In Panorama, what is the correct order of precedence for security policies?
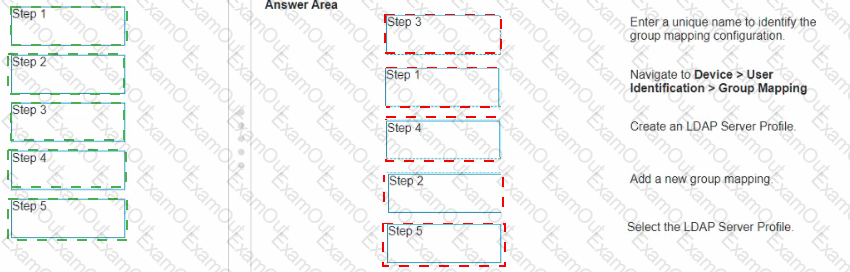
Match the task for server settings in group mapping with its order in the process.
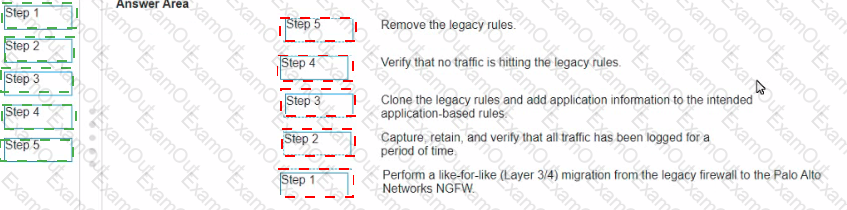
Match the App-ID adoption task with its order in the process.

Your customer has asked you to set up tunnel monitoring on an IPsec VPN tunnel between two offices What three steps are needed to set up tunnel monitoring? (Choose three)
Which of the following is a primary use case for the Decryption Broker feature?
You are hosting a public-facing web server on your DMZ and access to that server is through a Palo Alto Networks firewall Both internal clients and internet clients access this web server using the FQDN public webserver acme com which resolves to the public address of 99.99 99.2
Which combination of NAT policies is necessary to enable access to the web server for both internal and internet clients?
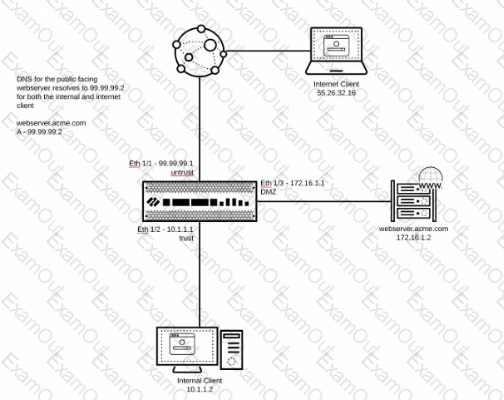
A)

B)
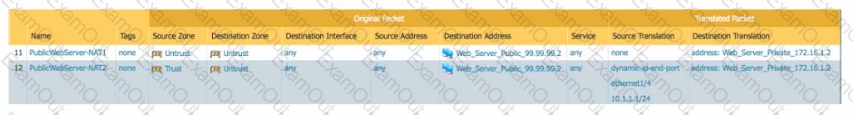
C)
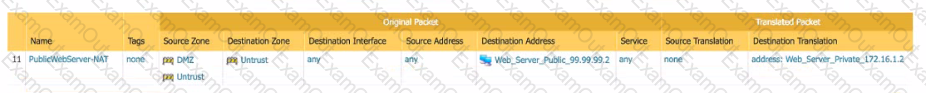
D)
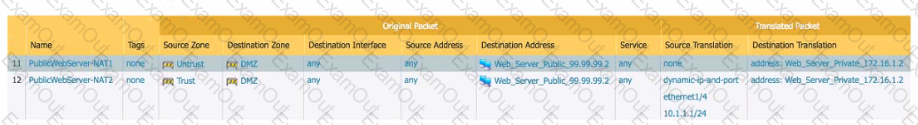
Which feature allows you to use multiple links simultaneously to balance the load in a Palo Alto Networks firewall?
Which two conditions must be met for a firewall to successfully forward traffic to a syslog server? (Choose two)