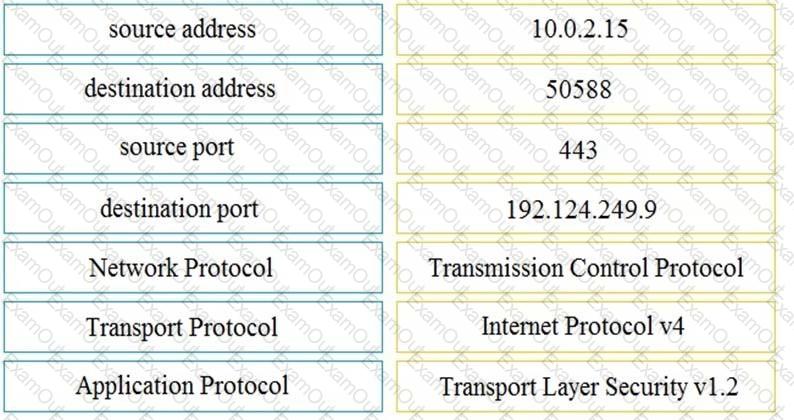
Which security principle requires more than one person is required to perform a critical task?
What is the name of the technology that searches for and reports on known weaknesses and flaws present in an organization’s IT infrastructure?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
An engineer must compare NIST vs ISO frameworks The engineer deeded to compare as readable documentation and also to watch a comparison video review. Using Windows 10 OS. the engineer started a browser and searched for a NIST document and then opened a new tab in the same browser and searched for an ISO document for comparison
The engineer tried to watch the video, but there 'was an audio problem with OS so the engineer had to troubleshoot it At first the engineer started CMD and looked fee a driver path then locked for a corresponding registry in the registry editor The engineer enabled "Audiosrv" in task manager and put it on auto start and the problem was solved Which two components of the OS did the engineer touch? (Choose two)
Which risk approach eliminates activities posing a risk exposure?
What is the difference between the ACK flag and the RST flag?
Refer to the exhibit.

Which component is identifiable in this exhibit?
What are two differences of deep packet inspection compared to stateful firewall inspection? (Choose two.)
Which data capture includes payload and header information?
Refer to the exhibit.
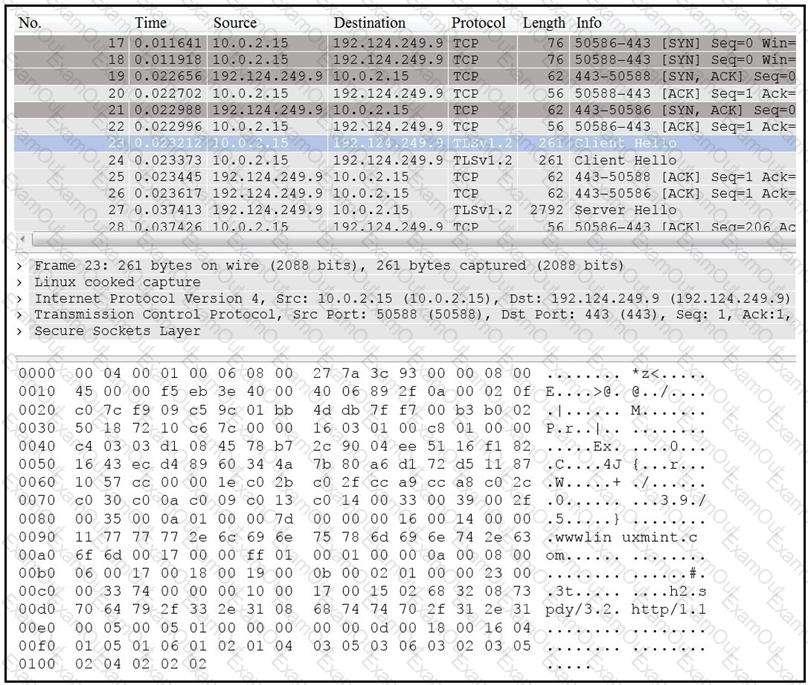
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.