Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:-
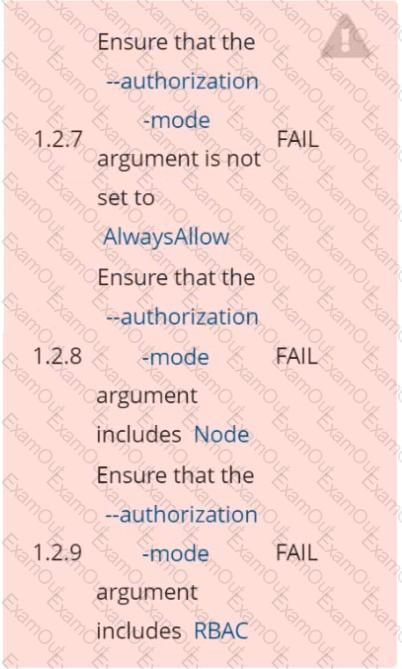
a. Ensure the --authorization-mode argument includes RBAC
b. Ensure the --authorization-mode argument includes Node
c. Ensure that the --profiling argument is set to false
Fix all of the following violations that were found against the Kubelet:-
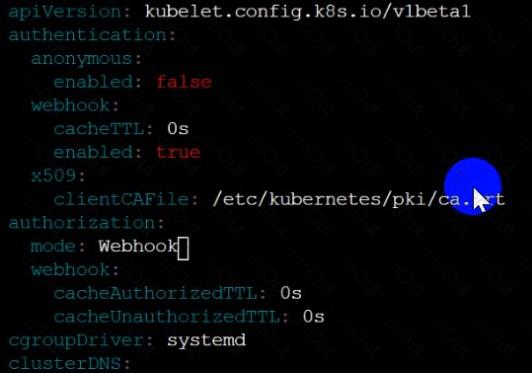
a. Ensure the --anonymous-auth argument is set to false.
b. Ensure that the --authorization-mode argument is set to Webhook.
Fix all of the following violations that were found against the ETCD:-
a. Ensure that the --auto-tls argument is not set to true
Hint: Take the use of Tool Kube-Bench
Documentation Secrets, TLS Secrets, Volumes
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000m40
