Refer to the exhibit.
What is occurring?
Refer to the exhibit.
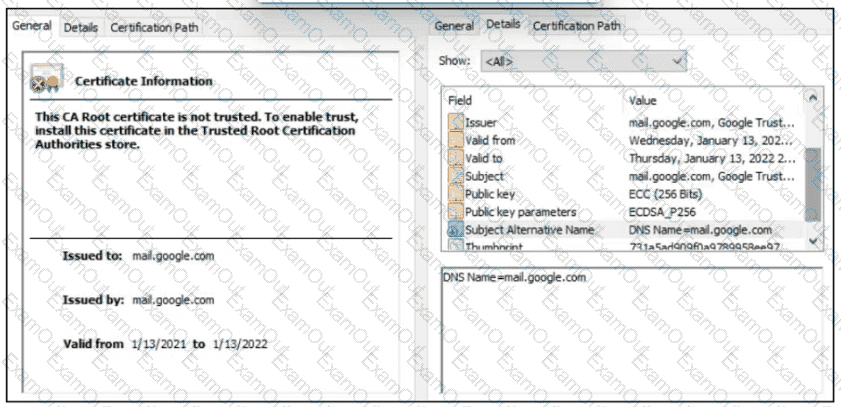
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
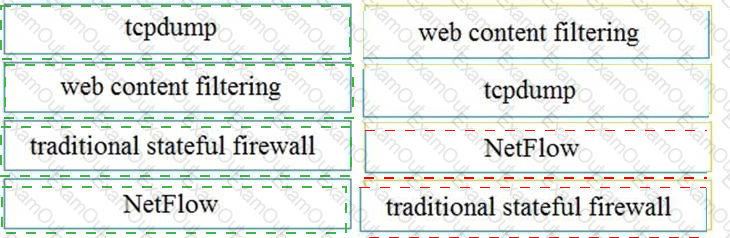
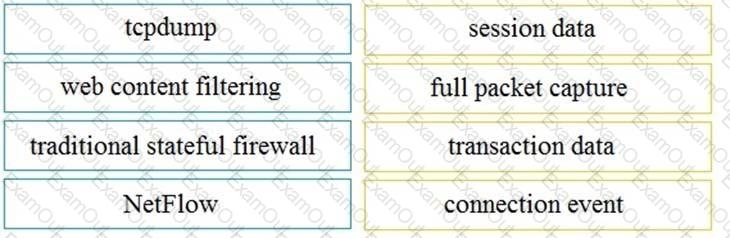
Drag and drop the technology on the left onto the data type the technology provides on the right.
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?
What is a difference between inline traffic interrogation and traffic mirroring?
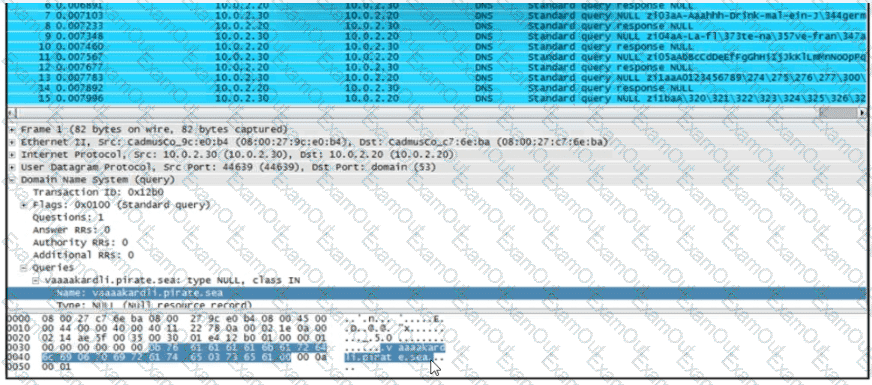
Refer to the exhibit.

Which type of log is displayed?
What are indicators of attack?
What is the purpose of a ransomware attack?
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
Which security technology allows only a set of pre-approved applications to run on a system?