Which two attacks are denial-of-service (DoS) attacks? (Choose two.)
Which technology assures that the information transferred from point A to point B is unaltered and authentic?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Which two measures are used by the defense-m-depth strategy? (Choose two)
Refer to the exhibit.
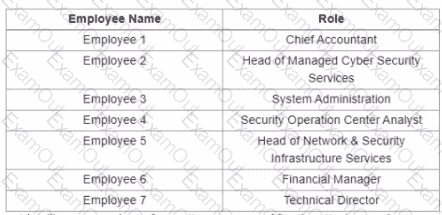
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
Which attack method intercepts traffic on a switched network?
Refer to the exhibit.
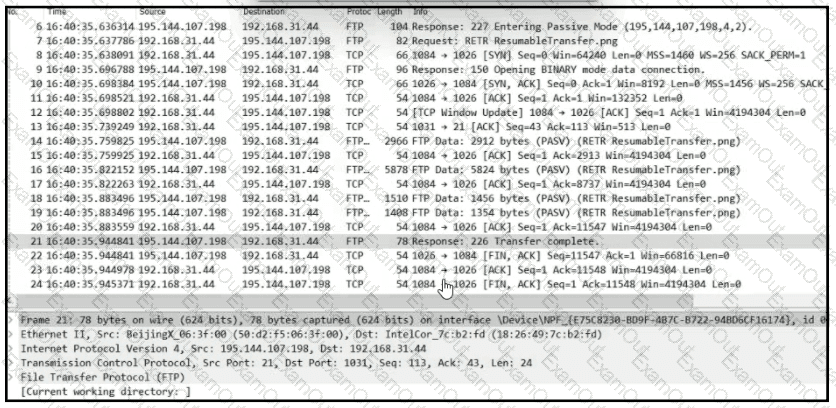
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
Refer to the exhibit.
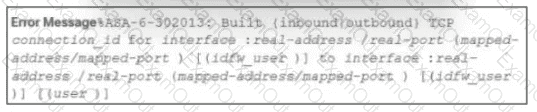
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?

