Refer to the exhibit.
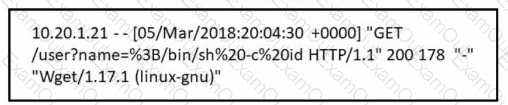
Which attack is being attempted against a web application?
What is rule-based detection when compared to statistical detection?
What is a difference between a threat and a risk?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Refer to the exhibit.
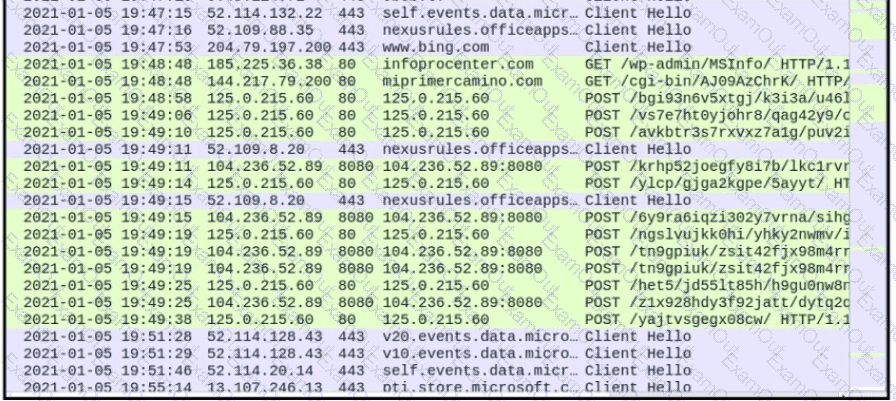
What is occurring?
What is a characteristic of a temporal score in CVSS?
A data privacy officer at a marketing firm has received a request from a former client to delete all personally sensitive information held by the company. The firm operates globally and follows international data protection standards. The only information retained about the client is a unique customer ID, "051473912", which is not directly tied to the name, address, or any other identifiable details. Which action should the data privacy officer take?
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
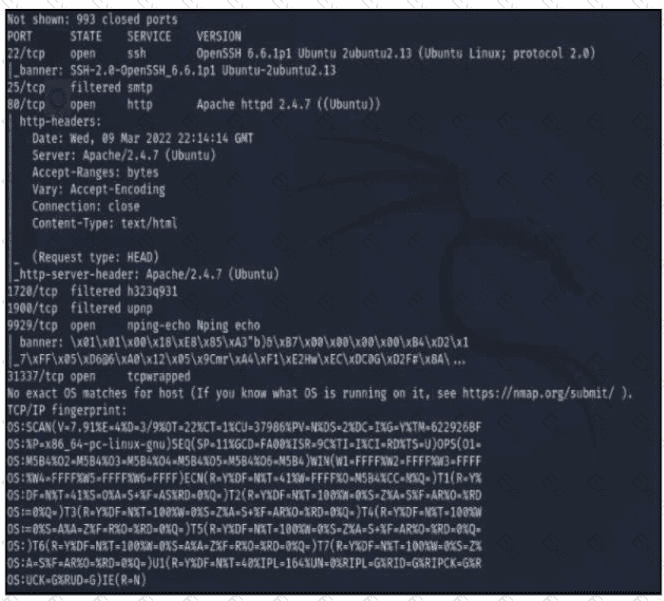
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)

