You have an Azure subscription that uses Microsoft Defender XDR.
From the Microsoft Defender portal, you perform an audit search and export the results as a file named Filel.csv that contains 10,000 rows.
You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from Filel.csv. The operations fail to generate columns for specific JSON properties.
You need to ensure that Excel generates columns for the specific JSON properties in the audit search results.
Solution: From Excel, you apply filters to the existing columns in Filel.csv to reduce the number of rows, and then you perform the Get & Transform Data operations to parse the AuditData column.
Does this meet the requirement?
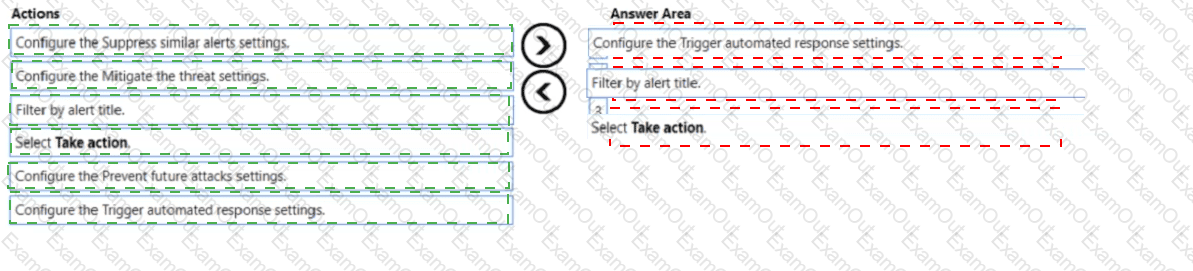
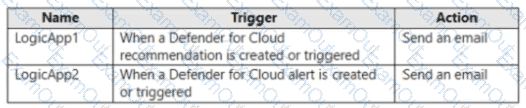
You have a Microsoft subscription that has Microsoft Defender for Cloud enabled You configure the Azure logic apps shown in the following table.
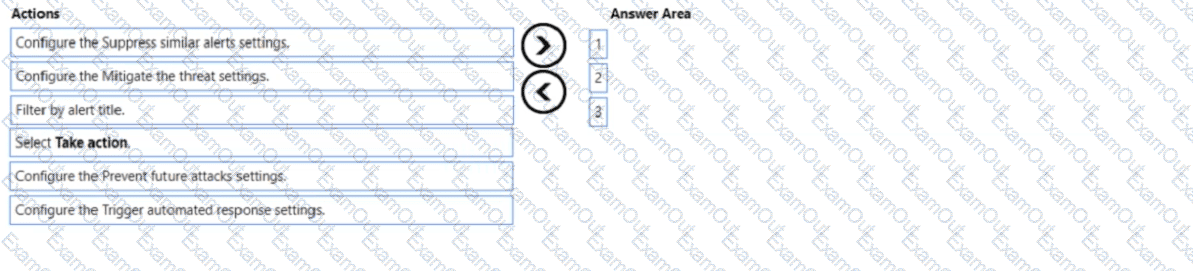
You need to configure an automatic action that will run if a Suspicious process executed alert is triggered. The solution must minimize administrative effort.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 subscription.
You have 1,000 Windows devices that have a third-party antivirus product installed and Microsoft Defender Antivirus in passive mode.
You need to ensure that the devices are protected from malicious artifacts that were undetected by the third -party antivirus product.
