As a technical test analyst, you are involved in a risk analysis session using the Failure Mode and Effect Analysis technique. You are calculating risk priorities. Which of the following are the major factors in this exercise?
Listed below are some possible findings from static analysis of a component containing approximately 1,000 lines of code. Which combination suggests that the component does NOT need refactoring for better maintainability?
A) Low measure of coupling.
B) Low measure of cohesion.
C) Low measure of commenting.
D) Low measure of complexity.
E) High measure of coupling.
F) High measure of cohesion.
G) High measure of commenting.
H) High measure of complexity.
Which of the following statements about Application Programming Interface (API) testing is TRUE?
You are an experienced tester on an Agile team that is producing a new application. The product backlog has been refined sufficiently to begin development for the first release. This stories in this backlog contain a mixture of functional and non-functional requirements, as well as some technical stories that will provide elements of the application's infrastructure The developers have decided to use TDD as a deveiopment approach but automation of the acceptance tests is not yet planned.
You have been asked to recommend whether or not the team should take an atdd approach as well as TDD. what would be the BEST recommendation in these circumstances?
SELECT ONE OPTION
Which statement correctly describes continuous testing’
SELECT ONE OPTION
You are working on project where re-use of software is an objective. You are involved in the project as a Technical Test Analyst and have been given the task to develop a checklist for code reviews.
Which question from the list below should you implement as part of the code review checklist?
A unit test should be isolated Which option correctly describes the meaning of 'isolated' as a characteristic of a unit test?
SELECT ONE OPTION
Whenever it is run under the same conditions, it should produce the same results.
When conducting a data flow analysis of following section of pseudo code:
Declare C, F, Z Decimal
Set Z = 32
Read F
SetC = (F-Z) * 5/9
Free C, F. Z
Print F
Which of the variables utilized above has a potential anomalie?
Consider the pseudo code for the Price program:
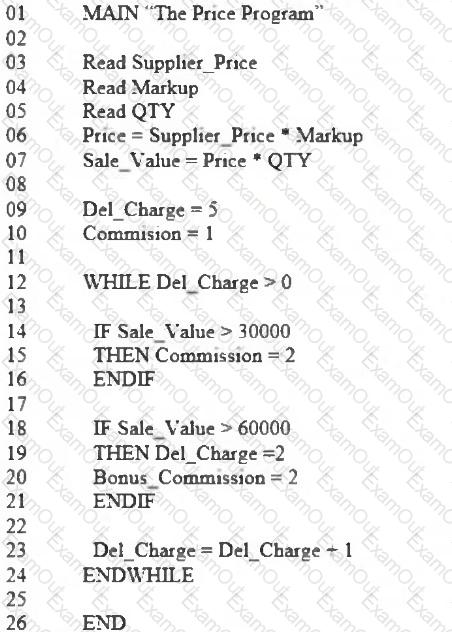
Which of the following statements about the Price program describes a control flow anomaly to be found in the program?
Which of the following elicitation techniques is BEST usedwhen questioning a large number of stakeholders specifically to obtain information for non-functional acceptance criteria?
SELECT ONE OPTION

