Exhibit
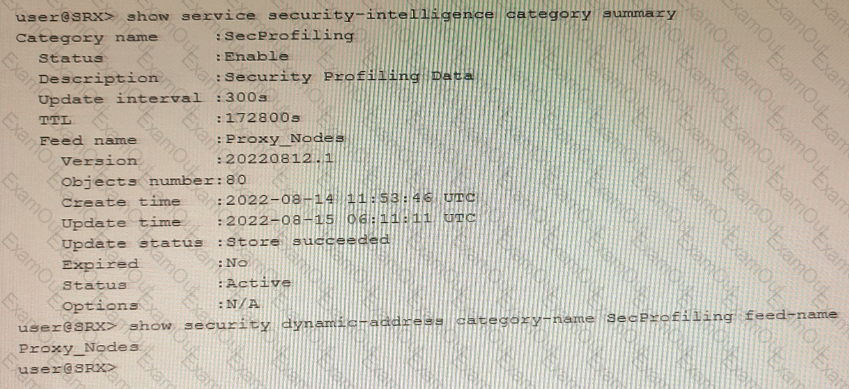
You have recently configured Adaptive Threat Profiling and notice 20 IP address entries in the monitoring section of the Juniper ATP Cloud portal that do not match the number of entries locally on the SRX Series device, as shown in the exhibit.
What is the correct action to solve this problem on the SRX device?
Exhibit:
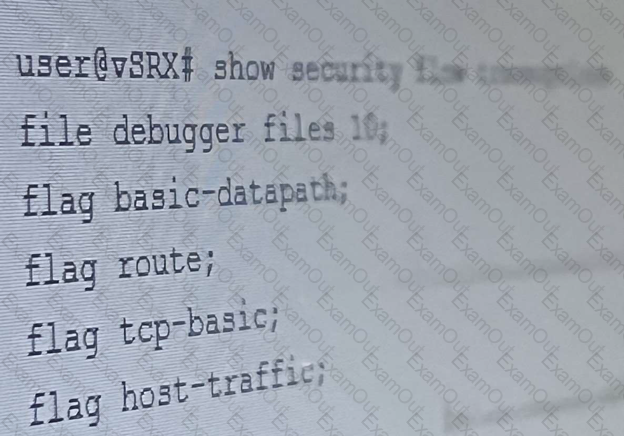
The security trace options configuration shown in the exhibit is committed to your SRX series firewall. Which two statements are correct in this Scenario? (Choose Two)
Exhibit
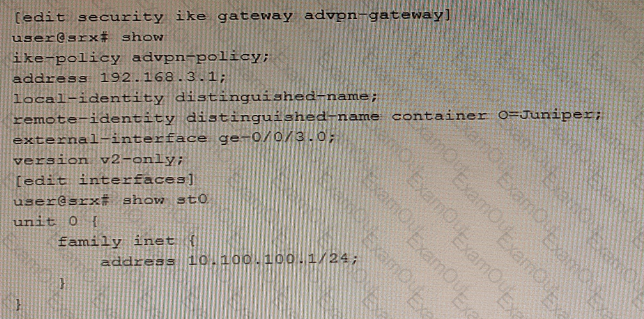
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)
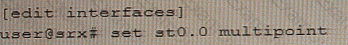
B)
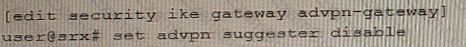
C)
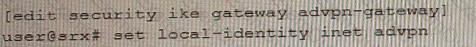
