Which method is used for third-party network data consumption?
Which CLI query would bring back Notable Events from Splunk?
A)
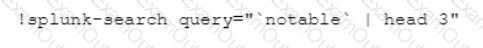
B)
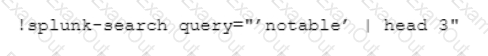
C)

D)
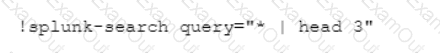
Which element displays an entire picture of an attack, including the root cause or delivery point?
Which command-line interface (CLI) query would retrieve the last three Splunk events?
What are two manual actions allowed on War Room entries? (Choose two.)
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Approximately how many Cortex XSOAR marketplace integrations exist?
What is the retention requirement for Cortex Data Lake sizing?
What are the key capabilities of the ASM for Remote Workers module?
What is the difference between an exception and an exclusion?

