While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
Recently your company implemented Zoom for collaboration purposes and you are attempting to inspect the traffic with Netskope. Your initial attempt reveals that you are not seeing traffic from the Zoom client that is used by all users. You must ensure that this traffic is visible to Netskope.
In this scenario, which two steps must be completed to satisfy this requirement? (Choose two.)
You are asked to grant access for a group of users to an application using NPA. So far, you have created and deployed the publisher and created a private application using the Netskope console.
Which two steps must also be completed to enable your users access to the application? (Choose two.)
Review the exhibit.
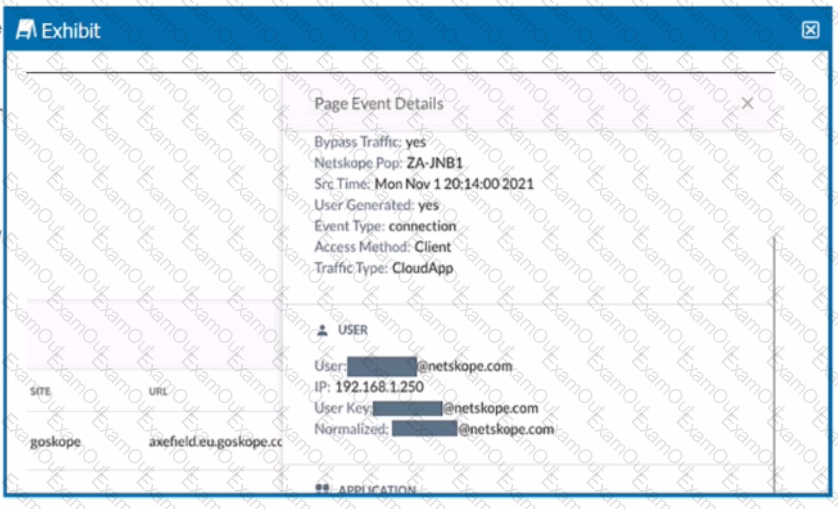
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
You are using the Netskope DLP solution. You notice that valid credit card numbers in a file that you just uploaded to an unsanctioned cloud storage solution are not triggering a policy violation. You can see the Skope IT application events for this traffic but no DLP alerts.
Which statement is correct in this scenario?
What is the purpose of the file hash list in Netskope?
Review the exhibit.
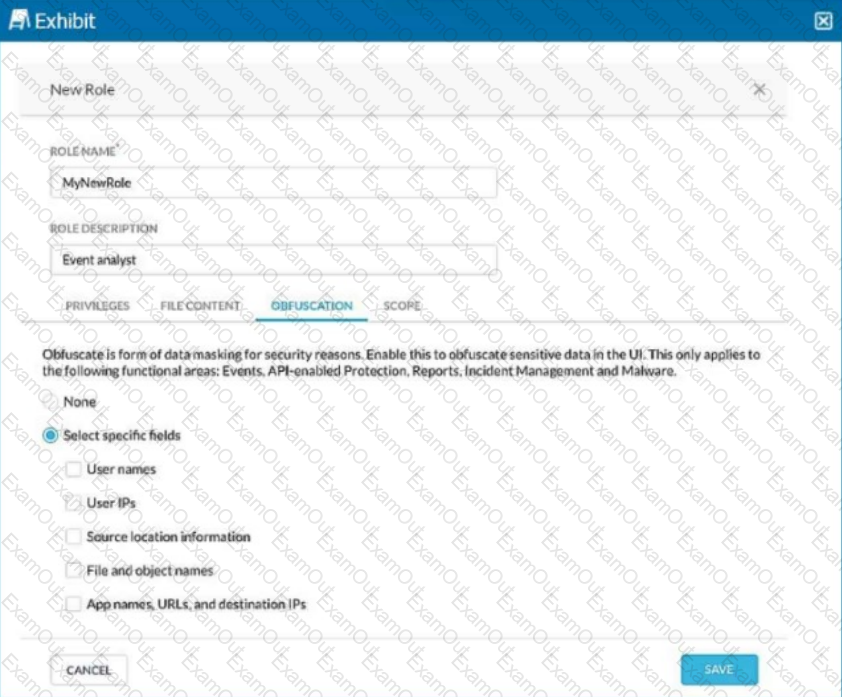
You are asked to create a new role that allows analysts to view Events and Reports while providing user privacy. You need to avoid directly exposing identities and user location information.
Which three fields must you obfuscate in this scenario? (Choose three.)
Which statement describes how Netskope's REST API, v1 and v2, handles authentication?
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or "Access key"?
Which statement describes a requirement for deploying a Netskope Private Application (NPA) Publisher?

