You have an Azure subscription that contains the resources shown in the following table.
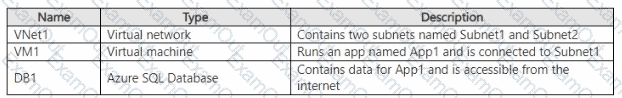
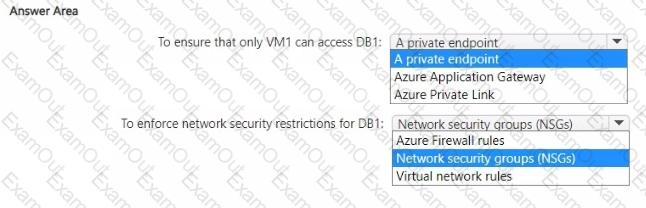
You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Only the virtual machines that are connected to Subnet1 must be able to connect to D81.
• DB1 must be inaccessible from the internet
• Costs must be minimized.
What should you include in the recommendation? To answer, select the options in the answer area. NOTE: Each correct answer is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
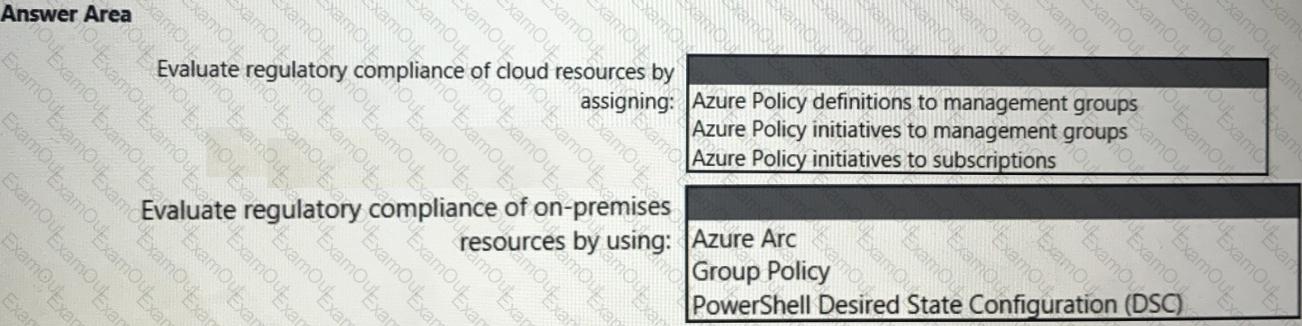
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
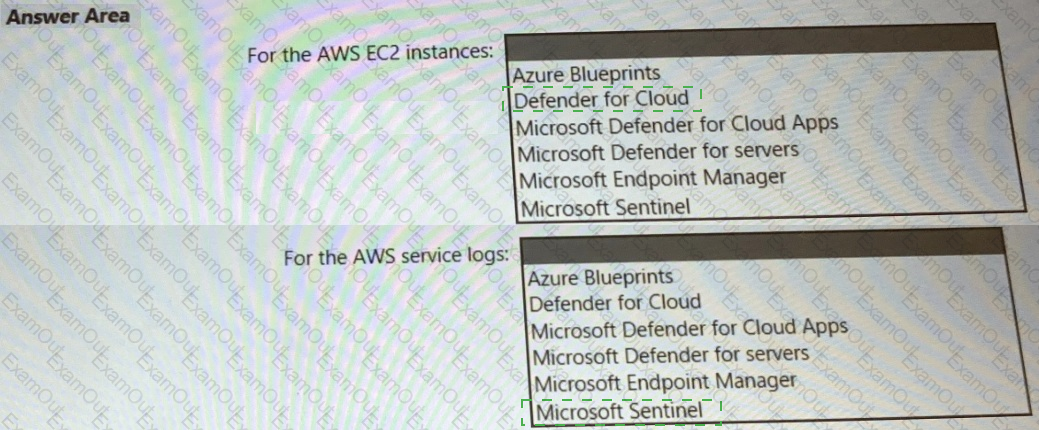
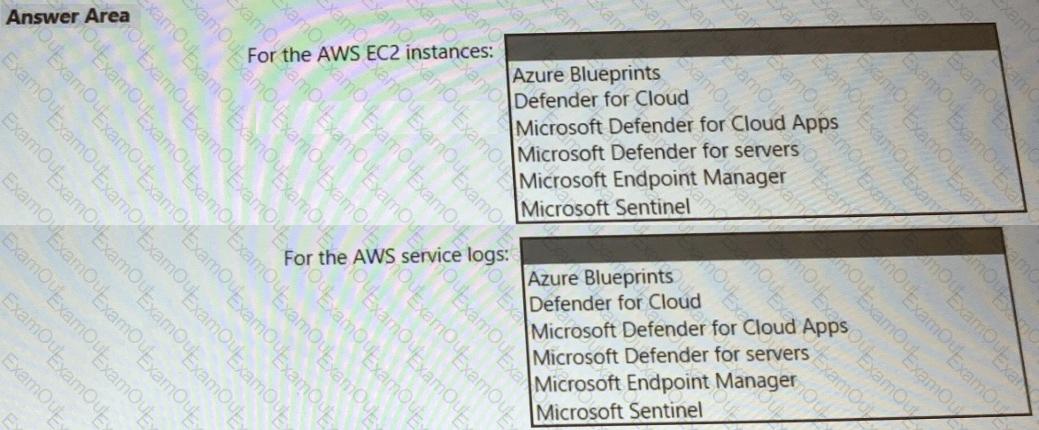
