You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
Exhibit
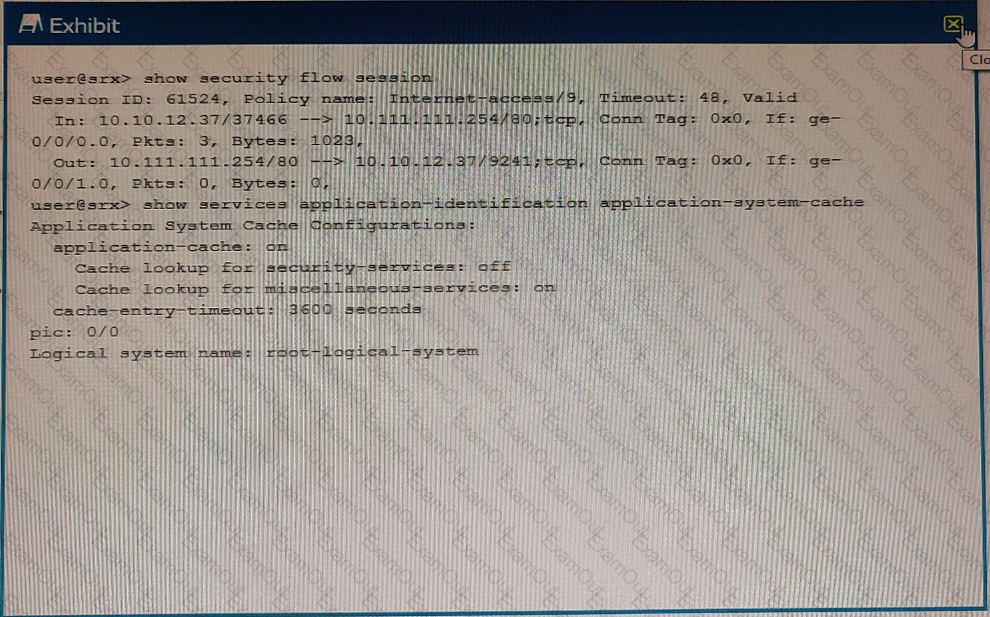
Referring to the exhibit which statement is true?
Which two statements about the DNS ALG are correct? (Choose two.)
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
You want to set up JSA to collect network traffic flows from network devices on your network.
Which two statements are correct when performing this task? (Choose two.)
Click the Exhibit button.
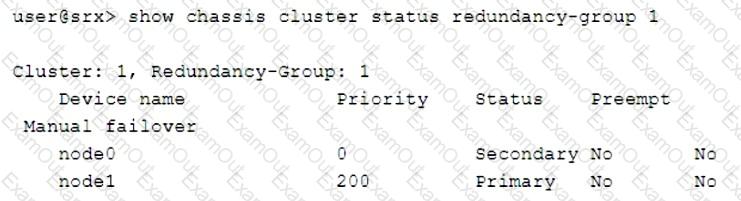
Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements about SRX Series device chassis clusters are true? (Choose two.)
Exhibit
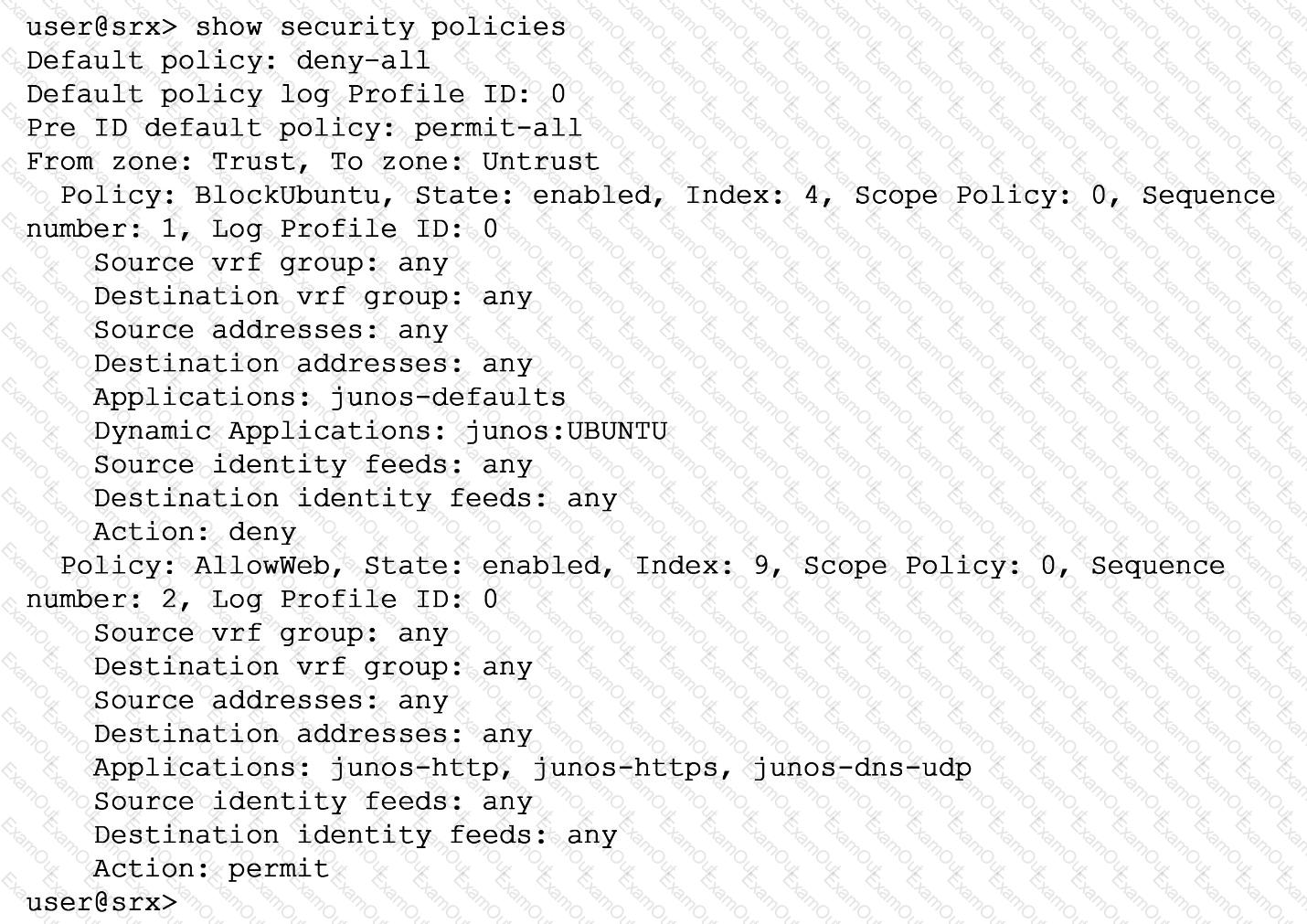
