The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
Your company has a Symantec BlueCoat proxy on-premises and you want to deploy Netskope using proxy chaining. Which two prerequisites need to be enabled first in this scenario? (Choose two.)
You are having issues with fetching user and group Information periodically from the domain controller and posting that information to your tenant instance in the Netskope cloud. To begin the troubleshooting process, what would you Investigate first in this situation?
Your IT organization is migrating its user directory services from Microsoft Active Directory to a cloud-based Identity Provider (IdP) solution, Azure AD. You are asked to adapt the Netskope user provisioning process to work with this new cloud-based IdP.
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling.
Using Netskope, which deployment method would be used in this scenario?
You want to allow both the user identities and groups to be imported in the Netskope platform. Which two methods would satisfy this requirement? (Choose two.)
Review the exhibit.
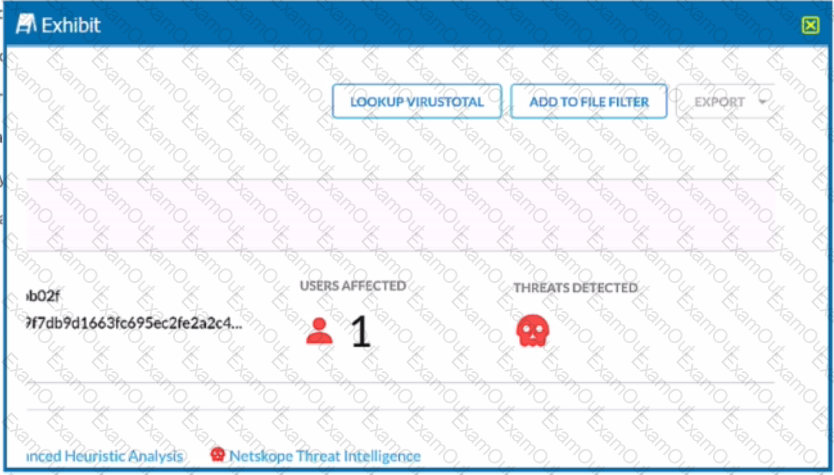
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
Review the exhibit.
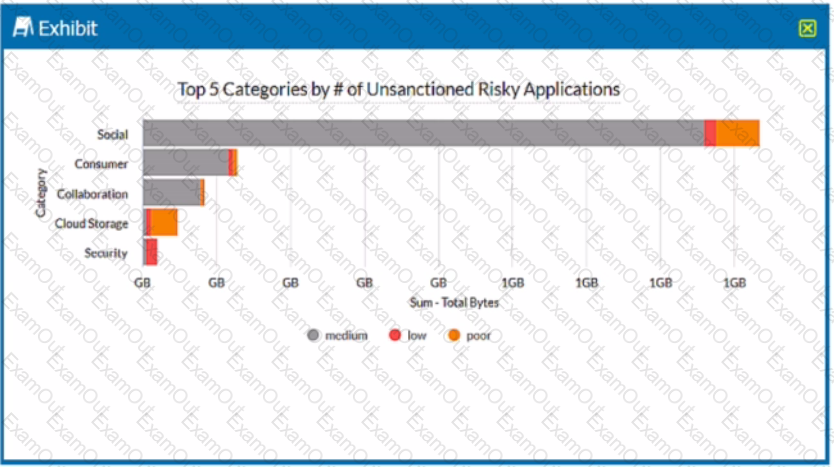
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)

