Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
According to CVSS, what is attack complexity?
What does this regular expression do?
192|172).(168|1[6-9]|2[0-9]|3[0-1]).[0-9]{1,3}.[0-9]{1,3}\b
Which are two denial-of-service attacks? (Choose two.)
Which SOC metric represents the time to stop the incident from causing further damage to systems or data?
What is the benefit of processing statistical data for security systems?
Refer to the exhibit.
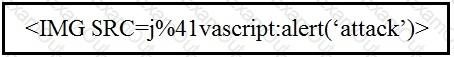
Which kind of attack method is depicted in this string?
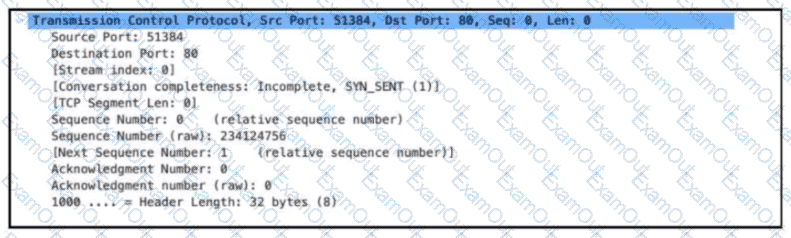
Refer to the exhibit. Which alert is identified from this packet?
What is a difference between signature-based and behavior-based detection?
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?

