You have an on-premises network and a Microsoft 365 subscription.
You are designing a Zero Trust security strategy.
Which two security controls should you include as part of the Zero Trust solution? Each correct answer part of the solution.
NOTE: Each correct answer is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling the VMAccess extension on all virtual machines.
Does this meet the goal?
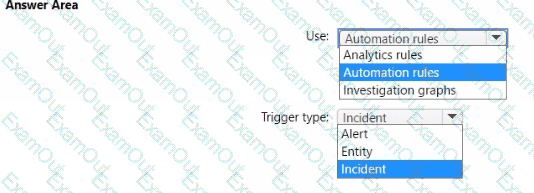
You have an Azure subscription that contains a Microsoft Sentinel workspace named MSW1. MSW1 includes 50 scheduled analytics rules.
You need to design a security orchestration automated response (SOAR) solution by using Microsoft Sentinel playbooks. The solution must meet the following requirements:
• Ensure that expiration dates can be configured when a playbook runs.
• Minimize the administrative effort required to configure individual analytics rules.
What should you use to invoke the playbooks, and which type of Microsoft Sentinel trigger should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have legacy operational technology (OT) devices and loT devices.
You need to recommend best practices for applying Zero Trust principles to the OT and loT devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The solution must minimize the risk of disrupting business operations.
Which two security methodologies should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point