D)

You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
Exhibit
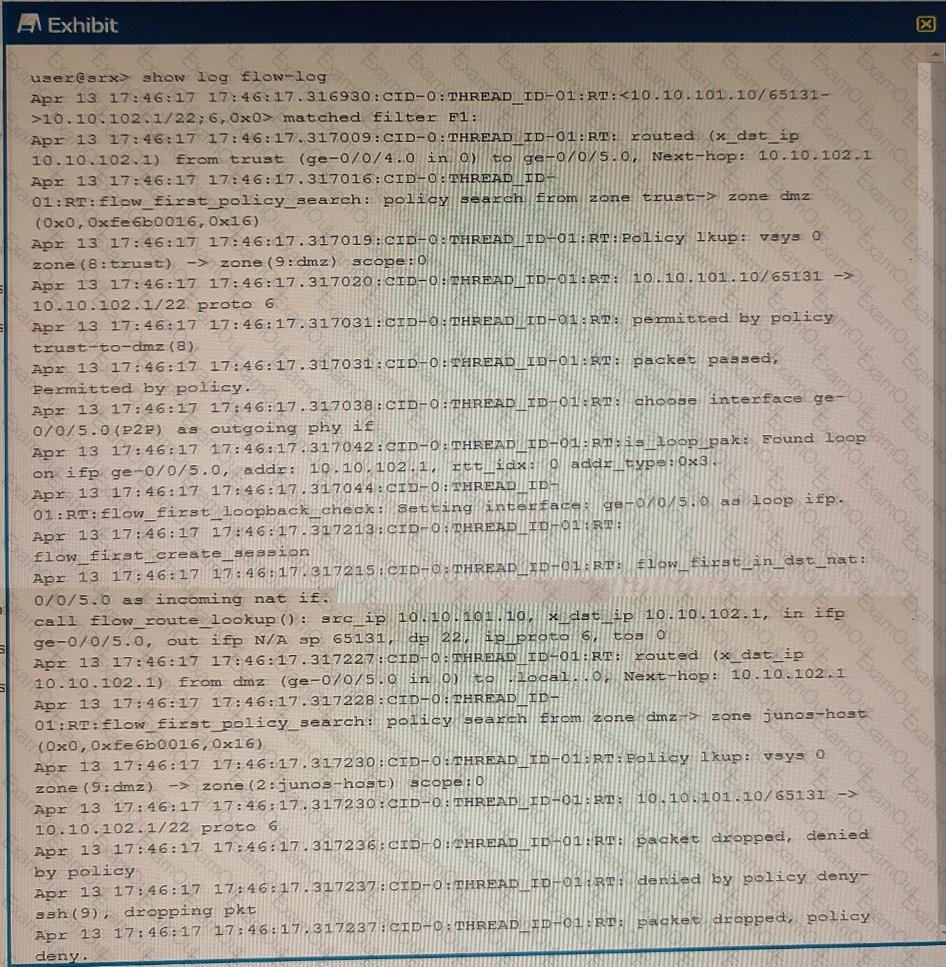
Referring to the exhibit, which three statements are true? (Choose three.)
According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
You are connecting two remote sites to your corporate headquarters site; you must ensure that all traffic is secured and
only uses a single Phase 2 SA for both sites.
In this scenario, which VPN should be used?
Which method does an SRX Series device in transparent mode use to learn about unknown devices in a network?
Which two types of source NAT translations are supported in this scenario? (Choose two.)
Exhibit
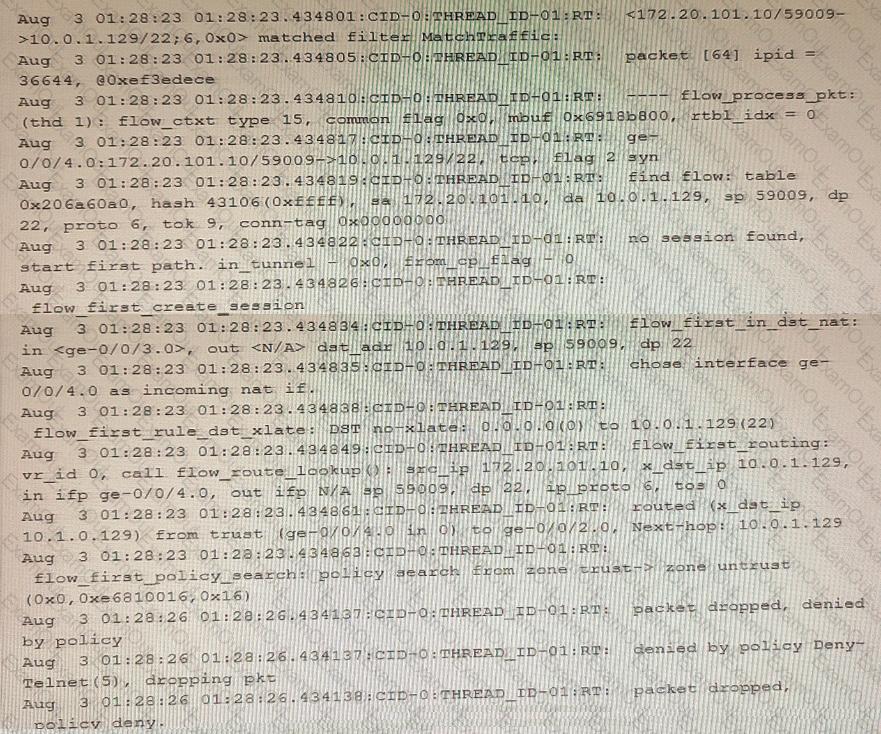
Which two statements are correct about the output shown in the exhibit? (Choose two.)