Solution: You configure endpoint detection and response (EDR) in block mode.
Does this meet the goal?
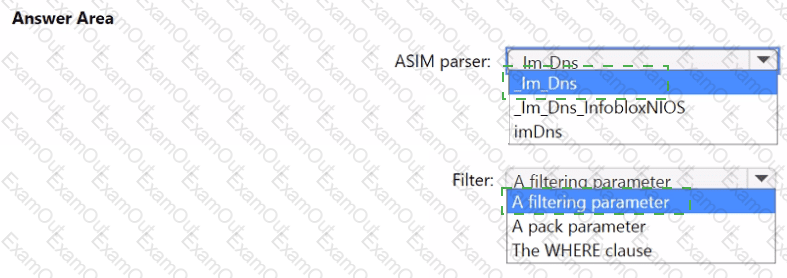
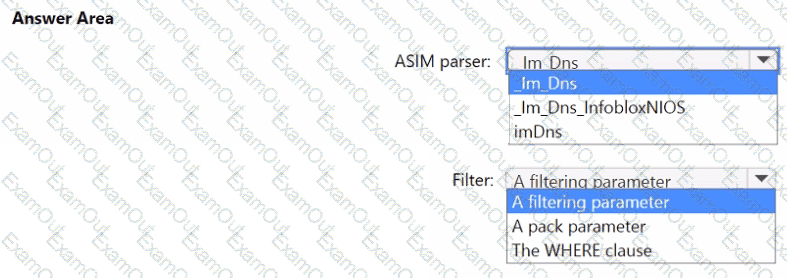
You need to implement the ASIM query for DNS requests. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
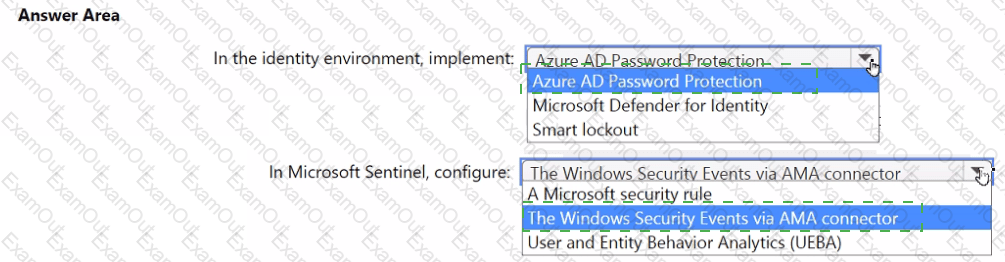
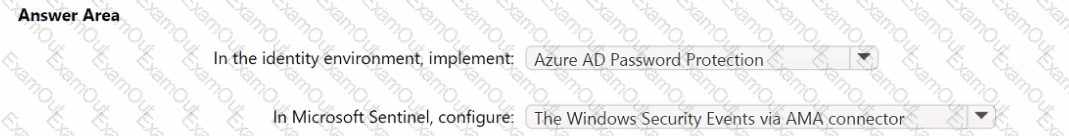
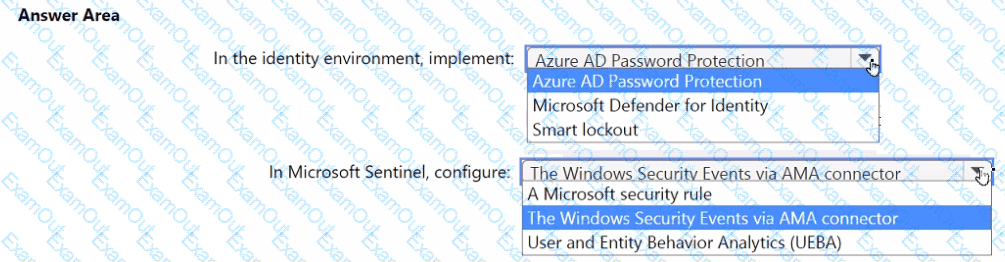
You need to monitor the password resets. The solution must meet the Microsoft Sentinel requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
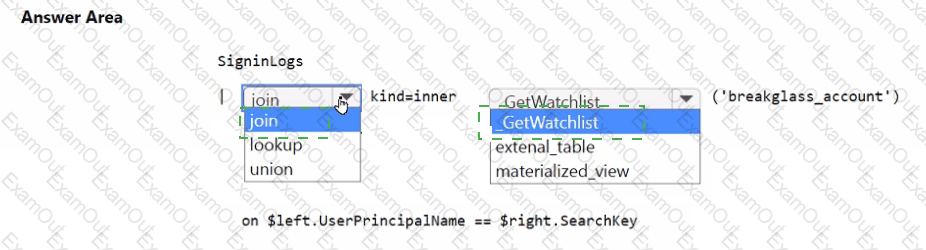
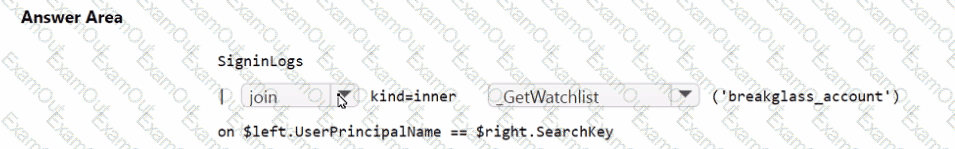
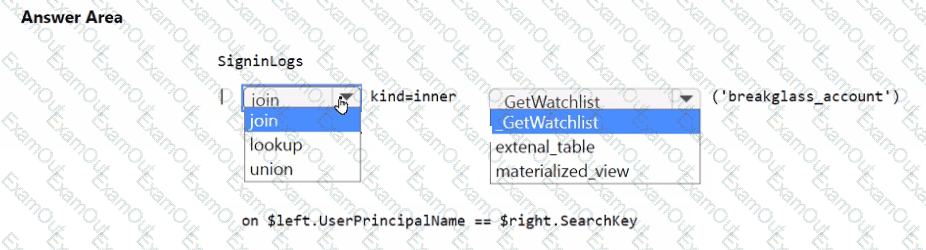
You need to implement the Microsoft Sentinel NRT rule for monitoring the designated break glass account. The solution must meet the Microsoft Sentinel requirements.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that the processing of incidents generated by rulequery1 meets the Microsoft Sentinel requirements.
What should you create first?
You need to implement the scheduled rule for incident generation based on rulequery1.
What should you configure first?
You need to implement the Defender for Cloud requirements.
What should you configure for Server2?
You need to ensure that the configuration of HuntingQuery1 meets the Microsoft Sentinel requirements.
What should you do?