A customer wants to use ECMP to provide additional throughput and availability for their critical business applications. Some applications require load balancing for scale and availability.
Which two Edge design choices can an architect present to the customer? (Choose two.)
An architect is helping an organization with the Logical Design of an NSX-T Data Center solution.
This information was gathered during the Assessment Phase:
Data between two networks connected over a public network needs to be encrypted.
Certificate authentication is required.
Dynamic route learning is preferred.
Which selection should the architect include in their design? (Choose the best answer.)
An architect is helping an organization with the Conceptual Design of an NSX-T Data Center solution.
This information was gathered by the architect during the Discover Task of the Engagement Lifecycle:
There are applications which use IPv6 addressing.
Network administrators are not familiar with NSX-T Data Center solutions.
Hosts can only be configured with two physical NICs.
There is an existing management cluster to deploy the NSX-T components.
Dynamic routing should be configured between the physical and virtual network.
There is a storage array available to deploy NSX-T components.
Which risk was documented by the architect? (Choose the best answer.)
According to the Discover Task of the Engagement Lifecycle, which statement would be classified as a risk? (Choose the best answer.)
What is a design justification for a solution with 3 NSX Manager nodes deployed in a 4 ESXi cluster Management Cluster? (Choose the best answer.)
Which two protocols are typically used for multicast in a NSX-T Data Center environment? (Choose two.)
Refer to the exhibit.
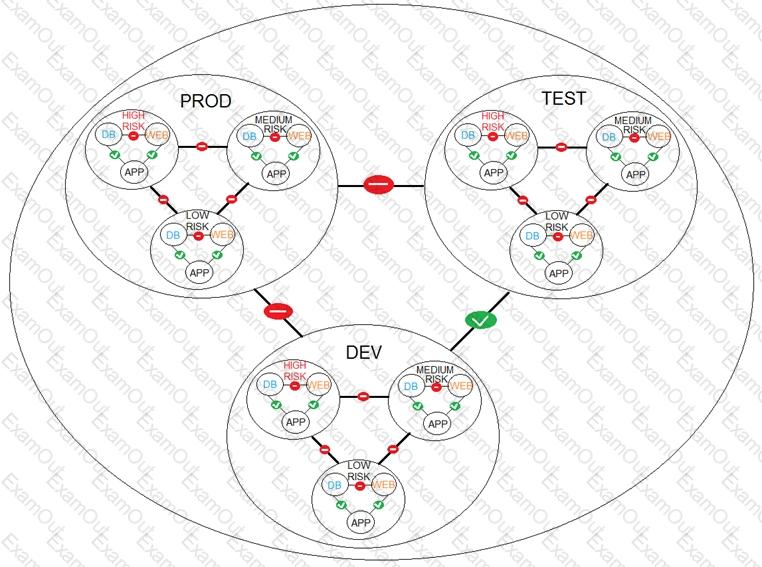
A financial company is adopting micro-services with the intent of simplifying network security. An NSX-T architect is proposing a NSX-T Data Center micro-segmentation logical design. The architect has created a diagram to share with the customer.
How many security levels will be implemented according to this Logical Design? (Choose the best answer.)
Which type of design includes vendor models, host names, IP Addresses, port connections, logical unit number sizes, and number of CPUs? (Choose the best answer.)
Which NSX-T feature is used to allocate the network bandwidth to business-critical applications and to resolve situations where several types of traffic compete for common resources? (Choose the best answer.)
An architect is helping an organization with the Physical Design of an NSX-T Data Center solution.
This information was gathered during a workshop:
Current hypervisor of choice is KVM.
Cost reduction is important.
Which two selections should the architect recommend to the organization? (Choose two.)