Path
Key
Context
You must complete securing access to a web server using SSL files stored in a TLS Secret .
Task
Create a TLS Secret named clever-cactus in the clever-cactus namespace for an existing Deployment named clever-cactus.
Use the following SSL files:
File
Certificate /home/candidate/clever-cactus/web.k8s.local.crt
/home/candidate/clever-cactus/web.k8s.local.key
The Deployment is already configured to use the TLS Secret.
Do not modify the existing Deployment.
Failure to do so may result in a reduced score.
Context
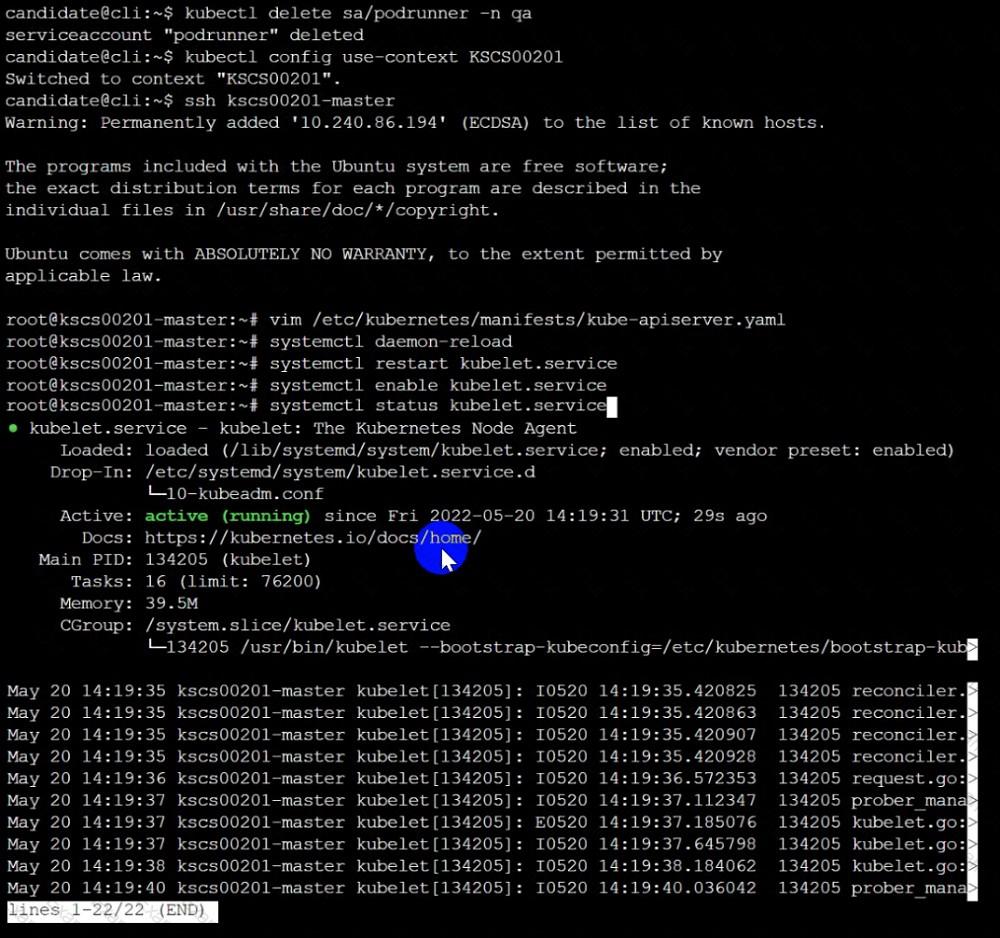
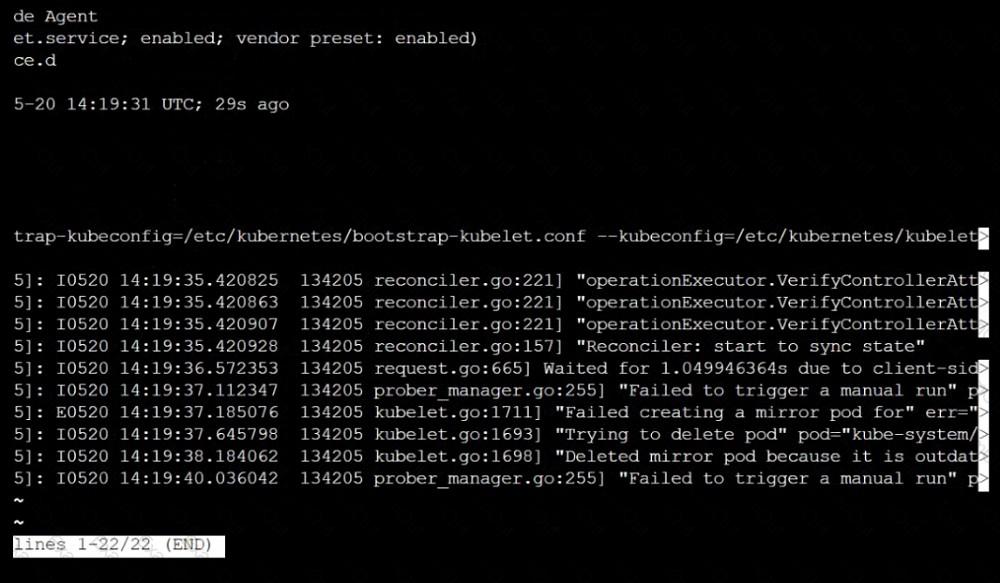
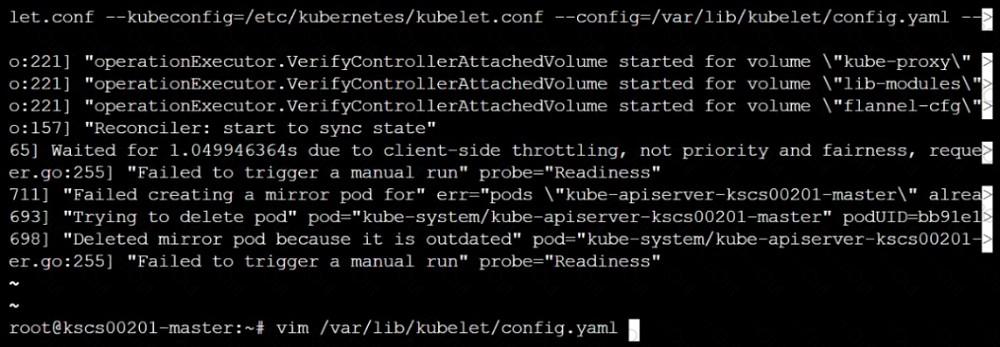
A CIS Benchmark tool was run against the kubeadm-created cluster and found multiple issues that must be addressed immediately.
