Review the following transform:

Can the following output of this transform be expected, based on the input provided in the option?
Solution:

Is the following statement accurate regarding Separation of Duties (SoD)?
Solution: An SoD policy can define mitigating controls.
Is this statement correct about identityNow components?
Solution: Password interception is available for the Active Directory source.
Is this an advantage of microservice architecture?
Solution: It provides quicker resolution of unintentional issues or failures with the service.
Is the following description of an access profile correct?
Solution: It allows definition of an approval process.
Does this example accurately describe an IdentityNow data flow?
1. The user changes their password in IdentityNow.
2. The virtual appliance checks in with the IdentityNow tenant and receives the request
3. The virtual appliance contacts the IQService host.
4. The IQService host makes the change in Active Directory.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Turn off the virtual appliance's (VA) internal firewall.
Is this an example of a vanity URL?
Solution: https://my.example.com
Is this statement accurate regarding SailPoint's multi-tenant processing environment?
Solution: identityNow admins have the option to choose how often updates to their tenant occur.
Exhibit.
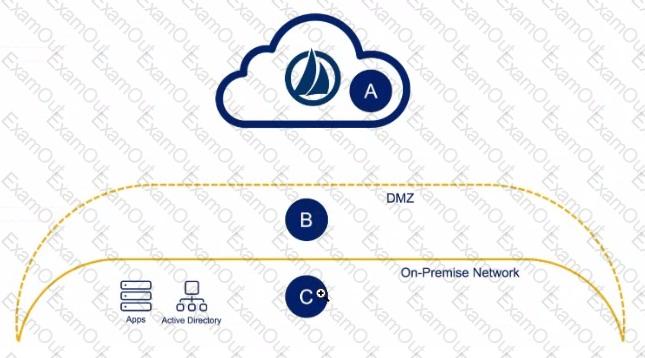
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect Where would the virtual appliances (VAs) reside In this scenario?
Solution: B

