An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
You are creating an API token to allow a DevSecOps engineer to create and update a URL list using REST API v2. In this scenario, which privilege(s) do you need to create in the API token?
Review the exhibit.
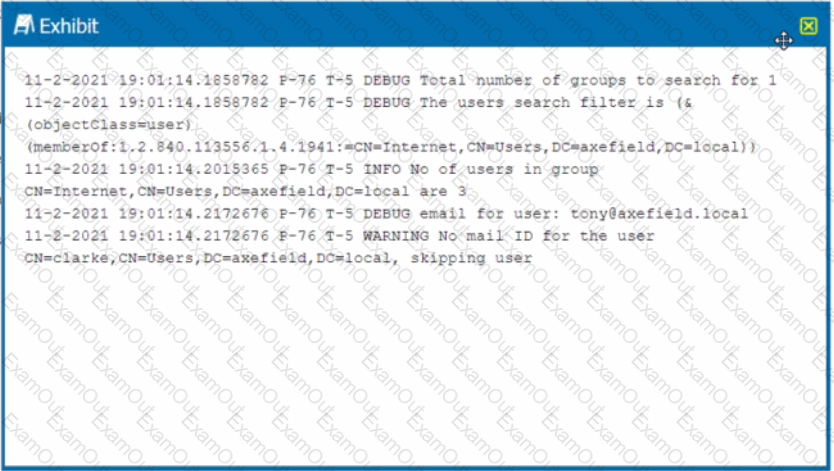
You are troubleshooting a Netskope client for user Clarke which remains in a disabled state after being installed. After looking at various logs, you notice something which might explain the problem. The exhibit is an excerpt from the nsADImporterLog.log.
Referring to the exhibit, what is the problem?
You want to secure Microsoft Exchange and Gmail SMTP traffic for DLP using Netskope. Which statement is true about this scenario when using the Netskope client?
Review the exhibit.
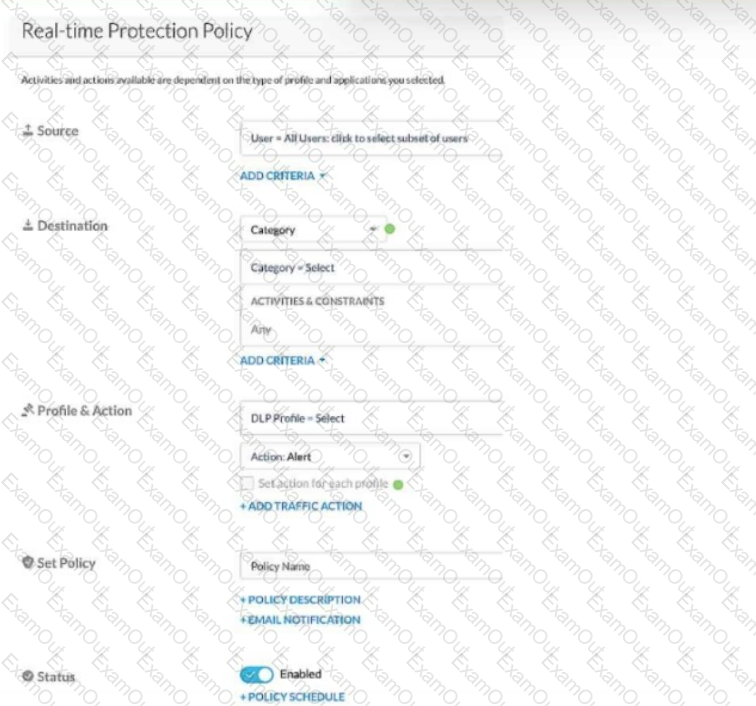
Given the information shown below:
-for PCI data uploads, you want to provide no notification,
-for PHI data uploads, you want to allow users to proceed by clicking OK,
-for GDPR data uploads, you want to provide block notification,
-if none of the above matches, you want to provide no notification.
You want to reduce the number of policies by combining multiple DLP profiles Into one policy.
Referring to the exhibit, which two statements are true? (Choose two.)
You are comparing the behavior of Netskope's Real-time Protection policies to API Data Protection policies. In this Instance, which statement is correct?
Review the exhibit.
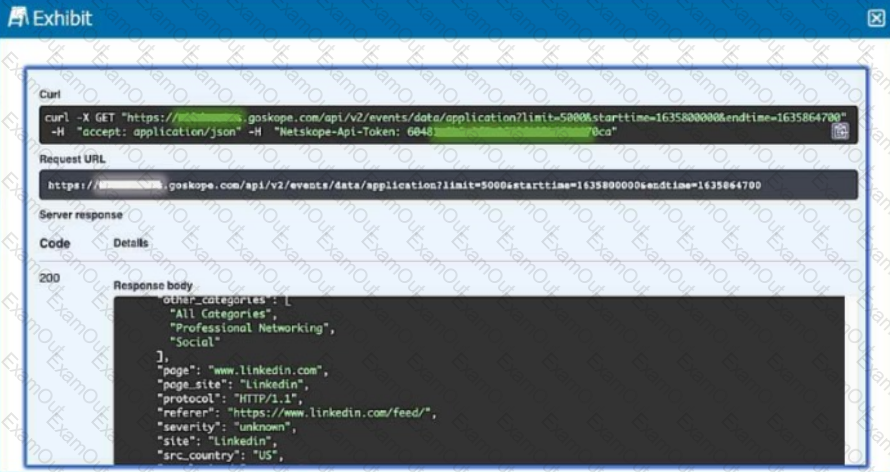
Referring to the exhibit, which three statements are correct? (Choose three.)

