You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
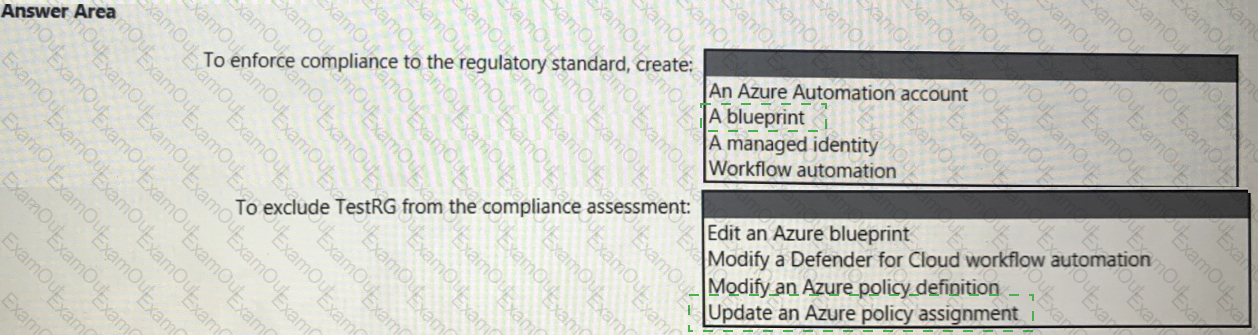
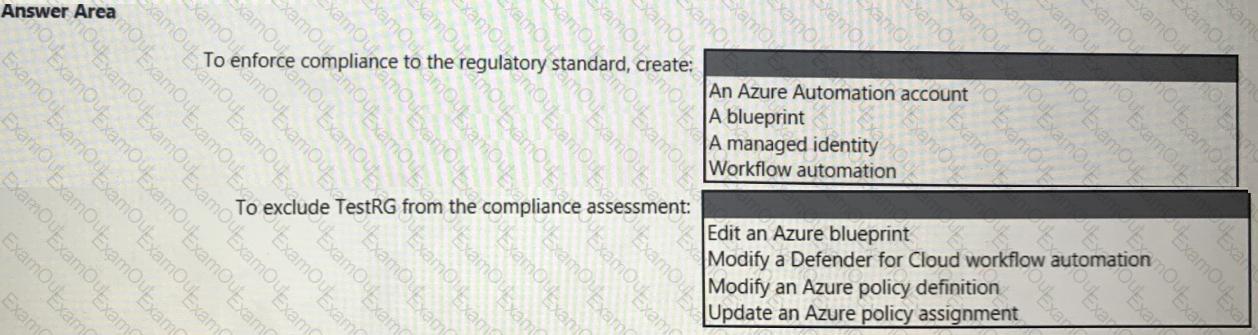
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
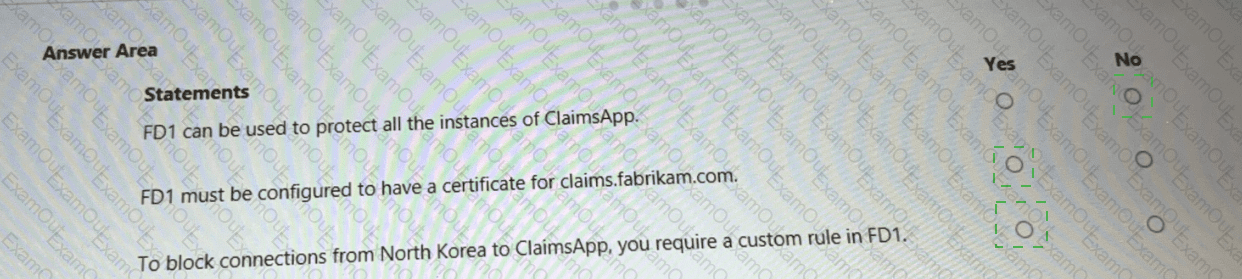
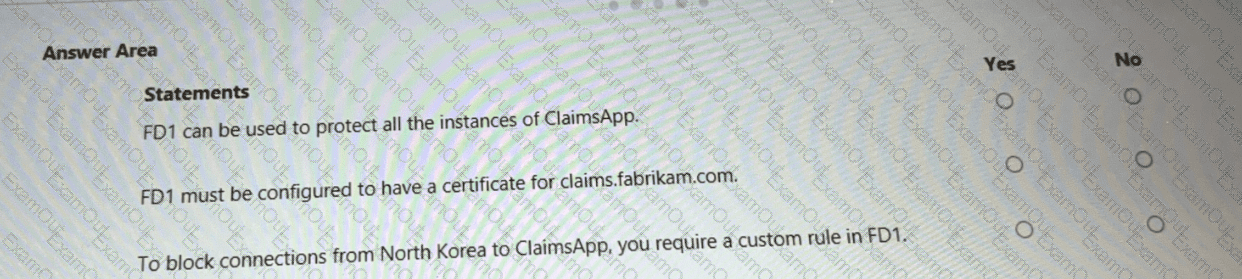
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
Your company has on-premises datacenters in Seattle, Chicago, and New York City.
