What is used to maintain persistent control of an exploited device?
What is the impact of false positive alerts on business compared to true positive?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Which tool is used by threat actors on a webpage to take advantage of the software vulnerabilities of a system to spread malware?
Which category relates to improper use or disclosure of PII data?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
Refer to the exhibit.

What is the outcome of the command?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
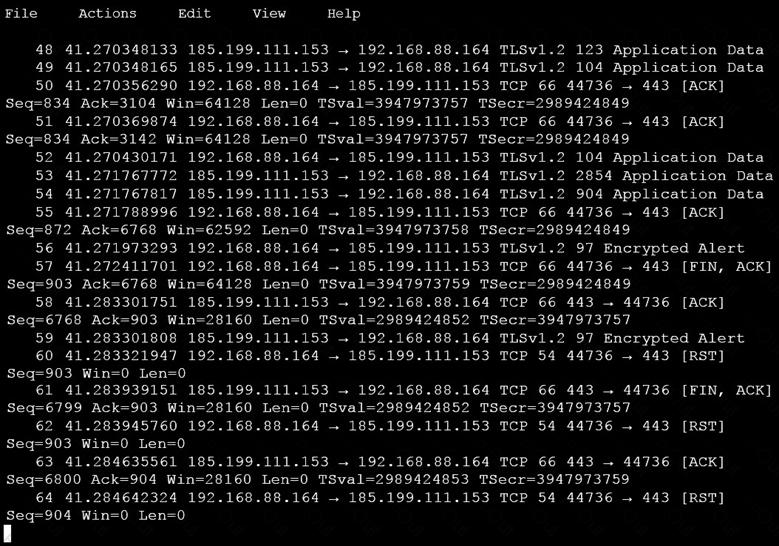
Which obfuscation technique is the attacker using?
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?

