Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?
What is the result of creating an exception from an exploit security event?
How does DBot score an indicator that has multiple reputation scores?
Which process in the causality chain does the Cortex XDR agent identify as triggering an event sequence?
Which source provides data for Cortex XDR?
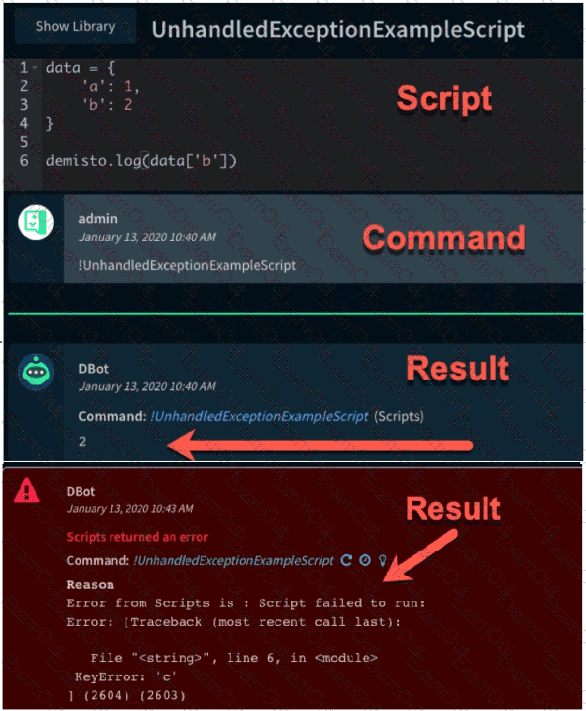
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS
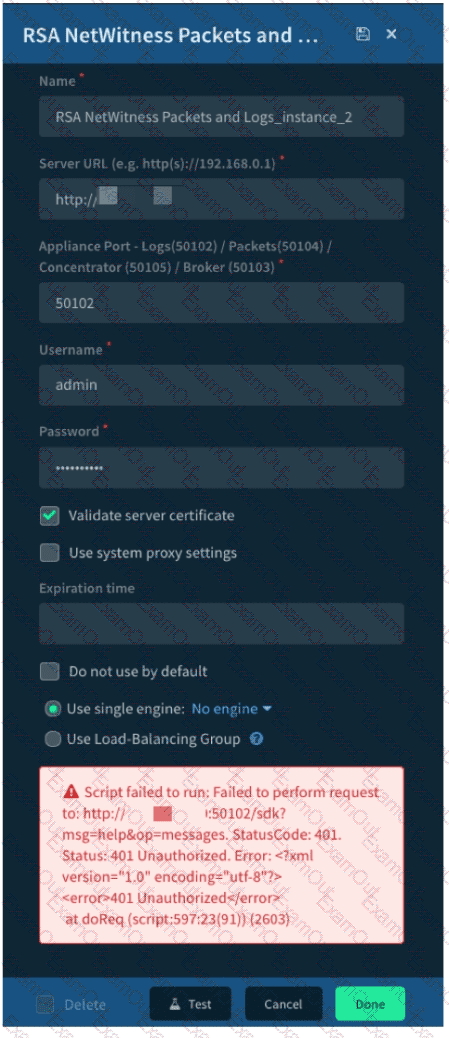
Given the integration configuration and error in the screenshot what is the cause of the problem?
Which two actions are required to add indicators to the whitelist? (Choose two.)
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
Cortex XSOAR has extracted a malicious Internet Protocol (IP) address involved in command-and-control (C2) traffic.
What is the best method to block this IP from communicating with endpoints without requiring a configuration change on the firewall?

