You deployed Netskope Cloud Security Posture Management (CSPM) using pre-defined benchmark rules to monitor your cloud posture in AWS, Azure, and GCP. You are asked to assess if you can extend the Netskope CSPM solution by creating custom rules for each environment.
Which statement is correct?
You jus! deployed and registered an NPA publisher for your first private application and need to provide access to this application for the Human Resources (HR) users group only. How would you accomplish this task?
You have an NG-SWG customer that currently steers all Web traffic to Netskope using the Netskope Client. They have identified one new native application on Windows devices that is a certificate-pinned application. Users are not able to access the application due to certificate pinning. The customer wants to configure the Netskope Client so that the traffic from the application is steered to Netskope and the application works as expected.
Which two methods would satisfy the requirements? (Choose two.)
Given the following:
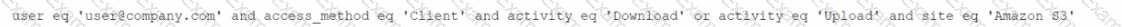
Which result does this Skope IT query provide?
You need to monitor the health of configured IPsec or GRE tunnels.
In this scenario, which two methods are supported by Netskope to accomplish this task? (Choose two.)
You are currently designing a policy for AWS S3 bucket scans with a custom DLP profile Which policy action(s) are available for this policy?
You are attempting to merge two Advanced Analytics reports with DLP incidents: Report A with 3000 rows and Report B with 6000 rows. Once merged, you notice that the merged report is missing a significant number of rows.
What is causing this behavior?
You have users connecting to Netskope from around the world You need a way for your NOC to quickly view the status of the tunnels and easily visualize where the tunnels are located Which Netskope monitoring tool would you use in this scenario?
You want to enable the Netskope Client to automatically determine whether it is on-premises or off-premises. Which two options in the Netskope Ul would you use to accomplish this task? (Choose two.)
Your organization's software deployment team did the initial install of the Netskope Client with SCCM. As the Netskope administrator, you will be responsible for all up-to-date upgrades of the client.
Which two actions would be required to accomplish this task9 (Choose two.)

