Which two statements are correct about JSA data collection? (Choose two.)
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
Exhibit
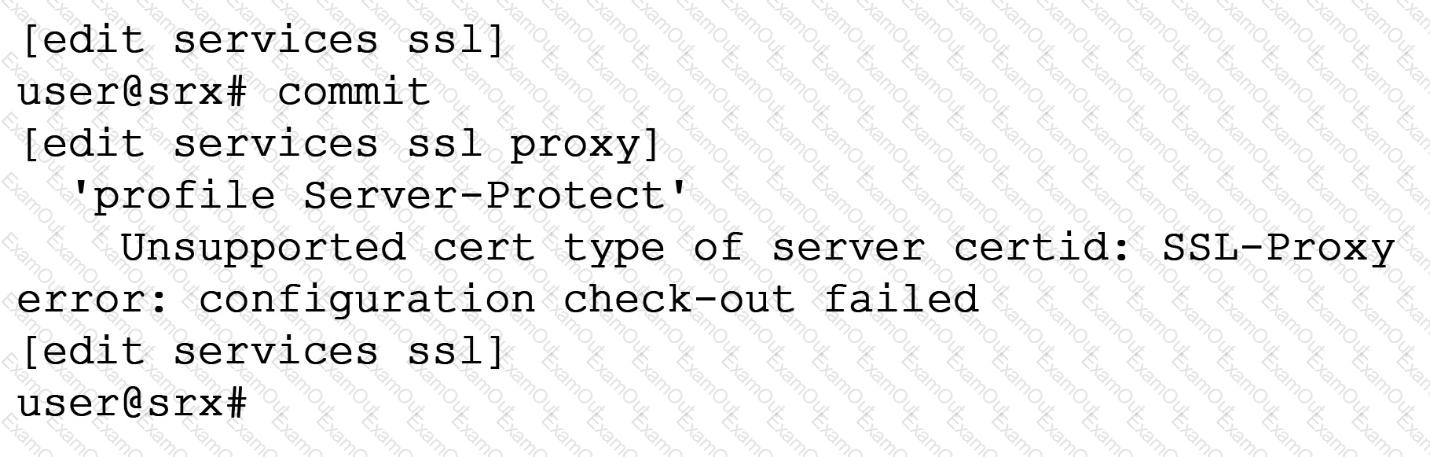
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
Which two statements are correct about SSL proxy server protection? (Choose two.)
Click the Exhibit button.
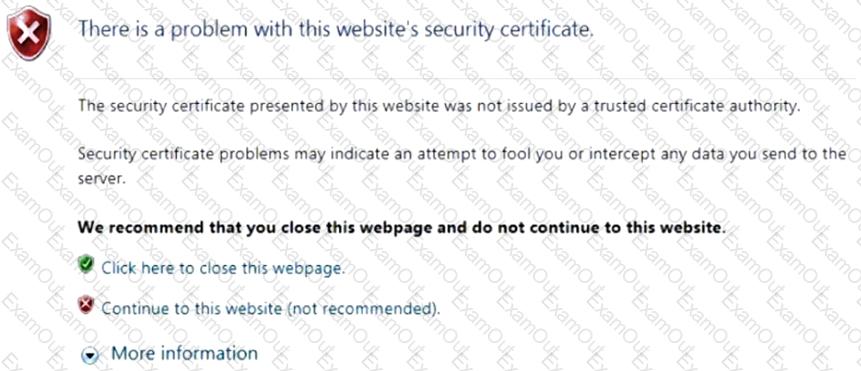
You have implemented SSL client protection proxy. Employees are receiving the error shown in the exhibit.
How do you solve this problem?
You are asked to reduce the load that the JIMS server places on your Which action should you take in this situation?

