that requires JSON-formatted content?
Which type of protocol is VRRP?
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
Which IP address is used when an administrator must open a web-based management session with a lightweight AP?
What is represented by the word "LB13" within this JSON schema?