The Require directive in mod_authz_core selects which authenticated users can access a resource. The directive takes one or more arguments that specify the authorization provider and the criteria for granting access. Some of the built-in authorization providers are:
all: This provider matches all users, regardless of the criteria. It can be used to grant or deny access to everyone. For example, Require all granted allows access to everyone, while Require all denied denies access to everyone.
ip: This provider matches the client IP address against a list of IP addresses, network/netmask pairs, or CIDR specifications. It can be used to allow or deny access based on the client’s location. For example, Require ip 192.168.1.0/24 allows access only to clients from the 192.168.1.0/24 subnet.
host: This provider matches the client hostname against a list of domain names. It can be used to allow or deny access based on the client’s DNS name. For example, Require host example.com allows access only to clients whose hostname ends with example.com.
local: This provider matches the client IP address against the server IP address. It can be used to allow or deny access based on whether the client is local or remote. For example, Require local allows access only to clients that connect to the server via the loopback interface.
user: This provider matches the authenticated username against a list of usernames. It can be used to allow or deny access based on the user identity. For example, Require user alice bob allows access only to users alice and bob.
group: This provider matches the authenticated user’s group membership against a list of groups. It can be used to allow or deny access based on the user’s group affiliation. For example, Require group admins allows access only to users who belong to the admins group.
valid-user: This provider matches any authenticated user, regardless of the username. It can be used to allow or deny access based on the user authentication status. For example, Require valid-user allows access to any user who can provide valid credentials.
expr: This provider evaluates an expression and grants or denies access based on the result. It can be used to implement complex logic based on various variables and functions. For example, Require expr "%{REQUEST_METHOD} == 'GET' && %{TIME_HOUR} < 12" allows access only to GET requests made before noon.
method: This provider matches the request method against a list of methods. It can be used to allow or deny access based on the type of request. For example, Require method GET POST allows access only to GET and POST requests.
regex: This provider matches the request URI against a regular expression. It can be used to allow or deny access based on the pattern of the request. For example, Require regex ^/admin/.* allows access only to requests that start with /admin/.
Therefore, the correct strings that can be used as an argument to Require are B, C, and E. Statement A is false because method is not a valid argument to Require, but a separate authorization provider. Statement D is false because header is not a valid argument to Require, but a variable that can be used in an expression.
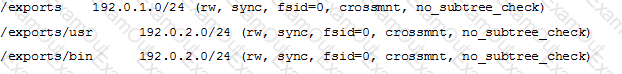

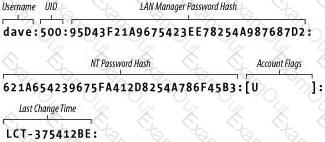 Chapter 9. Users and Security - Samba3
Chapter 9. Users and Security - Samba3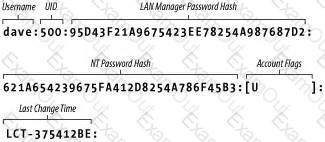 Chapter 9. Users and Security - Samba
Chapter 9. Users and Security - Samba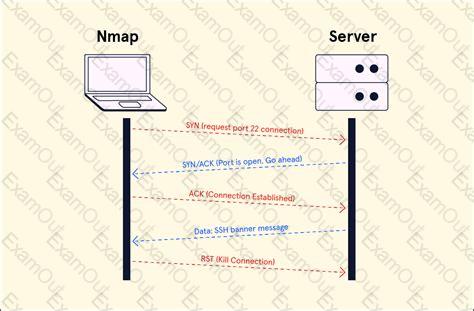 Cybersecurity | Nmap | TCP Connect Scan | Codecademy
Cybersecurity | Nmap | TCP Connect Scan | Codecademy