Task
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
Fix all of the following violations that were found against the API server:
Fix all of the following violations that were found against the Kubelet:

Fix all of the following violations that were found against etcd:
Service is running on port 389 inside the system, find the process-id of the process, and stores the names of all the open-files inside the /candidate/KH77539/files.txt, and also delete the binary.
Context
You must resolve issues that a CIS Benchmark tool found for the kubeadm provisioned cluster.
Task
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
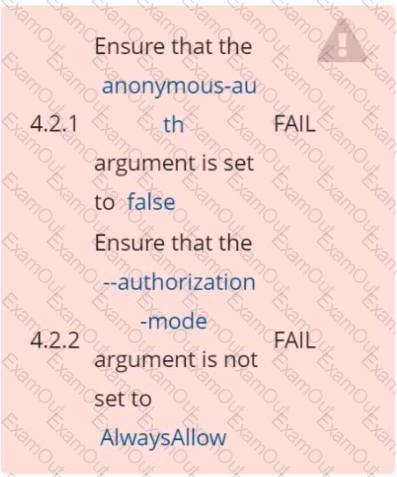
Fix all of the following violations that were found against the kubelet:
The cluster uses the Docker Engine os its container runtime, If needed, use the
docker command to troubleshaot running containers.
Ensure that the anonymous-auth argument is set to false FAIL
Ensure that the -authorization-mode argument is not set to FAIL
AlwaysAllow
Use Webhook authentication /authorization where possible.
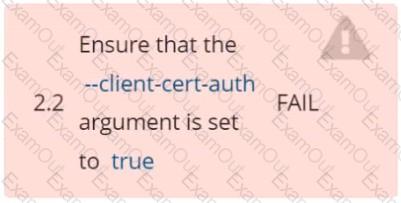
Fix all of the following violations that were found against ettd :
Ensure that the -client cert auth argument is set to true FAIL
Documentation dockerd
You must connect to the correct host . Failure to do so may result in a zero score.
[candidate@base] $ ssh cks000037
Task
Perform the following tasks to secure the cluster node cks000037 :
Remove user developer from the docker group.
Do not remove the user from any other group.
Reconfigure and restart the Docker daemon to ensure that the socket
file located at /var/run/docker.sock is owned by the group root.
Re-configure and restart the Docker daemon to ensure it does not listen on any TCP port.
After completing your work, ensure the Kubernetes cluster is healthy.
Task
Analyze and edit the given Dockerfile /home/candidate/KSSC00301/Docker file (based on the ubuntu:16.04 image), fixing two instructions present in the file that are prominent security/best-practice issues.
Analyze and edit the given manifest file /home/candidate/KSSC00301/deployment.yaml, fixing two fields present in the file that are prominent security/best-practice issues.

Context
AppArmor is enabled on the cluster's worker node. An AppArmor profile is prepared, but not enforced yet.
Task
On the cluster's worker node, enforce the prepared AppArmor profile located at /etc/apparmor.d/nginx_apparmor.
Edit the prepared manifest file located at /home/candidate/KSSH00401/nginx-pod.yaml to apply the AppArmor profile.
Finally, apply the manifest file and create the Pod specified in it.
You must connect to the correct host . Failure to do so may
result in a zero score.
[candidato@base] $ ssh cks000023
Task
Analyze and edit the Dockerfile located at /home/candidate/subtle-bee/build/Dockerfile, fixing one instruction present in the file that is a prominent security/best-practice issue.
Do not add or remove instructions; only modify the one existing instruction with a security/best-practice concern.
Do not build the Dockerfile, Failure to do so may result in running out of storage and a zero score.
Analyze and edit the given manifest file /home/candidate/subtle-bee/deployment.yaml, fixing one fields present in the file that are a prominent security/best-practice issue.
Do not add or remove fields; only modify the one existing field with a security/best-practice concern.
Should you need an unprivileged user for any of the tasks, use user nobody with user ID 65535.
Enable audit logs in the cluster, To Do so, enable the log backend, and ensure that
1. logs are stored at /var/log/kubernetes/kubernetes-logs.txt.
2. Log files are retained for 5 days.
3. at maximum, a number of 10 old audit logs files are retained.
Edit and extend the basic policy to log:
1. Cronjobs changes at RequestResponse
2. Log the request body of deployments changes in the namespace kube-system.
3. Log all other resources in core and extensions at the Request level.
4. Don't log watch requests by the "system:kube-proxy" on endpoints or