Which two configurations can be used to protect sensitive data In a database?
Examine this command:
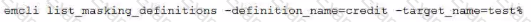
What masking definitions does it list?
Which two authorization rights does a Database Vault realm owner have that a realm participant does not have?
Which statement is true about Network ACLs?
Database user SCOTT requires the privilege to select from all tables and you decide to configure this using a global role.
You have not yet configured the database with Enterprise User Security.
You plan to perform these steps:
1. create role GLOBAI._ROI.E identified globally;
2. grant select any table to GLODAL_COLE;
3. grant GLOBAL_ROLE to SCOTT;
What is the result?
Which statement can be used to force password complexity in the password file?
You must rekey encrypted sensitive credential data In your database.
You run the command alter database dictionary rekey credentials.
Which three options ate true about the bkkey process?

