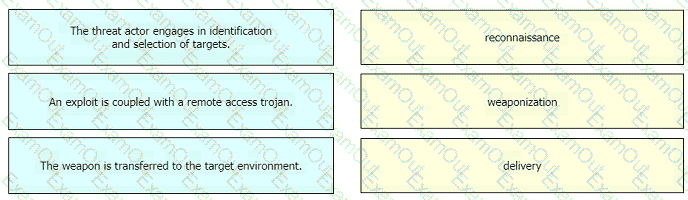
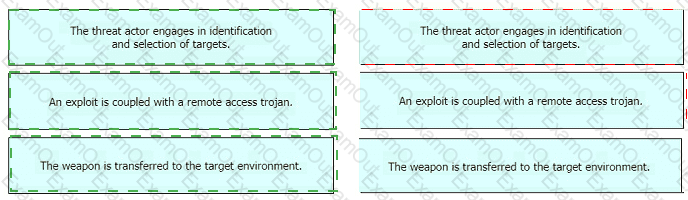
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
An organization's security team detected network spikes coming from the internal network. An investigation concluded that the spike in traffic was from intensive network scanning. How must the analyst collect the traffic to isolate the suspicious host?
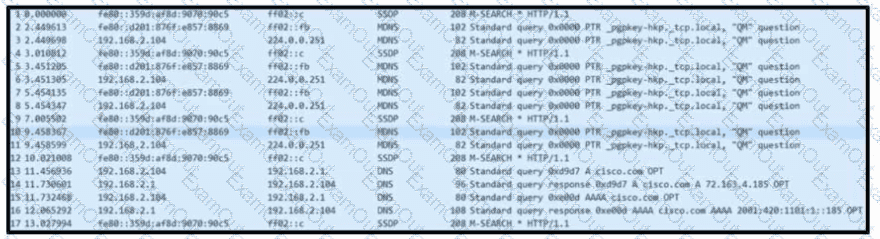
Refer to the exhibit. Based on the .pcap file, which DNS server is used to resolve cisco.com?
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
Refer to the exhibit.
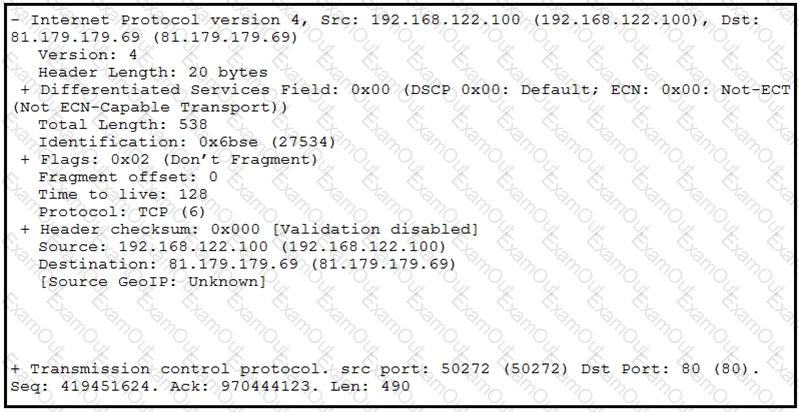
What should be interpreted from this packet capture?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
How does a certificate authority impact security?
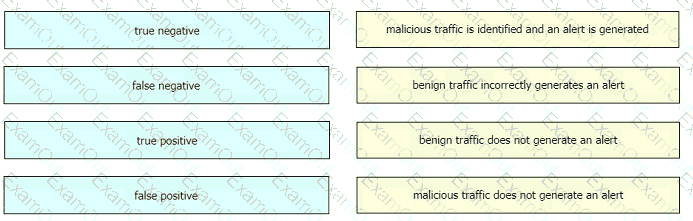
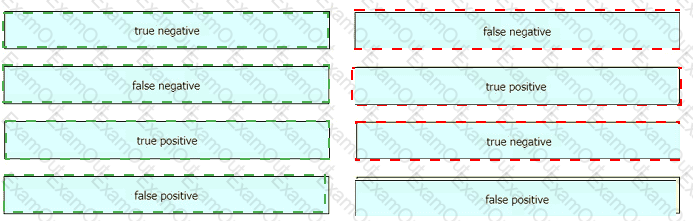
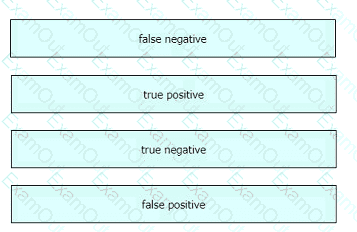
Drag and drop the event term from the left onto the description on the right.
A user reports that a mobile application is working very slowly. A DDoS detection tool reports high-volume traffic. During which phase does the CSIRT ensure that the incident does not continue and confirm that the organization has taken the required actions?
An engineer is working on the implementation of digital certificates for new cntical web applications One of the requirements is that the https connection must be validated and protected against malicious network impersonators The server will be exposed externally from the DMZ network Which certificate must be used?

 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated