You are required to remove embedded passwords from scripts that connect to database instances. Which tool can be used to implement this requirement?
Which two are true about auditing in an Oracle Database?
You configured Kerberos authentication for databases running on servers A and B.
However a database link connecting the database on server A to the database on server B fails with ORA-12638 Credential retrieval failed.
Where must you make a change to sqlnet.ora to allow the database link to use its stored credentials Instead of trying to use Kerberos?
Which two statements are true about Valid Node Checking for Registration (VNCR)?
A database link must be created to connect a source Autonomous Database to target on premises database.
Examine this command:
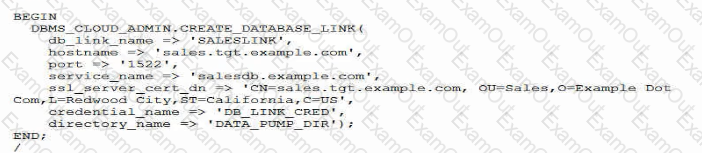
Which two options are true?
Database Vault is not used in your installation.
Why is a conventional secure application role more secure than a normal role?
Which CVSS Version 3.1 metric indicates how close an attacker needs to be to the vulnerable component?
Examine this code which executes successfully:
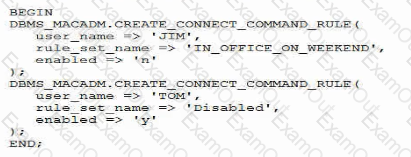
If the IN_OFFICE_ON_WEEKEND rule set returns true for an attempt to connect from Inside the office on weekends, which two are true about the effects of this configuration?
Database Vault is configured and enabled in the database. You create a rule set to enforce security on the hr. employees table.
Examine these requirements:
1. Users working In hr department are allowed to view all rows In HR.EMPLOYEES.
2. hr managers are allowed to view, update, and delete data in In HR.EMPLOYEES.
3. Audit records are to be collected for every evaluation of the rule set.
Which two options are true when creating the rule set?
You are Implementing a security policy that makes use of the USERENV namespace.
Which USERRENV value does not change for the duration of a session?

