You need to ensure that the Group1 members can meet the Microsoft Sentinel requirements.
Which role should you assign to Group1?
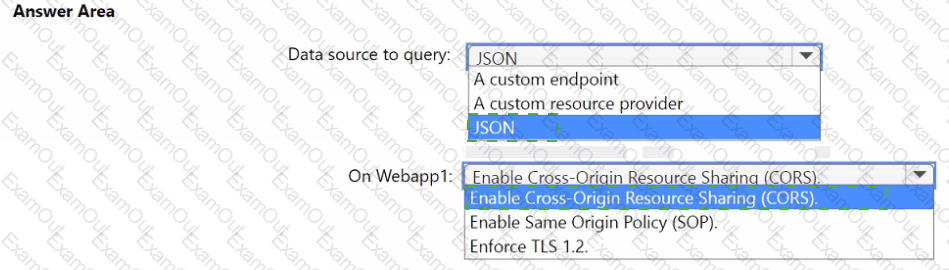
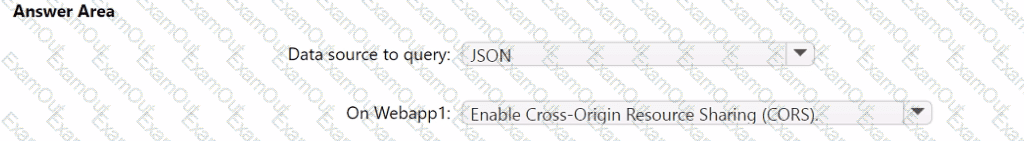
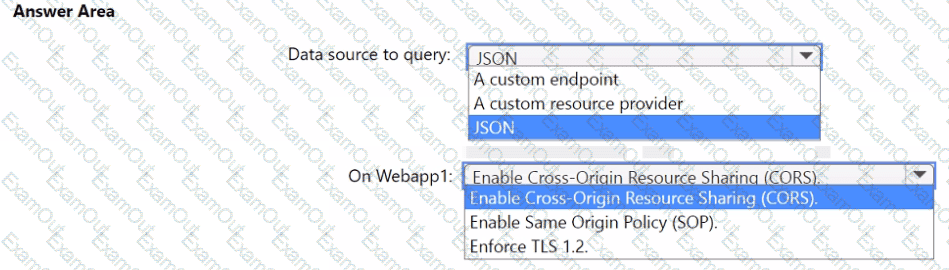
You need to implement the query for Workbook1 and Webapp1. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to implement the Defender for Cloud requirements.
Which subscription-level role should you assign to Group1?
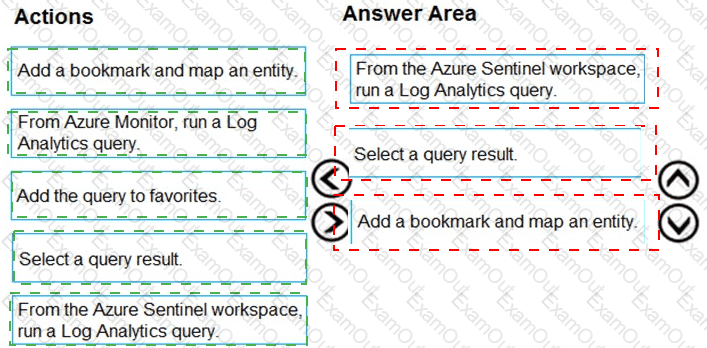
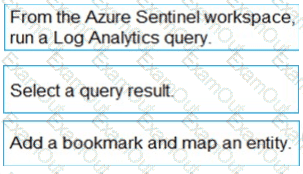
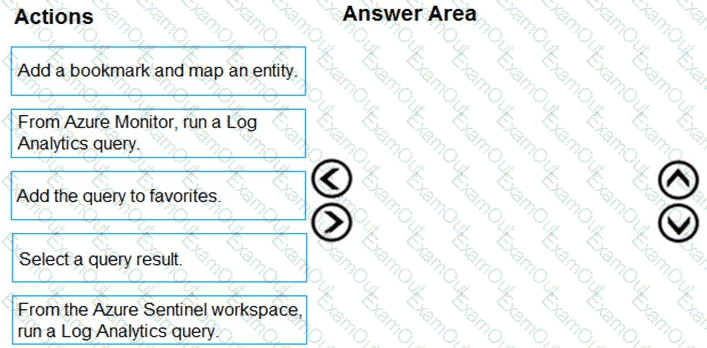
You need to add notes to the events to meet the Azure Sentinel requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
You need to configure event monitoring for Server1. The solution must meet the Microsoft Sentinel requirements. What should you create first?
You need to restrict cloud apps running on CUENT1 to meet the Microsoft Defender for Endpoint requirements. Which two configurations should you modify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
You need to restrict cloud apps running on CLIENT1 to meet the Microsoft Defender for Endpoint requirements.
Which two configurations should you modify? Each correct answer present part of the solution.
NOTE: Each correct selection is worth one point.
You need to modify the anomaly detection policy settings to meet the Microsoft Defender for Cloud Apps requirements and resolve the reported problem.
Which policy should you modify?
Which rule setting should you configure to meet the Microsoft Sentinel requirements?
You need to modify the anomaly detection policy settings to meet the Cloud App Security requirements. Which policy should you modify?