You are asked to ensure that servers running the Ubuntu OS will not be able to update automatically by blocking their access at the SRX firewall. You have configured a unified security policy named Blockuburrtu, but it is not blocking the updates to the OS.
Referring to the exhibit which statement will block the Ubuntu OS updates?
Exhibit
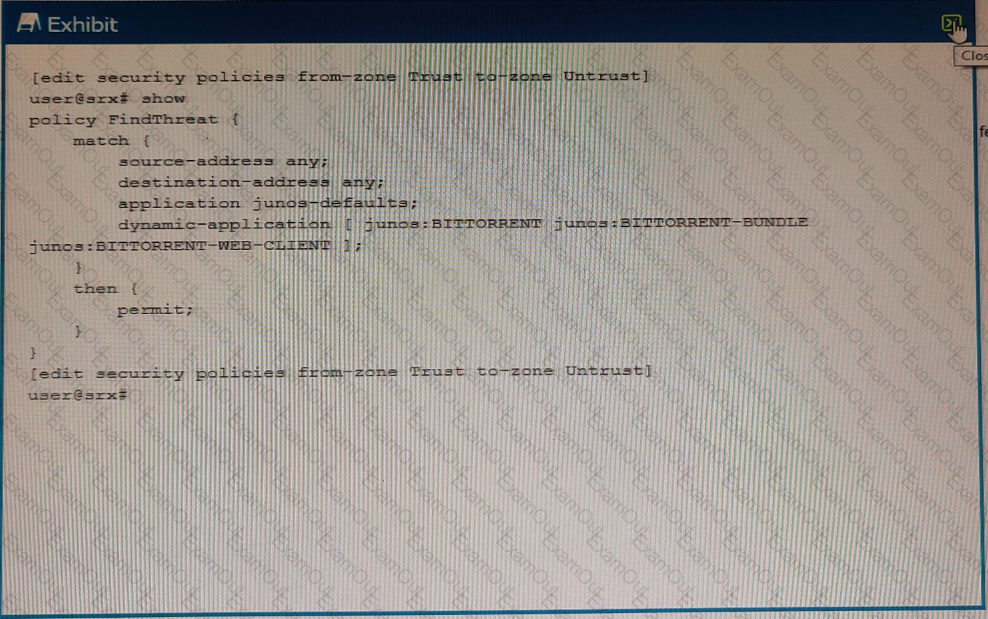
You are asked to track BitTorrent traffic on your network. You need to automatically add the workstations to the High_Risk_Workstations feed and the servers to the BitTorrent_Servers feed automatically to help mitigate future threats.
Which two commands would add this functionality to the FindThreat policy? (Choose two.)
A)
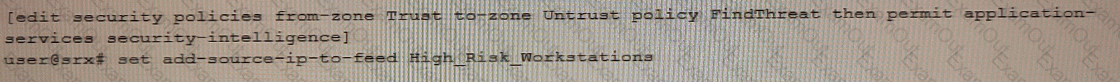
B)

C)

D)

Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)

