In an effort to reduce client-server latency transparent mode was enabled an SRX series device.
Which two types of traffic will be permitted in this scenario? (Choose Two )
Which three type of peer devices are supported for Cos-Based IPsec VPN?
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
While troubleshooting security policies, you added the count action. Where do you see the result of this action?
Exhibit
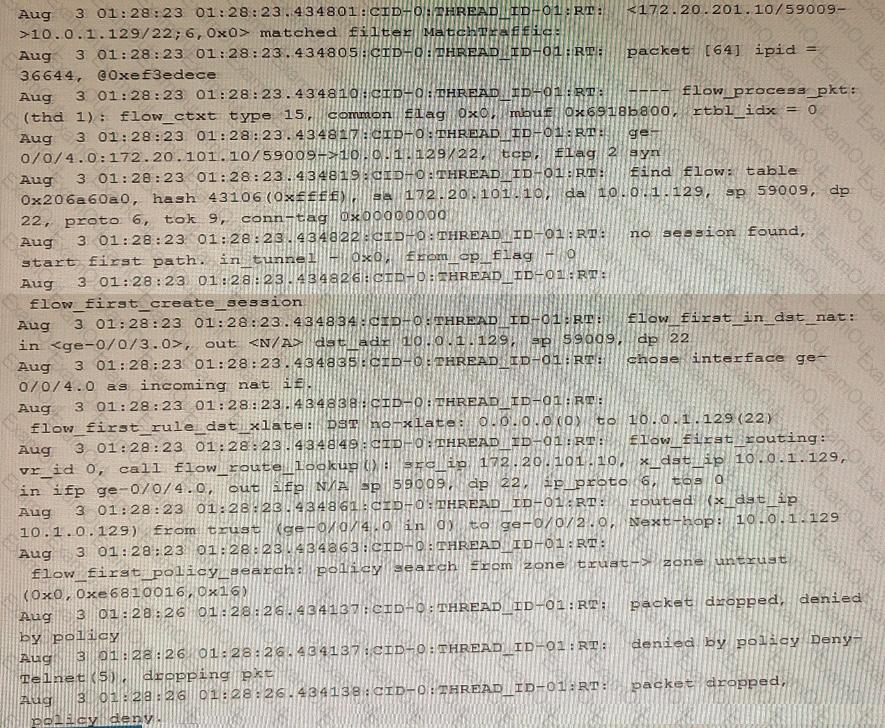
Which two statements are correct about the output shown in the exhibit. (Choose two.)
Which two features would be used for DNS doctoring on an SRX Series firewall? (Choose two.)
You must implement an IPsec VPN on an SRX Series device using PKI certificates for authentication. As part of the implementation, you are required to ensure that the certificate submission, renewal, and retrieval processes are handled
automatically from the certificate authority.
In this scenario, which statement is correct.
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request? (Choose three.)
Which statement is true about persistent NAT types?
which two statements about the configuration shown in the exhibit are correct ?
Exhibit:


