What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
Which access control should a chief information security officer select to protect extremely sensitive data categorized at various levels of confidentiality?
Refer to the exhibit.
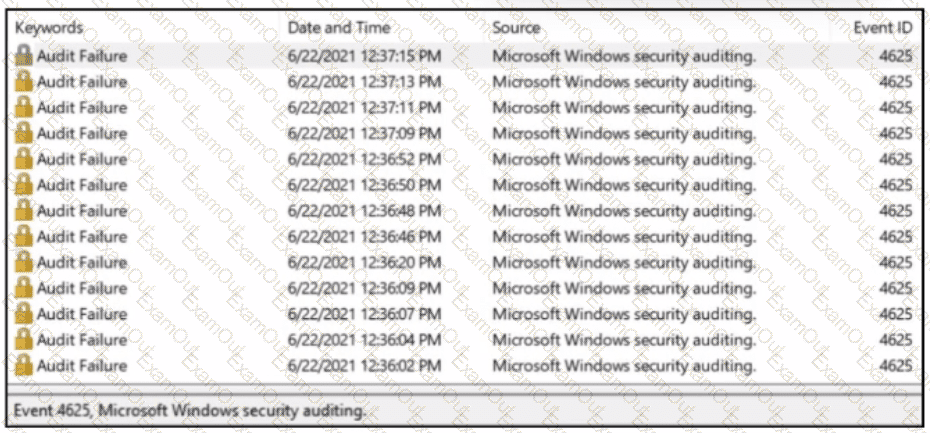
A SOC analyst received a message from SIEM about abnormal activity on the Windows server The analyst checked the Windows event log and saw numerous Audit Failures logs. What is occurring?

Refer to the exhibit. What is occurring?
Which artifact is used to uniquely identify a detected file?
A security analyst received a ticket about suspicious traffic from one of the workstations. During the investigation, the analyst discovered that the workstation was communicating with an external IP. The analyst could not investigate further and escalated the case to a T2 security analyst. What are the two data visibility challenges that the security analyst should identify? (Choose two.)
Which security principle is violated by running all processes as root or administrator?
What is a benefit of using asymmetric cryptography?
Which type of data consists of connection level, application-specific records generated from network traffic?