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
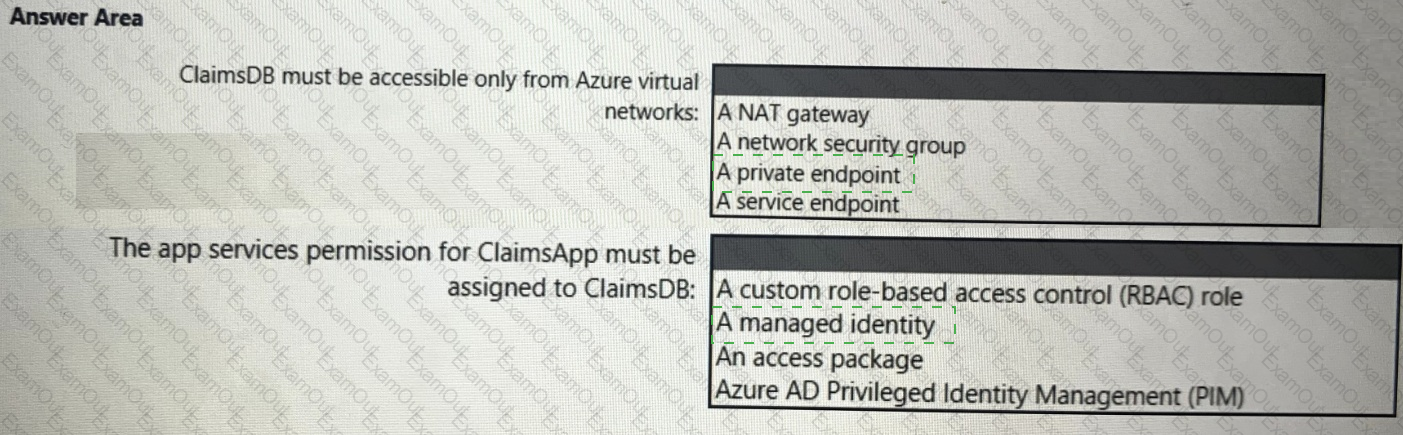
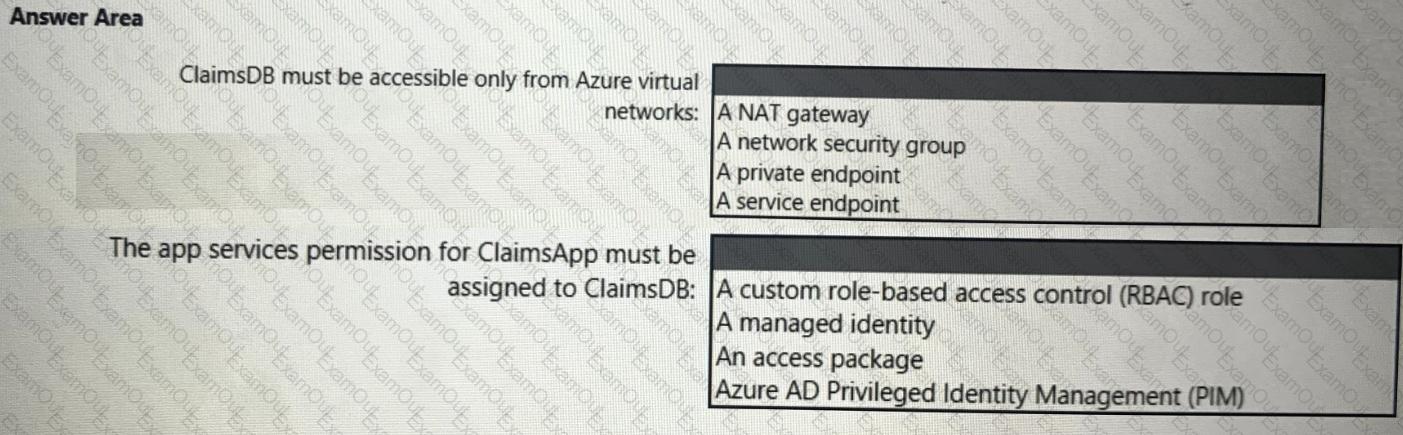
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
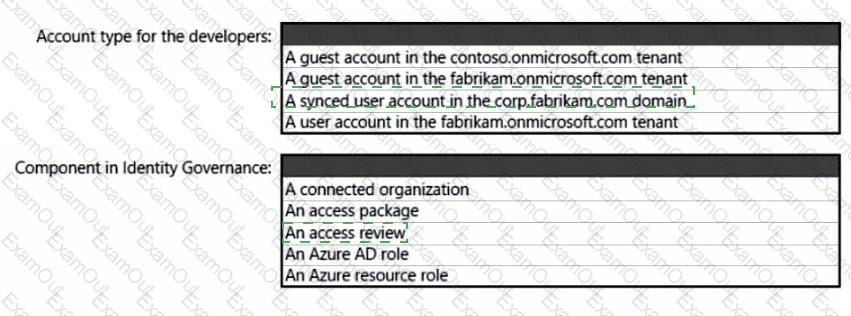
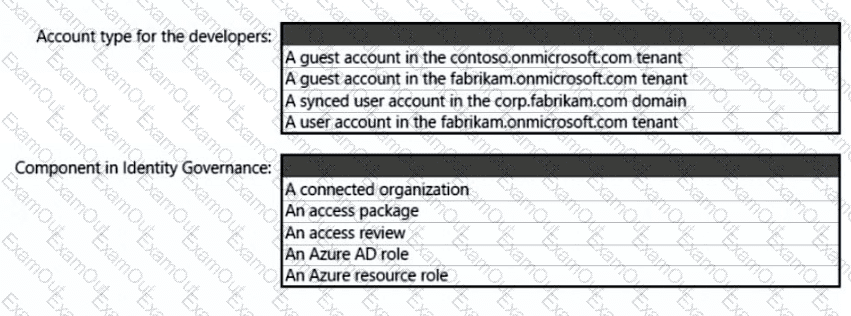
What should you create in Azure AD to meet the Contoso developer requirements?
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?