Which two of the following statements are true?
How does the use of new technologies such as big data impact auditing?
Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life insurance. The company was founded in North Carolina, but have recently expanded in other locations, including Europe and Africa.
Sinvestment is committed to complying with laws and regulations applicable to their industry and preventing any information security incident. They have implemented an ISMS based on ISO/IEC 27001 and have applied for ISO/IEC 27001 certification.
Two auditors were assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment. they started the audit activities. First, they reviewed the documentation required by the standard, including the declaration of the ISMS scope, information security policies, and internal audits reports. The review process was not easy because, although Sinvestment stated that they had a documentation procedure in place, not all documents had the same format.
Then, the audit team conducted several interviews with Sinvestment's top management to understand their role in the ISMS implementation. All activities of the stage 1 audit were performed remotely, except the review of documented information, which took place on-site, as requested by Sinvestment.
During this stage, the auditors found out that there was no documentation related to information security training and awareness program. When asked, Sinvestment's representatives stated that the company has provided information security training sessions to all employees. Stage 1 audit gave the audit team a general understanding of Sinvestment's operations and ISMS.
The stage 2 audit was conducted three weeks after stage 1 audit. The audit team observed that the marketing department (which was not included in the audit scope) had no procedures in place to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the information security policy of the company, the issue was included in the audit report. In addition, during stage 2 audit, the audit team observed that Sinvestment did not record logs of user activities. The procedures of the company stated that "Logs recording user activities should be retained and regularly reviewed," yet the company did not present any evidence of the implementation of such procedure.
During all audit activities, the auditors used observation, interviews, documented information review, analysis, and technical verification to collect information and evidence. All the audit findings during stages 1 and 2 were analyzed and the audit team decided to issue a positive recommendation for certification.
During stage 1 audit, the audit team found out that Sinvestment did not have records on information security training and awareness. What Sinvestment do in this case? Refer to scenario 6.
Scenario 3: Rebuildy is a construction company located in Bangkok.. Thailand, that specializes in designing, building, and maintaining residential buildings. To ensure the security of sensitive project data and client information, Rebuildy decided to implement an ISMS based on ISO/IEC 27001. This included a comprehensive understanding of information security risks, a defined continual improvement approach, and robust business solutions.
The ISMS implementation outcomes are presented below
•Information security is achieved by applying a set of security controls and establishing policies, processes, and procedures.
•Security controls are implemented based on risk assessment and aim to eliminate or reduce risks to an acceptable level.
•All processes ensure the continual improvement of the ISMS based on the plan-do-check-act (PDCA) model.
•The information security policy is part of a security manual drafted based on best security practices Therefore, it is not a stand-alone document.
•Information security roles and responsibilities have been clearly stated in every employees job description
•Management reviews of the ISMS are conducted at planned intervals.
Rebuildy applied for certification after two midterm management reviews and one annual internal audit Before the certification audit one of Rebuildy’s former employees approached one of the audit team members to tell them that Rebuildy has several security problems that the company is trying to conceal. The former employee presented the documented evidence to the audit team member Electra, a key client of Rebuildy, also submitted evidence on the same issues, and the auditor determined to retain this evidence instead of the former employee's. The audit team member remained in contact with Electra until the audit was completed, discussing the nonconformities found during the audit. Electra provided additional evidence to support these findings.
At the beginning of the audit, the audit team interviewed the company’s top management They discussed, among other things, the top management's commitment to the ISMS implementation. The evidence obtained from these discussions was documented in written confirmation, which was used to determine Rebuildy’s conformity to several clauses of ISO/IEC 27001
The documented evidence obtained from Electra was attached to the audit report, along with the nonconformities report. Among others, the following nonconformities were detected:
•An instance of improper user access control settings was detected within the company's financial reporting system.
•A stand-alone information security policy has not been established. Instead, the company uses a security manual drafted based on best security practices.
After receiving these documents from the audit team, the team leader met Rebuildy’s top management to present the audit findings. The audit team reported the findings related to the financial reporting system and the lack of a stand-alone information security policy. The top management expressed dissatisfaction with the findings and suggested that the audit team leader's conduct was unprofessional, implying they might request a replacement. Under pressure, the audit team leader decided to cooperate with top management to downplay the significance of the detected nonconformities. Consequently, the audit team leader adjusted the report to present a more favorable view, thus misrepresenting the true extent of Rebuildy's compliance issues.
Based on the scenario above, answer the following question:
Question:
Is it acceptable for the auditor to prioritize keeping the evidence provided by Electra over the evidence provided by the former employee?
