Which three types of entries can be excluded from an external dynamic list (EDL)? (Choose three.)
Which URL profiling action does not generate a log entry when a user attempts to access that URL?
Which three types of Source NAT are available to users inside a NGFW? (Choose three.)
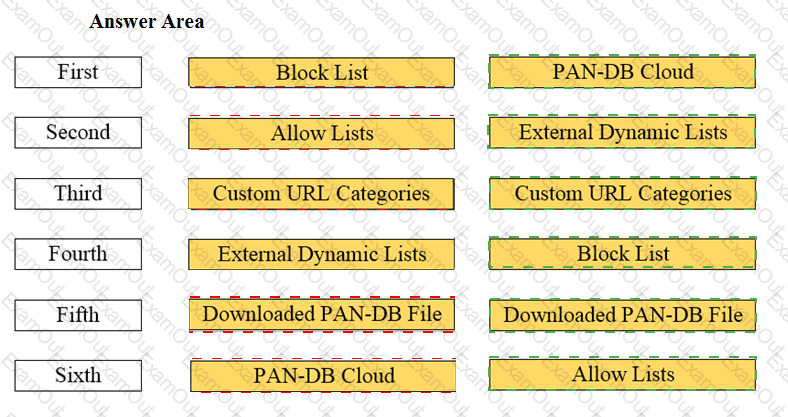
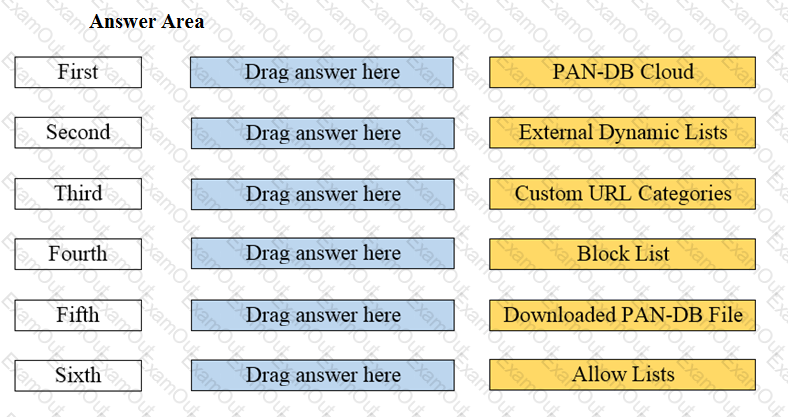
Arrange the correct order that the URL classifications are processed within the system.
Which Security policy set should be used to ensure that a policy is applied first?
How many zones can an interface be assigned with a Palo Alto Networks firewall?
An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.
What is the correct process to enable this logging1?
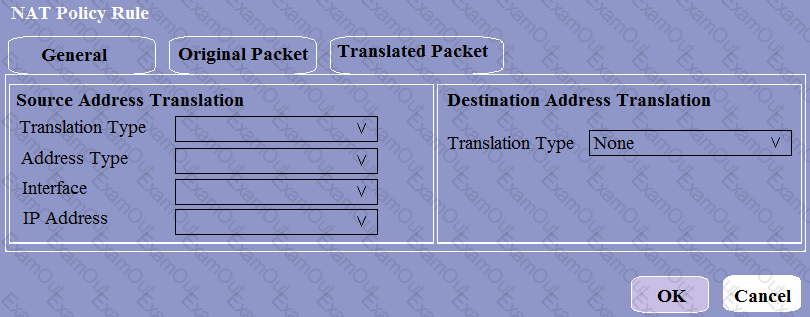
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
How are service routes used in PAN-OS?
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?