Which type of data must an engineer capture to analyze payload and header information?
What describes the public key infrastructure (PKI)?
Refer to exhibit.
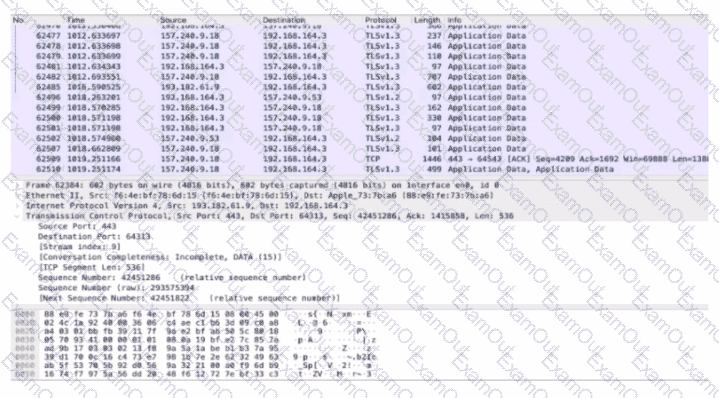
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
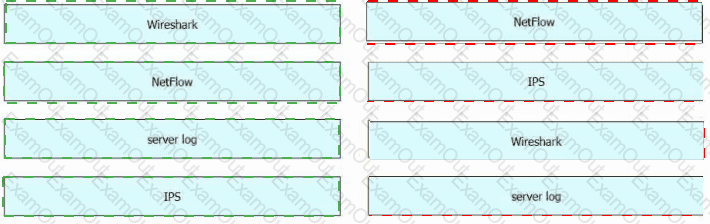
Drag and drop the data source from the left onto the data type on the right.
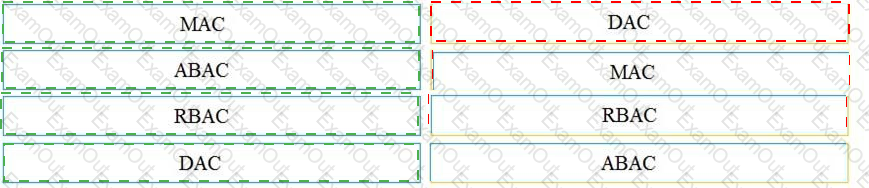
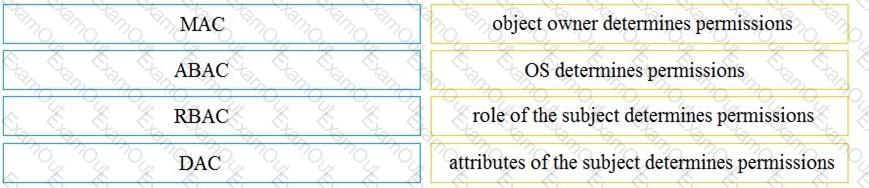
Drag and drop the access control models from the left onto the correct descriptions on the right.
Which information must an organization use to understand the threats currently targeting the organization?
An analyst performs traffic analysis to detect data exfiltration and identifies a high frequency of DNS requests in a small period of time Which technology makes this behavior feasible?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
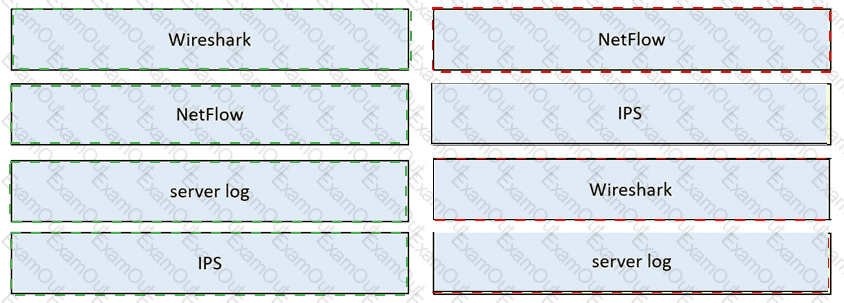
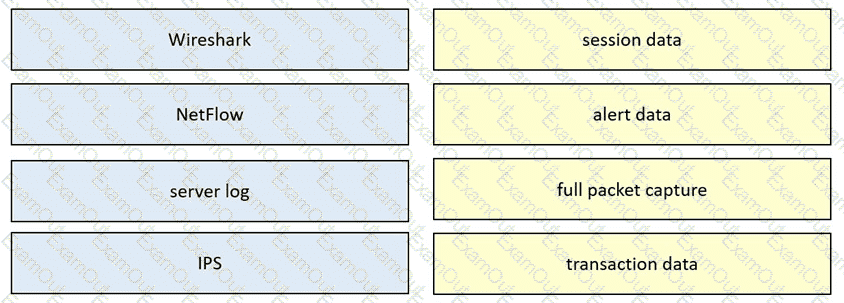
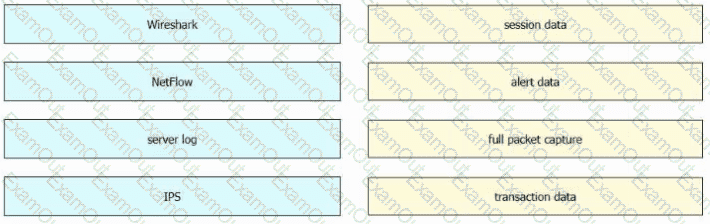
Drag and drop the data sources from the left onto the corresponding data types on the right.
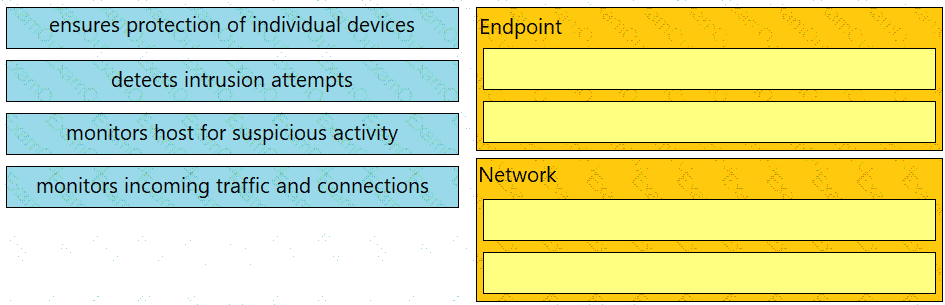
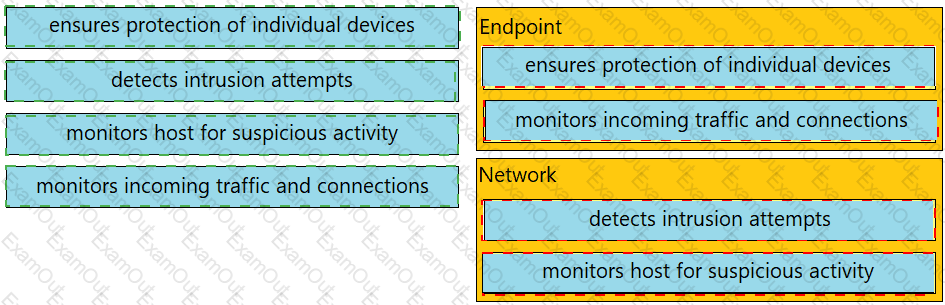
Drag and drop the uses on the left onto the type of security system on the right.