Question:
Which of the following statements regarding documented information in an organization's ISMS is incorrect?
You are performing an ISMS audit at a European-based residential nursing home called ABC that provides healthcare services. The next step in your audit plan is to verify the effectiveness of the continual improvement process.
During the audit, you learned most of the residents' family members (90%) receive WeCare medical devices promotion advertisements through email and SMS once a week via ABC's healthcare mobile app. All of them do not agree on the use of the collected personal data for marketing or any other purposes than nursing and medical care on the signed service agreement with ABC. They have very strong reason to believe that ABC is leaking residents' and family members' personal information to a non-relevant third party and they have filed complaints.
The Service Manager says that, after investigation, all these complaints have been treated as nonconformities. The corrective actions have been planned and implemented according to the nonconformity and corrective management procedure (Document reference ID: ISMS_L2_10.1, version 1).
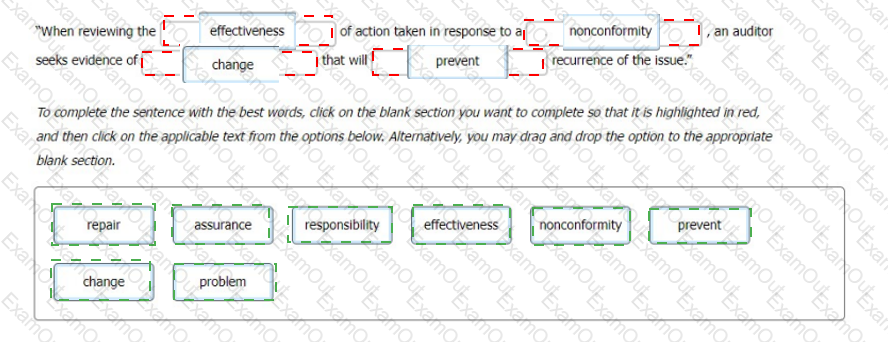
You write a nonconformity which you will follow up on later. Select the words that best complete the sentence:

Scenario 8: Tessa. Malik, and Michael are an audit team of independent and qualified experts in the field of security, compliance, and business planning and strategies. They are assigned to conduct a certification audit in Clastus, a large web design company. They have previously shown excellent work ethics, including impartiality and objectiveness, while conducting audits. This time, Clastus is positive that they will be one step ahead if they get certified against ISO/IEC 27001.
Tessa, the audit team leader, has expertise in auditing and a very successful background in IT-related issues, compliance, and governance. Malik has an organizational planning and risk management background. His expertise relies on the level of synthesis and analysis of an organization's security controls and its risk tolerance in accurately characterizing the risk level within an organization On the other hand, Michael is an expert in the practical security of controls assessment by following rigorous standardized programs.
After performing the required auditing activities, Tessa initiated an audit team meeting They analyzed one of Michael s findings to decide on the issue objectively and accurately. The issue Michael had encountered was a minor nonconformity in the organization's daily operations, which he believed was caused by one of the organization's IT technicians As such, Tessa met with the top management and told them who was responsible for the nonconformity after they inquired about the names of the persons responsible
To facilitate clarity and understanding, Tessa conducted the closing meeting on the last day of the audit. During this meeting, she presented the identified nonconformities to the Clastus management. However, Tessa received advice to avoid providing unnecessary evidence in the audit report for the Clastus certification audit, ensuring that the report remains concise and focused on the critical findings.
Based on the evidence examined, the audit team drafted the audit conclusions and decided that two areas of the organization must be audited before the certification can be granted. These decisions were later presented to the auditee, who did not accept the findings and proposed to provide additional information. Despite the auditee's comments, the auditors, having already decided on the certification recommendation, did not accept the additional information. The auditee's top management insisted that the audit conclusions did not represent reality, but the audit team remained firm in their decision.
Based on the scenario above, answer the following question:
Question:
After analyzing the audit conclusions, Company X accepted the risk related to a detected nonconformity and decided not to take corrective action. However, their decision was not documented. Is this acceptable?
You are conducting a third-party surveillance audit when another member of the audit team approaches you seeking clarification. They have been asked to assess the organisation's application of control 5.7 - Threat Intelligence. They are aware that this is one of the new controls introduced in the 2022 edition of ISO/IEC 27001, and they want to make sure they audit the control correctly.
They have prepared a checklist to assist them with their audit and want you to confirm that their planned activities are aligned with the control's requirements.
Which three of the following options represent valid audit trails?
What is we do in ACT - From PDCA cycle
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
According to scenario 8, the audit team evaluated the action plan and concluded that it would resolve the detected nonconformities. Is this acceptable?