An organization has created a custom internal application definition for "Inventory_App" on the Prisma SD-WAN controller based on its destination IP address and port (L3/L4 rule). The application server IP has just changed.
After updating the custom application definition on the controller, how is this change propagated to the branch ION devices?
BGP core peers on data center IONs are learning only a default route from the core router. Which action will protect the SD-WAN network from getting isolated in the event of BGP misconfiguration on the core routers?
A site has two internet circuits: Circuit A with 500 Mbps capacity and Circuit B with 100 Mbps capacity.
Which path policy configuration will ensure traffic is automatically shifted from a saturated circuit to the circuit with available bandwidth?
How can a network administrator detect a site outage or a service-level agreement (SLA) violation using controller-generated incidents?
In which modes can a Prisma SD-WAN branch be deployed?
A network engineer is troubleshooting a user complaint regarding "slow application performance" for an internal web application. While viewing the Flow Browser in the Prisma SD-WAN portal, the engineer notices that the Server Response Time (SRT) is consistently high (over 500ms), while the Network Transfer Time (NTT) and Round Trip Time (RTT) are low (under 50ms).
What does this data indicate about the root cause of the issue?
A network installer is at a remote branch site to deploy a new ION 3000 device. The device has been racked, cabled to the internet, and powered on. The installer has the "Claim Code" displayed on the email sent by the administrator.
When the administrator enters this Claim Code into the Prisma SD-WAN portal, what is the immediate status of the device before the configuration is fully pushed?
There are periodic complaints about the poor performance of a real-time application.
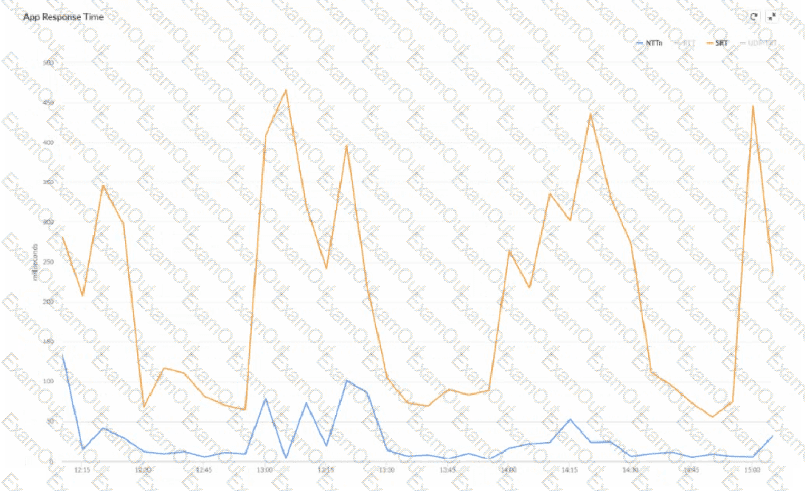
What can be inferred about the performance issue, based on the Network Transfer Time (NTT) and Server Response Time (SRT) image below?
What are two potential causes when a secondary public circuit has been added to the branch site, but the Prisma SD-WAN tunnel is not forming to the data center? (Choose two.)
Which statement is valid when integrating Prisma SD-WAN with Prisma Access remote networks?

