A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
Which process is used when IPS events are removed to improve data integrity?
Which evasion method involves performing actions slower than normal to prevent detection?
Refer to the exhibit.
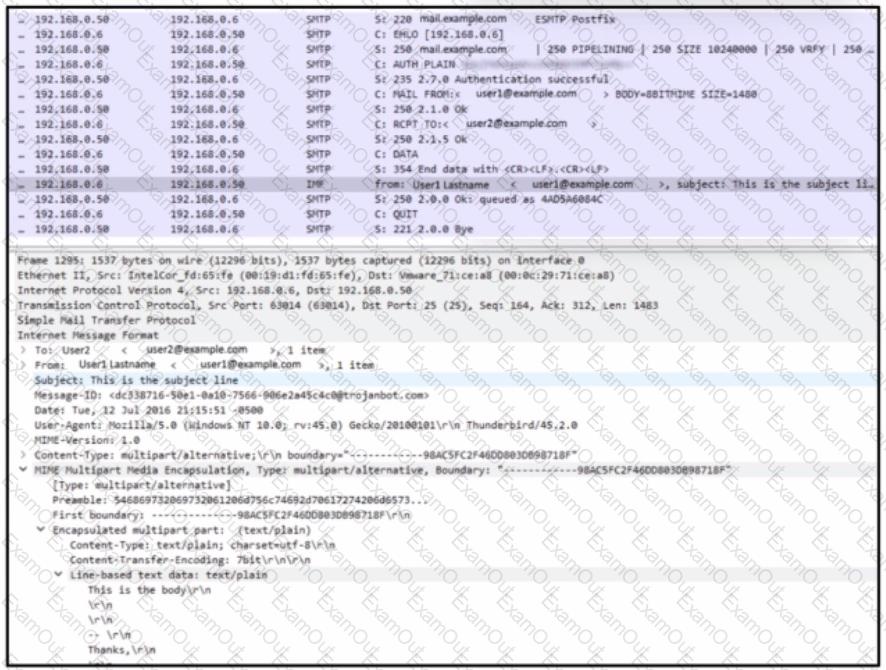
What is occurring?
Refer to the exhibit.
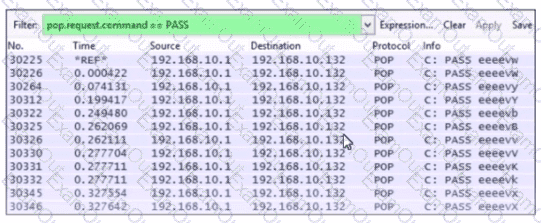
Which alert is identified from this packet capture?
What is a purpose of a vulnerability management framework?
How does an attacker observe network traffic exchanged between two users?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
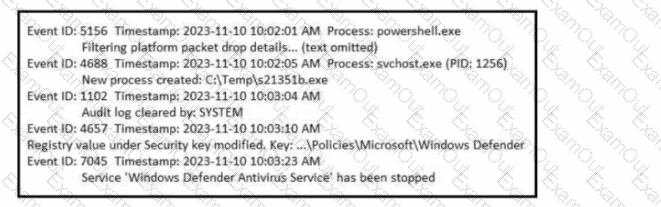
Refer to the exhibit. A SOC analyst is examining the Windows security logs of one of the endpoints. What is the possible reason for this event log?