You plan to migrate the on-premises workloads to the East US Azure region.
You need to design a governance solution for the management group hierarchy. The solution must be based on Microsoft Cloud Adoption Framework for Azure principles and must ensure that the hierarchy aligns with the Azure landing conceptual architecture.
What should you use to identify which archetype-aligned management groups to create beneath the landing zones management group?
You have an Azure subscription.
You have a subscription to a third-party cloud provider. The subscription contains 100 virtual machines.
You manage cloud security for both subscriptions from the Azure subscription.
You need to recommend a solution to validate the security posture of the virtual machines.
Which two services should you include in the recommendation? Each correct answer presents part of the solution.
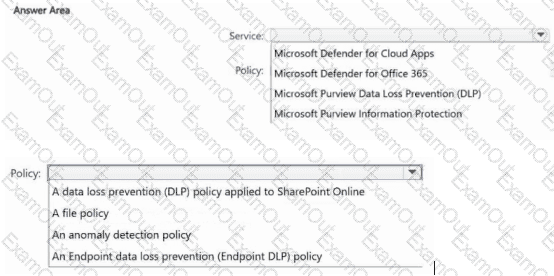
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and Microsoft Purview.
You need to recommend a data protection solution. The solution must ensure that you can identify users that download atypical amounts of data from Microsoft SharePoint Online.
Which service should you include in the recommendation, and which policy should be configured? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses Microsoft-managed keys.
Does this meet the goal?
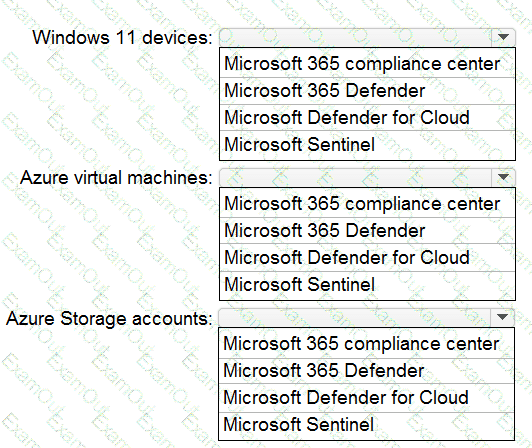
You have a Microsoft 365 E5 subscription and an Azure subscripts You need to evaluate the existing environment to increase the overall security posture for the following components:
• Windows 11 devices managed by Microsoft Intune
• Azure Storage accounts
• Azure virtual machines
What should you use to evaluate the components? To answer, select the appropriate options in the answer area.
You have a Microsoft 365 subscription. You have an Azure subscription.
You need to implement a Microsoft Purview communication compliance solution for Microsoft Teams and Yammer. The solution must meet the following requirements:
• Assign compliance policies to Microsoft 365 groups based on custom Microsoft Exchange Online attributes.
• Minimize the number of compliance policies
• Minimize administrative effort
What should you include in the solution?
Your company has two offices named Office1 and Office2. The offices contain 1,000 on-premises Windows 11 devices that are Microsoft Entra joined.
You have a Microsoft 365 subscription and use Microsoft Intune.
You plan to deploy Microsoft Entra Internet Access from the offices to Microsoft 365.
You enable the Microsoft 365 profile and configure the following:
• A traffic policy for all Microsoft 365 traffic
• A linked Conditional Access policy that has the following configurations:
° Applies to all users
° Performs compliant network checks
o Allows Microsoft 365 traffic from compliant devices
• An assignment to all devices
• An assignment to the remote network associated with Office1
You deploy the Global Secure Access client to all the devices in Office2 and establish connections.
Which users can access Microsoft 365 services from compliant devices, and which users are blocket1 from accessing Microsoft 365 services when using noncompliar devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.