A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load What is the next step the engineer should take to investigate this resource usage7
An engineer received a ticket to investigate a potentially malicious file detected by a malware scanner that was trying to execute multiple commands. During the initial review, the engineer discovered that the file was created two days prior. Further analyses show that the file was downloaded from a known malicious domain after a successful phishing attempt on an asset owner. At which phase of the Cyber Kill Chain was this attack mitigated?
An analyst see that this security alert "Default-Botnet-Communication-Detection-By-Endpoint" has been raised from the IPS. The analyst checks and finds that an endpoint communicates to the C&C. How must an impact from this event be categorized?
Refer to the exhibit.
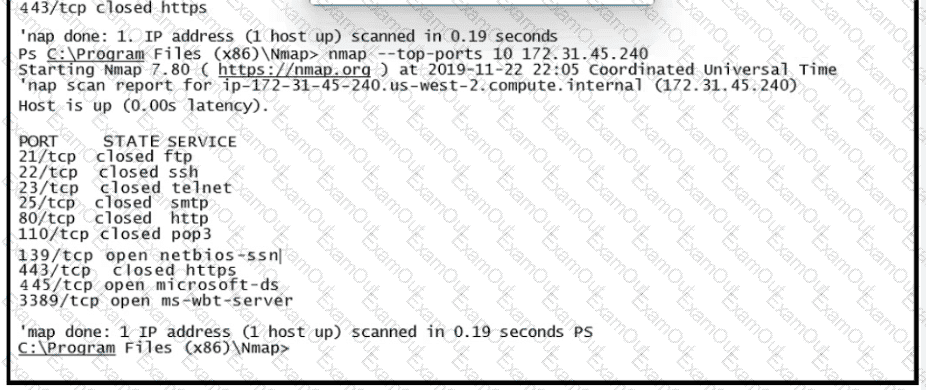
What does this output indicate?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
Which of these is a defense-in-depth strategy principle?
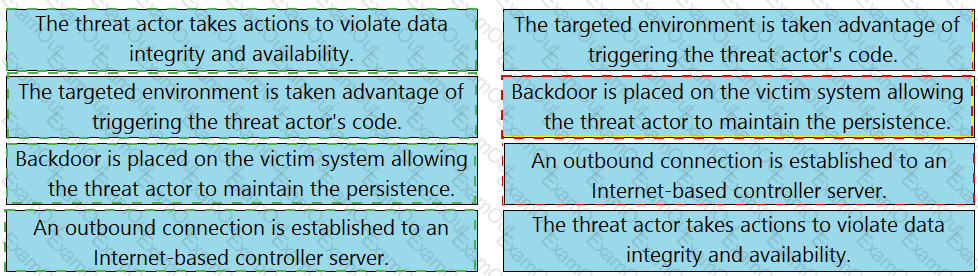
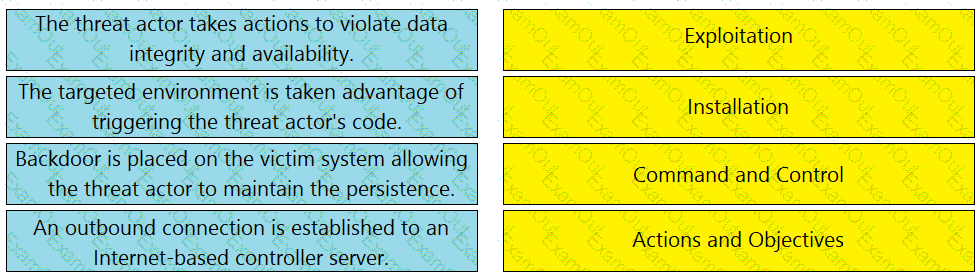
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned.
If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?