You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
Which two statements are correct about a policy scheduler? (Choose two.)
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)
You are asked to ensure that if the session table on your SRX Series device gets close to exhausting its resources, that you enforce a more aggress.ve age-out of existing flows.
In this scenario, which two statements are correct? (Choose two.)
Which two statements are correct about a reth LAG? (Choose two.)
Which two statements about SRX chassis clustering are correct? (Choose two.)
Click the Exhibit button.
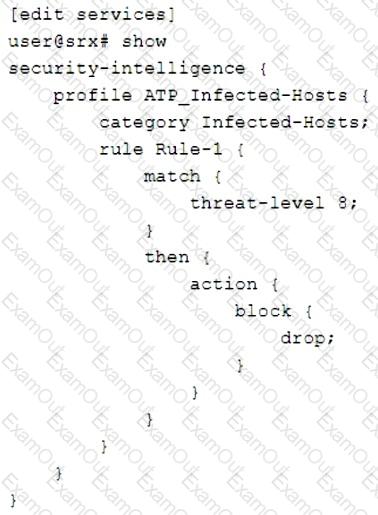
Referring to the exhibit, what will the SRX Series device do in this configuration?
You want to manually failover the primary Routing Engine in an SRX Series high availability cluster pair.
Which step is necessary to accomplish this task?
Which two statements are correct about Juniper ATP Cloud? (Choose two.)

