For the firewall to use Active Directory to authenticate users, which Server Profile is required in the Authentication Profile?
Which feature must be configured to enable a data plane interface to submit DNS queries originated from the firewall on behalf of the control plane?
What must be configured before setting up Credential Phishing Prevention?
An administrator would like to determine the default deny action for the application dns-over-https
Which action would yield the information?
When is an event displayed under threat logs?
URL categories can be used as match criteria on which two policy types? (Choose two.)
What are three valid information sources that can be used when tagging users to dynamic user groups? (Choose three.)
Selecting the option to revert firewall changes will replace what settings?
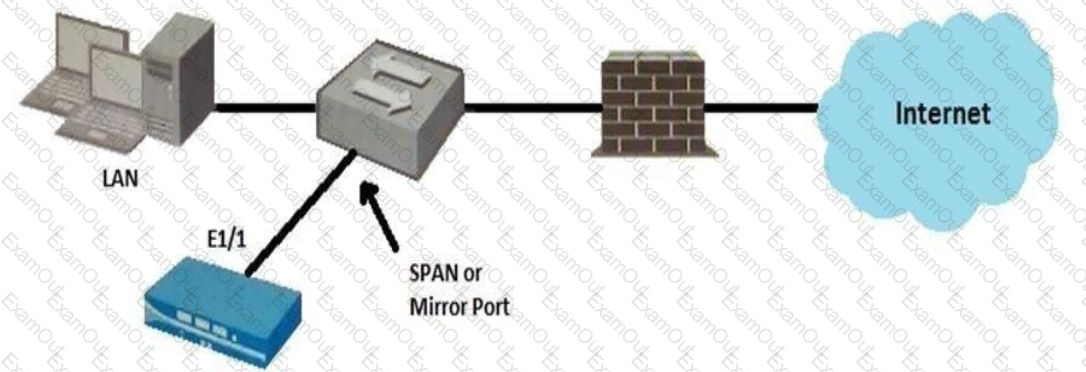
Given the topology, which zone type should you configure for firewall interface E1/1?
Which update option is not available to administrators?

