A healthcare portal needs to validate the token that it sends to a Mule API. The developer plans to implement a custom policy using the HTTP Policy Transform Extension to match the token received in the header from the heathcare portal.
Which files does the developer need to create in order to package the custom policy?
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
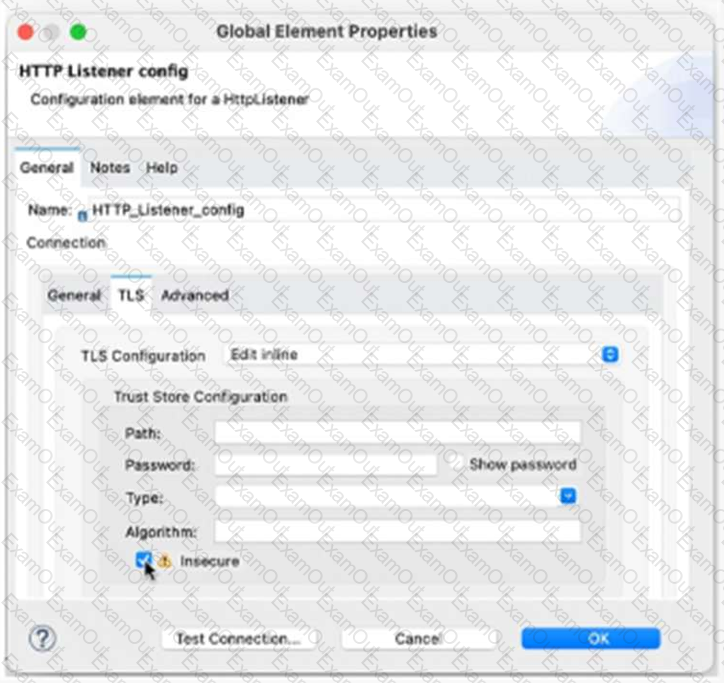
Refer to the exhibit.
What is the result if ‘’Insecure’’ selected as part of the HTTP Listener configuration?
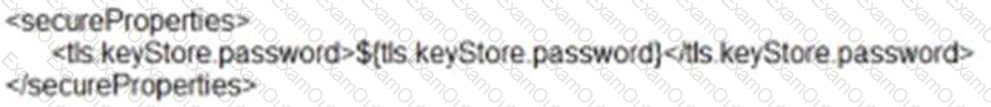
What is the MuleSoft recommended method to encrypt sensitive property data?
Refer to the exhibit.
What is the result of the Mule Maven Plugin configuration of the value of propertyits,keystorePassoword in CloudHub 2.0?
Mule application A is deployed to CloudHub and is using Object Store v2. Mute application B is also deployed to CloudHub.
Which approach can Mule application B use to remove values from Mule application A’S Object Store?
A Mule implementation uses a HTTP Request within an Unit Successful scope to connect to an API.
How should a permanent error response like HTTP:UNAUTHORIZED be handle inside Until Successful to reduce latency?
When implementing a synchronous API where the event source is an HTTP Listener, a developer needs to return the same correlation ID backto the caller in the HTTP response header.
How can this be achieved?

