A security specialist is investigating an incident regarding a recent major breach in the organization. The accounting data from a 24-month period is affected due to a trojan detected in a department's critical server. A security analyst investigates the incident and discovers that an incident response team member who detected a trojan during regular AV scans had made an image of the server for evidence purposes. The security analyst made animage again to compare the hashes of the two images, and they appeared to differ and do not match. Which type of evidence is the security analyst dealing with?
Which piece of information is needed for attribution in an investigation?
Which statement describes indicators of attack?
Refer to the exhibit.
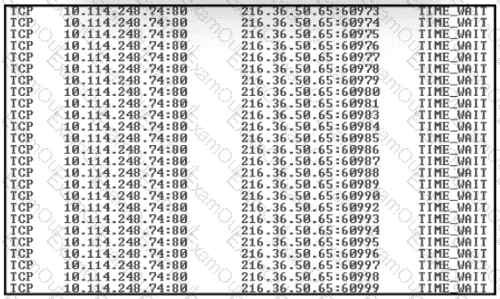
An engineer received a ticket about a slowed-down web application. The engineer runs the #netstat -an command. How must the engineer interpret the results?
How does agentless monitoring differ from agent-based monitoring?
Refer to the exhibit
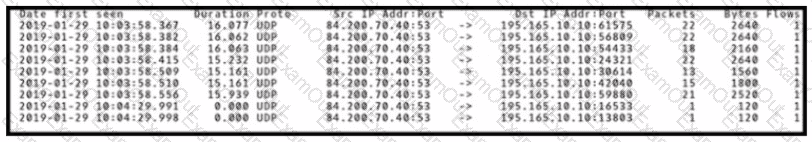
An engineer is analyzing DNS response packets that are larger than expected The engineer looks closer and notices a lack of appropriate DNS queries What is occurring?
What describes a buffer overflow attack?
Drag and drop the security concept on the left onto the example of that concept on the right.
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
Which tool provides a full packet capture from network traffic?