Exhibit
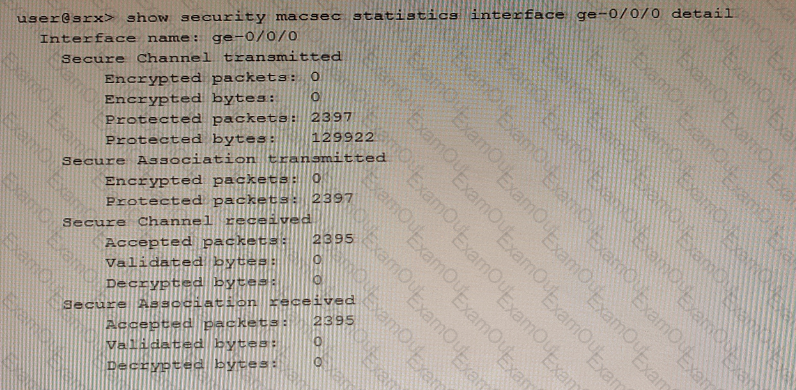
Referring to the exhibit, which two statements are true? (Choose two.)
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
You want traffic to avoid the flow daemon for administrative task.
In this scenario which two stateless service are available with selective stateless packet based service. (Choose Two)
Exhibit

You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
Exhibit
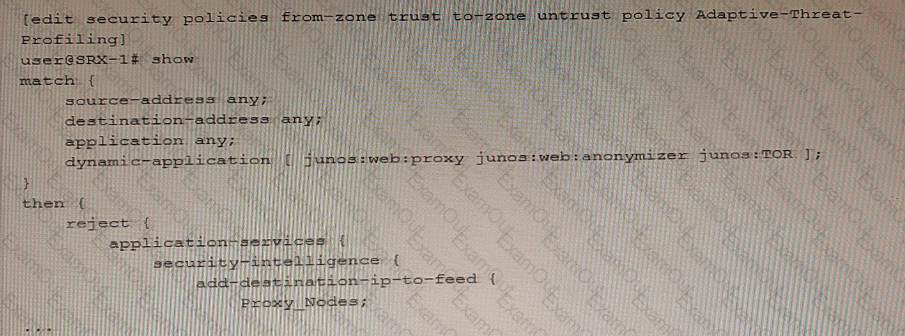
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit
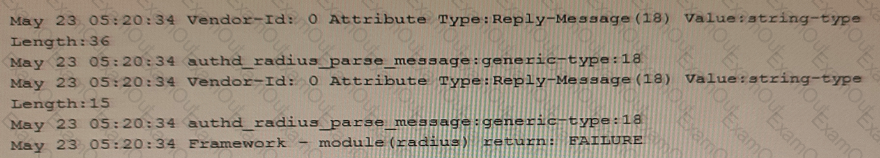
You configure a traceoptions file called radius on your returns the output shown in the exhibit
What is the source of the problem?
You issue the command shown in the exhibit.
Which policy will be active for the identified traffic?
Exhibit:

You are troubleshooting a firewall filter shown in the exhibit that is intended to log all traffic and block
only inbound telnet traffic on interface ge-0/0/3.
How should you modify the configuration to fulfill the requirements?
your company wants to take your juniper ATP appliance into private mode. You must give them a list
of impacted features for this request.
Which two features are impacted in this scenario? (Choose two)

